
Welcome to the Experian Thought Leadership Hub
Gain insights into the fast-changing world of consumer and business data through our extensive library of resources.
76 resultsPage 1
 Video
Video
How a rapidly evolving fraud landscape accelerated the need for a smarter, more modern fraud strategy.
Hear directly from Warren Jones, Head of Fraud Strategy & Analytics on:
 Webinar
Webinar
This webinar breaks down the major themes from Experian’s 2026 Future of Fraud Forecast and what they signal for the year ahead. Our experts explore the trends gaining momentum, including:
The technologies accelerating the next wave of fraud activity
Where fraudsters are finding new openings across consumer and enterprise touchpoints
The strategies forward-looking teams are prioritizing now
 Webinar
Webinar
First-party fraud can look like traditional credit risk, but the intent behind the behavior is very different. In this on-demand webinar, Experian experts show how to use early performance, identity and behavioral signals to distinguish fraud from genuine financial distress and improve portfolio outcomes.
 Infographic
Infographic
Download Experian’s 2026 Future of Fraud Forecast to explore five fraud trends expected to have the biggest impact on businesses and consumers in the coming year, including:
 Report
Report
Consumers expect e-commerce experiences to be seamless and secure but, as fraud threats evolve, merchants are struggling to keep pace — and consumers are losing trust in merchants. Drawing on this year’s U.S. identity and fraud insights, this report explores the key factors contributing to the e-commerce trust gap.
You’ll learn:
 Report
Report
The scale of global cyberattacks continues to rise, and 2026 is poised to be the year of AI in cybersecurity.
In our 13th annual Data Breach Industry Forecast, we share our top predictions for the year ahead, including:
Gain insight into the trends shaping the future of data security. Download the full forecast to prepare for what’s ahead.
 Video
Video
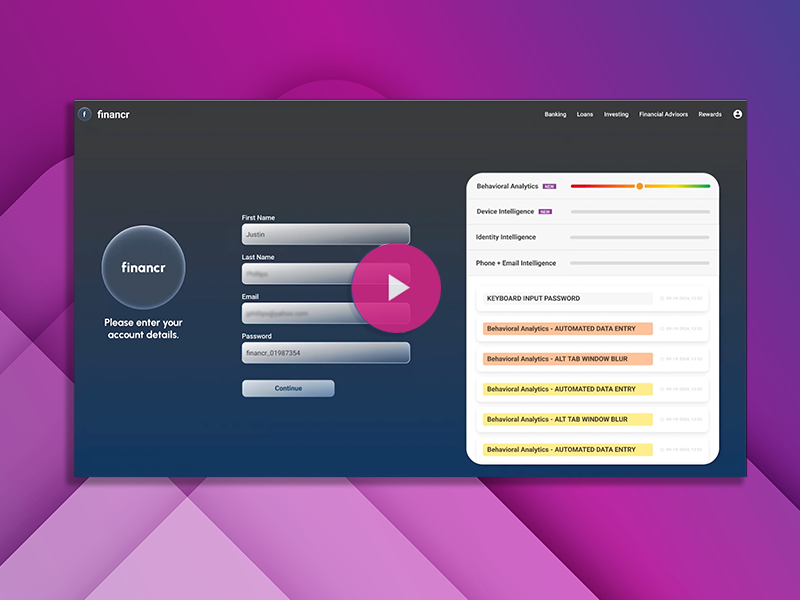
Fraud doesn’t happen in silos — and neither should your defense.
Watch this product demo to see how Experian’s connected fraud prevention solution brings behavioral analytics, identity verification and digital intelligence together to:
 Webinar
Webinar
Consumers expect convenience online, but fraud concerns continue to challenge retailers’ ability to deliver frictionless experiences. In this on-demand webinar, you’ll learn:
 Infographic
Infographic
Home equity lending is shifting fast and hidden risks could be costing you.