Ecommerce / Retail

On June 7, the Consumer Financial Protection Bureau (CFPB) released a new study that found that the ways “credit invisible” consumers establish credit history can differ greatly based on their economic background. The CFPB estimated in its May 2015 study "Data Point: Credit Invisibles" that more than 45 million American consumers are credit invisible, meaning they either have a thin credit file that cannot be scored or no credit history at all. The new study reviewed de-identified credit records on more than one million consumers who became credit visible. It found that consumers in lower-income areas are 240 percent more likely to become credit visible due to negative information, such as a debt in collection. The CFPB noted consumers in higher-income areas become credit visible in a more positive way, with 30 percent more likely to become credit visible by using a credit card and 100 percent more likely to become credit visible by being added as a co-borrower or authorized user on someone else’s account. The study also found that the percentage of consumers transitioning to credit visibility due to student loans more than doubled in the last 10 years. CFPB’s research highlights the need for alternative credit data The new study demonstrates the importance of moving forward with inclusion of new sources of high-quality financial data — like on-time payment data from rent, utility and telecommunications providers — into a consumer’s credit file. Experian recently outlined our beliefs on the issue in comments responding to the CFPB’s Request for Information on Alternative Data. As a brand, we have a long history of using alternative credit data to help lenders make better lending decisions. Extensive research has shown that there is an immense opportunity to facilitate greater access to fair and affordable credit for underserved consumers through the inclusion of on-time telecommunications, utility and rental data in credit files. While these consumers may not have a traditional credit history, many make on-time payments for telephone, rent, cable, power or mobile services. However, this data is not typically being used to enhance traditional credit files held by the nationwide consumer reporting agencies, nor is it being used in most third-party or custom credit scoring models. Further, new advances in financial technology and data analytics through account aggregation platforms are also integral to the credit granting process and can be applied in a manner to broaden access to credit. Experian is currently using account aggregation software to obtain consumer financial account information for authentication and income verification to speed credit decisions, but we are looking to expand this technology to increase the collection and utilization of alternative data for improving credit decisions by lenders. Policymakers should act to help credit invisible consumers While Experian continues to work with telecommunications and utility companies to facilitate the furnishing of on-time credit data to the nationwide consumer reporting agencies, regulatory barriers continue to exist that deter utility and telecommunications companies from furnishing on-time payment data to credit bureaus. To help address this issue, Congress is currently considering bipartisan legislation (H.R. 435, The Credit Access and Inclusion Act of 2017) that would amend the FCRA to clarify that utility and telecommunication companies can report positive credit data, such as on-time payments, to the nation' s credit reporting bureaus. The legislation has bipartisan support in Congress and Experian encourages lawmakers to move forward with this important initiative that could benefit tens of millions of American consumers. In addition, Experian believes policymakers should more clearly define the term alternative data. In public policy debates, the term "alternative data" is a broad term, often lumping data sources that can or have been proven to meet regulatory standards for accuracy and fairness required by both the Fair Credit Reporting Act and the Equal Credit Opportunity Act with data sources that cannot or have not been proven to meet these standards. In our comment letter, Experian encourages policymakers to clearly differentiate between different types of alternative data and focus the consumer and commercial credit industry on public policy recommendations that will increase the use of those sources of data that have or can be shown to meet legal and societal standards for accuracy, validity, predictability and fairness. More info on Alternative Credit Data More Info on Alternative Financial Services

There are about as many definitions for people-based marketing as there are companies using the term. Each company seems to skew the definition to fit their particular service offering. The distinctions are vast, and especially for financial services companies running regulated campaigns, they can be incredibly important. At Experian, we define people-based marketing in its purest form: targeting at the individual level across channels. This is a practice we’re very familiar with in offline marketing, having honed arguably one of the most accurate views of U.S. consumers over the past three decades. And now we’re taking those tried and true principals and applying them to digital channels. It’s not as easy as it sounds. The challenge with people-based marketing With direct mail, people-based marketing was easy. Jane Doe lives at 123 Main St. If I want to reach her, I can simply send her a direct mail piece at that address. To help, I can utilize any number of services, including the National Change of Address database, to know where to reach her if she ever moves. People-based marketing through digital channels is exponentially more difficult. While direct mail has one signal with which you use to identify a consumer (the address), digital channels offer countless signals. And not all of those signals can be used, either individually or in conjunction with other signals, to reliably tie a consumer to a persistent offline ID. A prime example of this is cookies. The problem with cookies A cookie, in and of itself, isn’t the problem. The problem is the linkage. How was a cookie associated with the person to whom the ad is being served? As