Tag: fraud

In today's fast-paced digital world, the risk of fraud across all industries is a constant threat. The traditional methods of fraud detection are no longer sufficient, as fraudsters become increasingly sophisticated in their attacks. However, with artificial intelligence (AI) and machine learning (ML) solutions, financial institutions can stay one step ahead of fraudsters. AI and machine learning-equipped fraud detection tools have the ability to identify suspicious activity and patterns of fraud that are imperceptible to the human brain. In this blog post, we’ll dive into the significance of AI and machine learning in fraud detection and how these solutions are uniquely equipped to handle the demands of modern-day risk management. Understanding artificial intelligence and machine learning AI and machine learning solutions are transformative technologies that are reshaping the landscape of many industries. AI, at its core, is a field of computer science that simulates human intelligence in machines, enabling them to learn from experience and perform tasks that normally require human intellect. Machine learning, a subset of AI, is the science of getting computers to learn and act like humans do, but with minimal human intervention. They can analyze vast amounts of data within seconds, identifying patterns and trends that would be impossible for a human to recognize. When it comes to fraud detection, this ability is invaluable. Advantages of fraud detection using machine learning AI and machine learning have several benefits that make them valuable in fraud detection. One significant advantage is that these technologies can recognize patterns that are too complex for humans to identify. By running through a vast set of data points, these solutions can pinpoint anomalous behavior, and thereby prevent financial losses. AI analytics tools are adept at monitoring complex networks, detecting the dispersion of attacks that may involve multiple individuals and entities, and correlating activity patterns that would otherwise be hidden. Machine learning algorithms can take these patterns and turn them into mathematical models that help identify instances of fraud before the damage takes place. Secondly, they continuously learn from new data, which allows them to become more efficient in identifying fraud as they process more data. Thirdly, they automate fraud mitigation processes, which significantly reduces the need for manual interventions that may consume valuable time and resources. Another significant benefit of machine learning is its analytics capabilities, which allow organizations to gain valuable insights into customer behavior and fraud patterns. With AI analytics, they can detect and investigate fraudulent activities in real-time, and combine it with other tools to help detect and mitigate fraud risk. For example, in financial services, AI fraud detection can help banks and financial service providers detect and prevent fraud in their systems, add value to their services and improve customer satisfaction. The future of fraud detection and machine learning The rate at which technology is evolving means that machine learning and AI fraud detection will become increasingly important in the future. In the next few years, we can expect a more sophisticated level of fraud detection using unmanned machine systems, robotics process automation, and more. Ultimately, this will improve the efficiency and effectiveness of fraud detection. AI-based fraud management solutions are taking center stage. Organizations must leverage advanced machine learning and AI analytics solutions to prevent and mitigate cyber risks and comply with regulatory mandates. The benefits extend far beyond the financial bottom line to improving the safety and security of customers. AI and machine learning solutions offer accurate, efficient and proactive routes to managing the risk of fraud in an ever-changing environment. How can Experian® help Integrating machine learning for fraud detection represents a significant advancement in cybersecurity. Fraud management solutions detect, prevent and manage fraud across all industries, including financial services, healthcare and telecommunications. With the advancement of technology, fraud management solutions now integrate machine learning to improve their processes. Experian® provides fraud prevention solutions, including machine learning models and AI analytics, which can help more effectively mitigate fraud risk, streamline fraud investigations and create a more secure digital environment for all. With Experian’s AI analytics, risk mitigation tools and fraud management solutions, organizations can stay one step ahead of fraudsters and protect their brand reputation, customer trustworthiness and corporate data. Embracing these solutions can save organizations from significant losses, reputational damage and regulatory scrutiny. To learn more about how to future-proof your business and safeguard your customers from fraud, check out Experian’s robust suite of fraud prevention solutions. Want to hear what our industry experts think? Check out this on-demand webinar on artificial intelligence and machine learning strategies. Learn more Watch webinar *This article includes content created by an AI language model and is intended to provide general information.