marketers, we need to make sure that we are reaching the right people with the right ad … and more importantly not reaching those people who have opted out. This is especially true in the world of regulated data, where you need to know who you are targeting. And cookie-based linkage is controlled by a handful of companies, many of which are walled gardens who don’t share how they link offline people to online cookies and don’t collect this information directly. They rely on other third-party websites to gather PII, and connect it to their cookies. In some cases, the data is very accurate (especially with transaction data). In some cases, it is not (think websites that collect PII when giving surveys, offering coupons, etc.). In short, in order for you to use cookie-based targeting accurately, you need to have insight into the source of the base linkage data that was used to connect the offline consumer record to the online cookie. This same concept applies to all forms of digital linkage that drive people-based marketing. Why does people-based marketing matter in digital credit marketing? With campaigns that utilize non-regulated data, such as “Invitation to Apply” campaigns that are driven from demographic and psychographic data, the consequences of not reaching the consumer you meant to target are negligible. But with campaigns that utilize regulated data, you must ensure you’re targeting the exact consumer you meant to reach. More importantly, you must make sure you’re not targeting an ad to a consumer who had previously opted out of receiving offers driven with regulated data (prescreen offers, for example). Even if you’ve already delivered a direct mail piece with the same offer, this doesn’t negate your responsibility to reach only approved consumers who have not opted out. --- Bottom line, the world of 1:1 marketing is growing more sophisticated, and that’s a good thing. Marketers just need to understand that while regulated data can be powerful, they must also take great responsibility when handling it. The data exists to deliver firm offers of credit to your very specific target in all-new mediums. People-based marketing has its place, and it can now be done in a compliant, digitally-savvy way – in the financial services space, nonetheless. Register for our webinar on Credit Marketing Strategies to Drive Today's Digital Consumer.

The final day of Vision 2017 brought a seasoned group of speakers to discuss a wide range of topics. In just a few short hours, attendees dove into a first look at Gen Z and their use of credit, ecommerce fraud, the latest in retail, the state of small business and leadership. Move over Millennials – Gen Z is coming of credit age Experian Analytics leaders Kelley Motley and Natasha Madan gave audience members an exclusive look at how the first wave of Gen Z is handling and managing credit. Granted most of this generation is still under the age of 18, so the analysis focused on those between the ages of 18 to 20. Yes, Millennials are still the dominant generation in the credit world today, standing strong at 61 million individuals. But it’s important to note Gen Z is sized at 86 million, so as they age, they’ll be the largest generation yet. A few stats to note about those Gen Z individuals managing credit today: Their average debt is $12,679, compared to younger Millennials (21 to 27) who have $65,473 in debt and older Millennials (28 to 34) who sport $121,460. Given their young age, most of Gen Z is considered thin-file (less than 5 tradelines) Average Gen Z income is $33,000, and average debt-to-income is low at 5.7%. New bankcard balances are averaging around $1,574. As they age, acquire mortgages and vehicles, their debt and tradelines will grow. In the meantime, the speakers provided audience members a few tips. Message with authenticity. Think long-term with this group. Maintain their technological expectations. Build trust and provide financial education. State of business credit and more on the economy Moody’s Cris deRitis reiterated the U.S. economy is looking good. He quoted unemployment at 4.5%, stating “full employment is here.” Since the recession, he said we’ve added 15 million jobs, noting we lost 8 million during the recession. The great news is that the U.S. continues to add about 200,000 jobs a month, and that job growth is broad-based. Small business loans are up 10% year-to-date vs. last year. While there has been a tremendous amount of buzz around small business, he adds that most job creation has come from mid0size business (50 to 499 employees). The case for layered fraud systems Experian speaker John Sarreal shared a case study that revealed by layering on fraud products and orchestrating collaboration, a business can go from a string 75% fraud detection rate to almost 90%. Additionally, he commented that Experian is working to leverage dark web data to mine for breached identity data. More connections for financial services companies to make with mobile and social Facebook speaker Olivia Basu reinforced the need for all companies to be thinking about mobile. “Mobile is not about to happen,” she said. “Mobile is now. Mobile is everything. You look at the first half of 2017 and we’re seeing 40% of all purchases are happening on mobile devices.” Her challenge to financial services companies is to make marketing personal again, and of course leverage the right channels. Experian Sr. Director of Credit Marketing Scott Gordon commented on Experian’s ability to reach consumers accurately – whether that be through direct or digital delivery channels. A great deal of focus has been around person-based marketing vs. leveraging the cookie. -- The Vision conference was capped off with a keynote speech from legendary quarterback and Super Bowl MVP Tom Brady. He chatted about the details of this past season, and specifically the comeback Super Bowl win in February 2017. He additionally talked about leadership and what that means to creating a winning team and organization. -- Multiple keynote speeches, 65 breakout sessions, and hours of networking designed to help all attendees ready themselves for growing profits and customers, step up to digital, regulatory and fraud challenges, and capture the latest data insights. Learn more about Experian’s annual Vision conference.

Risk analysts are insatiable consumers of big data who require better intelligence to develop market insights, evaluate risk and confirm business strategies. While every credit decision, risk assessment model or marketing forecast improves when it is based on better, faster and more current data, leveraging large data sets can be challenging and unproductive. That’s why Experian added a new functionality to its Analytical Sandbox, giving clients the flexibility they need to analyze big data efficiently. Experian’s Analytical Sandbox now utilizes H2O –an open source machine learning and deep learning platform that can model and predict with high accuracy billions of rows of high-dimensional data from multiple sources in various formats. Through machine learning and advanced predictive modeling, the platform enables Experian to better provide on-demand data insights that empowers analysts with high-quality intelligence to inform regional trends, provide consumer transactional insight or expose marketing opportunities. As a hosted service, Sandbox is offered as a plug-and-play, meaning no internal development is required. Clients can instantly access the data through a secure Web interface on their desktop, giving users access to powerful artificial and business intelligence tools from their own familiar applications. No special training is required. “AI monetizes data,” said SriSatish Ambati, CEO of H2O.ai. “Our partnership with Experian democratizes and delivers AI to the wider community of financial and risk analysts. Experian's analytics sandbox can now model and predict with high accuracy billions of rows of high-dimensional data in mere seconds.” Through H2O and the Experian Sandbox, machine learning and predictive analytics are giving risk managers from financial institutions of all sizes the ability to incorporate machine learning models into their own big data processing systems.

In just a few short hours, Vision attendees immersed themselves into the depths of the economy, risk models, specialty finance data, credit invisibles, student loan data, online marketplace lending and more. The morning kicked off with one of the most respected and trusted macroeconomists in the U.S., Diane Swonk. With a rap sheet filled with advising central banks and multinational companies, Swonk treated a packed house to a look back on what has transpired in the U.S. economy since the Great Recession, as well as launching into current state and speculating on the months ahead. She described the past decade not as “lost, but rather lagging.” She went onto to say this past year was transitional, and while markets slowed slightly during the months leading up the U.S. presidential election, good things are happening: We’ve finally broken out of the 2% wage rut Recruiting on college campuses has picked up The labor force is growing Debt-to-income levels have returned to where they were prerecession and Investment is coming back. “I believe we’ll see growth over 2% this year,” said Swonk. Still, change is underway. She commented on how the way U.S. consumer spending is changing, and of course we’re seeing a restructuring in the retail space. While JC Penney announces store closings, you simultaneously see Amazon moving from “click to brick,” dabbling in the opening of some actual storefronts. Globally, she said the economy is the strongest it has been in eight years. She closed by noting there is a great deal of political change and unrest in the world today, but says, “Never underestimate our abilities when we tap our human capital.” -- More than 100 attendees filled a room to hear about the current trends and the future of online lending with featured guests from Oliver Wyman, Marlette Funding and Lending USA. While speakers commented on the “hiccup” in the space last year with some layoffs and mergers, volume has continued to double every year for the past several years with roughly $40 billion in cumulative originations today. Panelists discussed the use of alternative data to decision, channel bias, the importance of partnerships and how the market will see fewer and fewer players offering just one product specialty. “It is expensive to acquire customers, so you don’t just want to have one product to sell, but rather a range,” said Sharat Shankar of Lending USA. -- The numbers in the student lending universe are astounding. In a session focused on the U.S. student loan market, new Experian data reveals there is $1.49 billion in total student loan outstandings. In fact, total outstandings have grown 21% over the past four years, while the number of trades have only grown 4%. Costs are skyrocketing. The average balance per trade has grown 17% over the past four years. “We don’t ration education in this country,” said Joe DePaulo of College Ave. Student Loans. “We give everyone access to liquidity when it comes to federal student loans – and it’s not like that in other countries.” While DePaulo notes the access is great, offering many students the opportunity to obtain higher education, he says the problem is with disclosures. Guardians are often the individuals filling out the FAFSA, but the students inherit the loans. Students, he says, rarely understand how much their monthly payment will ultimately be after graduation. For every $10,000 in student loans, he says that will generally equate to a $100 monthly payment. -- Tomorrow, Vision attendees will be treated to more breakout sessions and a concluding keynote with legendary quarterback Tom Brady.

So many insights and learnings to report after the first full day of 2017 Vision sessions. From the musings shared by tech engineer and pioneer Steve Wozniak, to a panel of technology thought leaders, to countless breakout sessions on a wide array of business topics … here’s a look at our top 10 from the day. A mortgage process for the digital age. At last. In his opening remarks, Experian President of Credit Services Alex Lintner asked the audience to imagine a world when applying for a mortgage simply required a few clicks or swipes. Instead of being sent home to collect a hundred pieces of paper to verify employment, income and assets, a consumer could click on a link and provide a few credentials to verify everything digitally. Finally, lenders can make this a reality, and soon it will be the only way consumers expect to go through the mortgage process. The global and U.S. economies are stable. In fact, they are strong. As Experian Vice President of Analytics Michele Raneri notes, “the fundamentals and technicals look really solid across the countries.” While many were worried a year ago that Brexit would turn the economy upside down, it appears everything is good. Consumer confidence is high. The Dow Jones Index is high. The U.S. unemployment rate is at 4.7%. Home prices are up year-over-year. While there has been a great deal of change in the world – politically and beyond – the economy is holding strong. The rise of the micropreneur. This term is not officially in the dictionary … but it will be. What is it? A micropreneur is a business with 0 to 4 employees bringing in no more than $200k in annual revenue. But the real story is that numbers show microbusiness are improving on many fronts when it comes to contribution to the economy and overall performance compared to other small businesses. Keep an eye on these budding business people. Fraud is running fierce. Synthetic identity losses are estimated in the hundreds of millions annually, with 50% year-over year growth. Criminals are now trying to use credit cleaners to get tradelines removed from used Synthetic IDs. Oh, and it is essential for businesses to ready themselves for “Dark Web” threats. Experts advise to harden your defenses (and play offense) to keep pace with the criminal underground. As soon as you think you’ve protected everything, the criminals will find a gap. The cloud is cool and so are APIs. A panel of thought leaders took to the main stage to discuss the latest trends in tech. Experian Global CIO Barry Libenson said, “The cloud has changed the way we deliver services to our customers and clients, making it seamless and elastic.” Combine that with API, and the goal is to ultimately make all Experian data available to its customers. Experian President of Decision Analytics Steve Platt added, “We are enabling you to tap into what you need, when you need it.” No need to “rip and replace” all your tech. Expect more regulation – and less. A panel of regulatory experts addressed the fast-changing regulatory environment. With the new Trump administration settling in, and calls for change to Dodd-Frank and the Consumer Financial Protection Bureau (CFPB), it’s too soon to tell what will unfold in 2017. CFPB Director Richard Cordray may be making a run for governor of Ohio, so he could be transitioning out sooner than the scheduled close of his July 2018 term. The auto market continues to cruise. Experian’s auto expert, Malinda Zabritski, revealed the latest and greatest stats pertaining to the auto market. A few numbers to blow your mind … U.S. passenger cars and light trucks surpassed 17 million units for the second consecutive year Most new vehicle buyers in the U.S. are 45 years of age or older Crossover and sport utility vehicles remain popular, accounting for 40% of the market in 2016 – this is also driving up finance payments since these vehicles are more expensive. There are signs the auto market is beginning to soften, but interest rates are still low, and leasing is hot. Defining alternative data. As more in the industry discuss the need for alternative data to decision, it often gets labeled as something radical. But in reality, alternative data should be simple. Experian Sr. Director of Government Affairs Liz Oesterle defined it as “getting more financial data in the system that is predicted, validated and can be disputed.” #DeathtoPasswords – could it be a reality? It’s no secret we live in a digital world where we are increasingly relying on apps and websites to manage our lives, but let’s throw out some numbers to quantify the shift. In 2013, the average U.S. consumer had 26 online accounts. By 2015, that number increased to 118 online accounts. By 2020, the average person will have 207 online accounts. When you think about this number, and the passwords associated with these accounts, it is clear a change needs to be made to managing our lives online. Experian Vice President David Britton addressed his session, introducing the concept of creating an “ultimate consumer identity profile,” where multi-source data will be brought together to identify someone. It’s coming, and all of us managing dozens of passwords can’t wait. “The Woz.” I guess you needed to be there, but let’s just say he was honest, opinionated and notes that while he loves tech, he loves it even more when it enables us to live in the “human world.” Too much wonderful content to share, but more to come tomorrow …

In a May 4 speech before the ACA International Conference in Washington, FCC Commissioner Michael O’Rielly criticized the FCC’s past decisions on Telephone Consumer Protection Act (TCPA) and outlined his vision on the direction that the new Commission should head to provide more certainty to businesses. Commissioner O’Rielly noted that prior decisions by the FCC and courts have “expanded the boundaries of TCPA far beyond what I believe Congress intended.” He said that the new leadership at the Commission and a new Bureau head overseeing TCPA, provides the FCC with the opportunity to “undo the misguided and harmful TCPA decisions of the past that exposed legitimate companies to massive legal liability without actually protecting consumers.” O’Rielly laid out three principles that he thought would help to frame discussions and guide the development of replacement rules. First, he said that legitimate businesses need to be able to contact consumers to communicate information that they want, need or expect to receive. This includes relief for informational calls, as well as valid telemarketing calls or texts. Second, Commissioner O’Rielly said that FCC should change the definition of an autodialer so that valid callers can operate in an efficient manner. He went on to say that if FCC develops new rules to clarify revocation of consent, it should do so in a clear and convenient way for consumers, but also does not upend standard best practices of legitimate companies. Third, O’Rielly said that the FCC should focus on actual harms and bad actors, not legitimate companies. While Commissioner O’Rielly’ s comments signal his approach to TCPA reform, it is important to note that FCC action on the issue us unlikely to happen overnight. A rule must be considered by the Commission, which will have to allow for public notice and comment. Experian will continue to monitor regulatory and legislative developments on TCPA.

As we enter May, a month dedicated to recognizing our U.S. Armed Forces, it’s only fitting to think about how we are honoring this special group of people. Yes, there will likely be car deals, coupons, and even a few beautiful ceremonies, but as both lawmakers and leaders have recognized, these individuals and their families deserve protections every day. Especially in the financial services universe. There should be no exorbitant fees. No excessively high interest rates. And when they are called to active-duty, they should have avenues to ease their financial commitments and/or exit out of lease agreements. Thankfully, the Servicemembers Civil Relief Act (SCRA) and a strengthened Military Lending Act (MLA) were introduced to help. In fact, we are in year one of the enhanced MLA Final Rule in which compliance was mandated by Oct. 3, 2016. The extended MLA protections include a 36% Military Annual Percentage Rate (MAPR) cap to a wider range of credit products, including payday loans, vehicle title loans, refund application loans, deposit advance loans, installment loans and unsecured open-end lines of credit. The cap additionally applies to fees tacked on for credit-related ancillary products including finance charges and certain application and participation fees. The amended rule covers credit offered or extended to active-duty service members and their dependents, if the credit is subject to a finance charge or is payable by written agreement in more than four installments. And finally, one of the most important additions is that creditors must verify active-duty and dependents at origination. Right now, this can be accomplished by either working with a bureau, like Experian, or by vetting lists directly with the Department of Defense’s (DOD) own database. To continue to help with client need, the bureaus are working with the DOD and financial institutions to ensure alignment in delivery of military member and dependent data for a consistent, immediate and accurate MLA verification process. While much has been introduced over the past year to strengthen protections, there is still more to come. The compliance date for credit cards is Oct. 3, 2017. To date, the MLA status of millions upon millions of consumer credit applications have been verified, ensuring our military members and their dependents receive the financial protections they are entitled to under law. There are roughly 3.4 million military members and dependents in the MLA database, and this is an audience who sacrifices a great deal for our country. Thankfully, protections are finally being enforced to ensure they are taken care of too.

Experian and Creative Strategies share survey results about Apple’s AirPods, Google Home, Amazon Echo and Echo Dot for consumer behavior with voice devices.
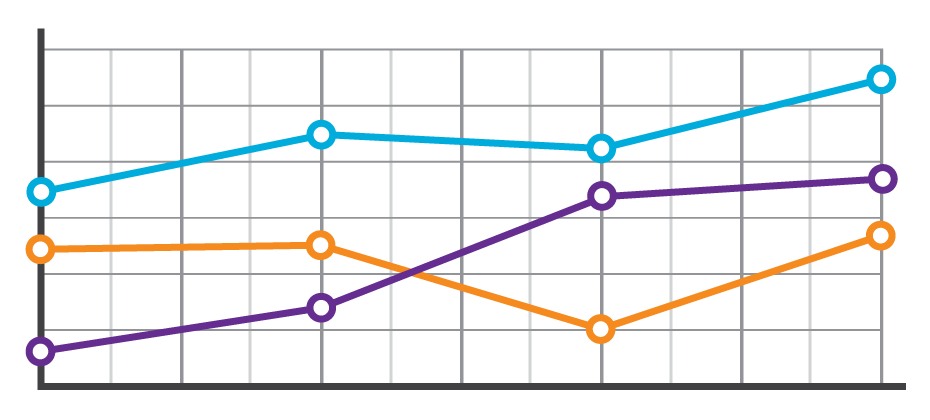
Sometimes life throws you a curve ball. The unexpected medical bill. The catastrophic car repair. The busted home appliance. It happens, and the killer is that consumers don’t always have the savings or resources to cover an additional cost. They must make a choice. Which bills do they pay? Which bills go to the pile? Suddenly, a consumer’s steady payment behavior changes, and in some cases they lose control of their ability to fulfill their obligations altogether. These shifts in payment patterns aren’t always reflected in consumer credit scores. At a single point in time, consumers may look identical. However, when analyzing their past payment behaviors, differences emerge. With these insights, lenders can now determine the appropriate risk or marketing decisions. In the example below, we see that based on the trade-level data, Consumer A and Consumer B have the same credit score and balance. But once we see their payment pattern within their trended data, we can clearly see Consumer A is paying well over the minimum payments due and has a demonstrated ability to pay. A closer look at Consumer B, on the other hand, reveals that the payment amount as compared to the minimum payment amount is decreasing over time. In fact, over the last three months only the minimum payment has been made. So while Consumer B may be well within the portfolio risk tolerance, they are trending down. This could indicate payment stress. With this knowledge, the lender could decide to hold off on offering Consumer B any new products until an improvement is seen in their payment pattern. Alternatively, Consumer A may be ripe for a new product offering. In another example, three consumers may appear identical when looking at their credit score and average monthly balance. But when you look at the trend of their historical bankcard balances as compared to their payments, you start to see very different behaviors. Consumer A is carrying their balances and only making the minimum payments. Consumer B is a hybrid of revolving and transacting, and Consumer C is paying off their balances each month. When we look at the total annual payments and their average percent of balance paid, we can see the biggest differences emerge. Having this deeper level of insight can assist lenders with determining which consumer is the best prospect for particular offerings. Consumer A would likely be most interested in a low- interest rate card, whereas Consumer C may be more interested in a rewards card. The combination of the credit score and trended data provides significant insight into predicting consumer credit behavior, ultimately leading to more profitable lending decisions across the customer lifecycle: Response – match the right offer with the right prospect to maximize response rates and improve campaign performance Risk – understand direction and velocity of payment performance to adequately manage risk exposure Retention – anticipate consumer preferences to build long-term loyalty All financial institutions can benefit from the value of trended data, whether you are a financial institution with significant analytical capabilities looking to develop custom models from the trended data or looking for proven pre-built solutions for immediate implementation.

It should come as no surprise that reaching consumers on past-due accounts by traditional dialing methods is increasingly ineffective. The new alternative, of course, is to leverage digital channels to reach and collect on debts. The Past: Dialing for dollars. Let’s take a walk down memory lane, shall we? The collection approach used for many years was to initially send the consumer a collection letter recapping the obligation and requesting payment, usually when an account was 30 days late. If the consumer failed to respond, a series of dialing attempts were then made, trying to reach the consumer and resolve the debt. Unfortunately, this approach has become less effective through the years due to several reasons: The use of traditional landlines continues to drop as consumers shift to cell and Voice Over Internet Protocol (VOIP) services. The cost of reaching consumers by cell is more costly since predictive dialers can’t be used without prior consent, and the obtaining and maintaining consent presents its own set of tricky challenges. Consumers simply aren’t answering their phones. If they think a bill collector is calling, they don’t pick up. It’s that simple. In fact, here is a breakdown by age group that Gallup published in 2015, highlighting the weakness of traditional phone-dialing. The Present: Hello payment portal. With the ability to get the consumer on the phone to negotiate a payment on the wane, the logical next step is to go digital and use the Internet or text messaging to reach the consumer. With 71 percent of consumers now using smartphones and virtually everyone having an Internet connection, this can be a cost-effective approach. Some companies have already implemented an electronic payment portal whereby a consumer can make a payment using his or her PC or smartphone. Usually this is prompted by a collection letter, or if permitted by consumer consent, a text message to their smartphone. The Future: Virtual negotiation. But what if the consumer wants to negotiate different terms or payment plans? What if they want to try and settle for less than the full amount? In the past – and for most companies operating today – this translates into a series of emails or letters being exchanged, or the consumer must actually speak to a debt collector on the phone. And let’s be honest, the consumer generally does not want to speak to a collector on the phone. Fortunately, there is a new technology involving a virtual negotiator approach coming into the market now. It works like this: The credit grantor or agency contacts the consumer by letter, email, or text reminding them of their debt and offering them a link to visit a website to negotiate their debt without a human being involved. The consumer logs onto the site, negotiates with the site and hopefully comes to terms with what is an acceptable payment plan and amount. In advance, the site would have been fed the terms by which the virtual negotiator would have been allowed to use. Finally, the consumer provides his payment information, receives back a recap of what he has agreed to and the process is complete. This is the future of collections, especially when you consider the younger generations rarely wanting to talk on the phone. They want to handle the majority of their matters digitally, on their own terms and at their own preferred times. The collections process can obviously be uncomfortable, but the thought is the virtual negotiator approach will make it less burdensome and more consumer-friendly. Learn more about virtual negotiation.

Knowing where e-commerce fraud takes place matters We recently hosted a Webinar with Mike Gross, Risk Strategy Director at Experian and Julie Conroy, Research Director at Aite Research Group, looking at the current state of card-not-present fraud, and what to prepare for in the coming year. Our biannual analysis of fraud attacks, served as a backdrop for the trends we’ve been seeing. I wanted to share some observations from the Webinar. Of course, if you prefer to hear it firsthand, you can download the archive recording here. I’ll start with the current landscape of card-not-present fraud. Julie shared 5 key trends her firm has identified regarding e-commerce fraud: Rising account take-over fraud Loyalty points targeted Increasingly global transactions Frustrating false declines Increasingly mobile consumers One particularly interesting note that Julie made was regarding consumer frustration levels towards forgotten passwords. While consumers are more frustrated when they’re locked out of access to their banking accounts (makes sense, it’s their money), forgotten passwords are more detrimental to e-commerce retailers since consumers are likely to go to another site. This equates to a frustrated consumer, and lost revenue for the business. Next, Mike went through the findings from our 2016 e-commerce fraud attack analysis. Fraud attack rates show the attempted fraudulent e-commerce transactions against the population of overall e-commerce orders. Overall, e-commerce attack rates spiked 33% in 2016. The biggest trends we saw included: Increased EMV adoption is driving a shift from counterfeit to card-not-present fraud 2B breached records disclosed in 2016, more than 3x any previous year Consumers reporting credit card fraud jumped from 15% in 2015 to over 32% in 2016 Attackers shifting locations slightly and international orders rely on freight forwarders 10 states saw an increase of over 100% in fraudulent orders Over 70 of the top 100 riskiest postal codes were not in last year’s list So, what will 2017 bring? Be prepared for more attacks, more global rings, more losses for businesses, and the emergence of IoT fraud. Businesses need to anticipate an increase of fraud over time and to be prepared. The value of employing a multi-layered approach to fraud prevention especially when it comes to authenticating consumers to validate transactions cannot be understated. By looking at all the points of the customer journey, businesses can better protect themselves from fraud, while maintaining a good consumer experience. Most importantly, having the right fraud solution in place can help businesses prevent losses both in dollars and reputation.

Turns out, Americans still don’t know much about CyberSecurity. That’s according to new research from the Pew Data Center, which conducted a cybersecurity knowledge quiz. The 13 question quiz was designed to test American’s knowledge on a number of cybersecurity issues and terms. A majority of online adults can identify a strong password and recognize the dangers of using public Wi-Fi. However, many struggle with more technical cybersecurity concepts, such as how to identify true two-factor authentication or determine if a webpage they are using is encrypted. As we in the industry know, cybersecurity is a complicated and diverse subject, but given the pervasiveness of news around cybersecurity, I was still a little surprised by the lack of knowledge. The typical (median) respondent answered only five of the 13 questions correctly (with a mean of 5.5 correct answers). 20% answered more than eight questions accurately, and just 1% received a “perfect score” by correctly answering all 13 questions. The study showed that public knowledge of cybersecurity is low on some relatively technical issues, like identifying the correct example of multi-factor authentication, understanding how VPNs minimize risk and knowing what a botnet is. On the flip side, the two questions that the majority of respondents answered correctly included identifying the strongest password from a list of four options and understanding that public Wi-Fi networks have risk even when they are password protected. Given the median scores, I was proud of missing only one question – guess I have more reading to do on Botnets. As an industry, it is our duty to not only create systems and securities to improve the tactical effectiveness of fraud prevention, but to educate consumers on many of these topics as well. They often are the first line of defense in stopping fraud and reducing the threat of breaches.

Newest technology doesn’t mean best when it comes to stopping fraud I recently attended the Merchant Risk Conference in Las Vegas, which brings together online merchants and industry vendors including payment service providers and fraud detection solution providers. The conference continues to grow year to year – similar to the fraud and risk challenges within the industry. In fact, we just released analysis, that we’ve seen fraud rates spike to 33% in the past year. This year, the exhibit hall was full of new names on the scene – evidence that there is a growing market for controlling risk and fraud in the e-commerce space. I heard from a few merchants at the conference that there were some “cool” new technologies out to help combat fraud. Things like machine learning, selfies and other two-factor authentication tools were all discussed as the latest in the fight against fraud. The problem is, many of these “cool” new technologies aren’t yet efficient enough at identifying and stopping fraud. Cool, yes. Effective, no. Sure, you can ask your customer to take a selfie and send it to you for facial recognition scanning. But, can you imagine your mother-in-law trying to manage this process? Machine Learning, while very promising, still has some room to grow in truly identifying fraud while minimizing the false positives. Many of these “anomaly detection” systems look for just that – anomalies. The problem is, we’re fighting motivated and creative fraudsters who are experts at avoiding detection and can beat anomaly detection. I do not doubt that you can stop fraud if you introduce some of these new technologies. The problem is, at what cost? The trick is stopping fraud with efficiency – to stop the fraud and not disrupt the customer experience. Companies, now more than ever, are competing based on customer experience. Adding any amount of friction to the buying process puts your revenue at risk. Consider these tips when evaluating and deploying fraud detection solutions for your online business. Evaluate solutions based on all metrics What is the fraud detection rate? What impact will it have on approvals? What is the false positive rate and impact on investigations? Does the attack rate decline after implementing the solution? Is the process detectable by fraudsters? What friction is introduced to the process? Use all available data at your disposal to make a decision Does the consumer exist? Can we validate the person’s identity? Is the web-session and user-entered data consistent with this consumer? Step up authentication but limit customer friction Is the technology appropriate for your audience (i.e. a selfie, text-messaging, document verification, etc...)? Are you using jargon in your process? In the end, any solution can stop 100% of the fraud – but at what cost. It’s a balance - a balance between detection and friction. Think about customer friction and the impact on customer satisfaction and revenue.

Has the EMV liability shift caused e-commerce fraud to increase 33% in 2016? According to Experian data, CNP fraud increased with Florida, Delaware, Oregon and New York ranked as the riskiest states. Miami accounted for the most fraudulent ZIP™ Codes in the US for shipping and billing fraud.