Sometimes logging into an account feels a bit like playing 20 questions. Security is vital for a positive customer experience, and engaging the right identity verification strategies is essential to proactive fraud prevention. For financial institutions and businesses, secure authentication is more important than ever. It is imperative for customer safety – which drives retention and loyalty – and your bottom line – as fraud has determinantal effects on and off the balance sheet. Information sharing has proliferated, as has the number of times consumers are prompted to provide access to sensitive information. While today’s consumer has grown accustomed to providing such information, there’s also a heightened demand for security. According to Experian’s 2023 U.S. Identity and Fraud Report, nearly two-thirds (64%) of consumers say they’re very or somewhat concerned with online safety, listing identity theft, stolen card information and online privacy as top concerns. Customers want to know who they are providing access to and whether that entity will have their safety in mind. From a business perspective, one way to ensure that only the right people can get in is by using (KBA). KBA takes traditional authentication methods, like passwords and Personal Identification Numbers (PINs), one step further by creating an additional layer of security through collecting private facts from each user. In this post, we'll look at how KBA works, what its benefits are as a form of identity verification, and how it can improve customer trust. Introducing Knowledge Based Authentication (KBA): What it is and how it works Knowledge Based Authentication can be part of a multifactor authentication solution and is one way to stay on top of privacy and security for your customers – existing and new. KBA is a feature designed to protect online accounts by verifying the account holder’s identity. It involves answering a series of personal questions, such as mother's maiden name or first pet's name, that only the account holder should know. This system has become increasingly popular due to its effectiveness in preventing fraud and identity theft. With KBA, businesses and individuals can have peace of mind that their information is protected by a reliable authentication system that is difficult for unauthorized users to breach. Benefits of implementing KBA and a multifactor authentication strategy By implementing KBA into your business, customers experience an additional layer of security by verifying the identity of users through personalized questions. This reduces the risk of fraud and enhances customer trust and confidence. Secondly, it improves the customer experience by making the authentication process faster and user-friendly. Lastly, KBA reduces costs by automating the authentication process and reducing the need for manual intervention. However, KBA is just one facet of an ideal strategy. Multifactor authentication provides confidence while reducing friction. Risk-based authentication tools allow organizations to assess risk to apply the appropriate level of security. Factors to consider adding to your authentication processes include: Generating unique one-time passwords (OTPs): By creating a new OTP for each transaction, you can increase the level of security. Confirm device ownership: A multifactored approach applies device intelligence checks to increase confidence that the message is reaching the correct user. Maintain low friction with secondary options: If the OTP fails or can’t be attempted by the user, working with a provider who allows an automatic default to another authentication service, such as a knowledge-based authentication solution, decreases end-user friction. Identifying potential security risks associated with KBA KBA relies on personal information that may easily be discovered via social media and other public records, which makes it vulnerable to fraud and identity theft. This highlights the need for a multilayered fraud and identity solution. The landscape of digital security is constantly changing, leveraging an arsenal of fraud and identity prevention strategies, like document verification, one-time passcode, and various identity authentication and verification measures, is critical for keeping your customers and business safe. Commonly used technologies for enhancing KBA security With the rising need for secure authentication, KBA systems have become increasingly popular. However, cyberthreats evolve at an alarming rate, making it imperative to stay current with the latest fraud schemes and how to enhance and supplement your security. Biometrics, like facial recognition and fingerprint scans, as a tactic is gaining traction, as evidenced by “85% of consumers report physical biometrics as the most trusted and secure authentication method they have recently encountered,” according to Experian’s 2023 U.S. Identity and Fraud Report. Additionally, machine learning algorithms detect patterns and anomalies in user behavior and flag any potential security breaches. Multi-factor authentication is another tool that adds an extra layer of security by requiring users to provide multiple forms of identification before logging in. Keeping up with these and other technological advancements can help ensure your KBA system stays one step ahead of potential cyberattacks. Interestingly, there’s a disconnect between the technologies consumers feel safe with and/or are prepared to use versus the technologies and strategies that organizations implement. According to the U.S. Identity and Fraud Report, biometrics are only currently used by 33% of businesses to detect and protect against fraud. An opportunity for business differentiation and driving customer loyalty through a better customer experience may be tapping into some of these lesser used – but sought after – technologies. Compliance with industry standards regarding KBA Ensuring that your system complies with industry standards regarding KBA is crucial for protecting sensitive information from unauthorized access. By implementing the following tips, you can stay ahead of the game and safeguard your organization's data. Analyze your system's current authentication methods and evaluate if they meet industry standards. Additionally, follow standard guidelines for data storage and encryption, limit access to only authorized personnel, and y current with regulations. Lastly, conduct frequent security audits and perform vulnerability tests to identify and address any potential threats. Knowledge-based authentication offers a robust security solution for businesses of all sizes, and incorporating KBA as part of a multifactor authentication strategy is a winning course of action. It provides an added layer of protection for personal data, encourages user accountability, and safeguards against unauthorized access. By leveraging appropriate KBA technologies and maintaining compliance with industry standards, it is possible to create a secure system for customers that gives you peace of mind for your business and bottom line. Experian can help you with knowledge-based authentication offerings, a multifactor authentication strategy and everything in between to enhance your existing authentication process without causing user fatigue. Increase your pass rates, confirm device ownership and add security to risky or high-value transactions, all while executing identity verification and fraud detection to protect your business from risk. The most important step is getting started. Learn more
It's that magical time of the year! The holiday season is fast approaching, and folks everywhere are gearing up for festive travels and family reunions. Unfortunately, holiday travel can sometimes lead to unforeseen circumstances, such as fraudulent activities orchestrated by scammers who impersonate property owners on well-known vacation rental platforms. These fraudsters employ schemes designed to deceive unsuspecting travelers into making payments through unsecured channels, resulting in significant financial losses for the gullible victims. Digital identity and hotel fraud Airline and hotel fraud encompasses illicit activities aimed at airlines, hotels, booking platforms, and other travel accommodation services, including car rentals and excursions. These services often utilize loyalty programs to incentivize repeat patronage through point-based rewards. The widespread adoption of such loyalty programs has extended their appeal beyond the travel and hospitality sectors, consequently attracting fraudulent activities. Perpetrators of airline and hospitality fraud employ a range of tactics and different techniques to execute their schemes, leveraging various online forums, marketplaces, shops, and public messaging platforms. Hotels are custodians of valuable guest data, encompassing contact information and payment details. Their operational model involves serving a large pool of potential customers who are making limited visits. Consequently, compromising a hospitality employee's account could grant an identity thief access to millions of consumer records. Moreover, hotel employees are frequent targets of foreign governments aiming to procure confidential travel records to facilitate the tracking of specific individuals and groups. In contrast, restaurants primarily store transaction records with fewer customer details. However, the landscape is evolving as more establishments adopt online ordering capabilities and loyalty programs. At present, cybercriminals typically focus on the high volume of point-of-sale transactions. As travel booms, fraudsters find new paths According to a recent Deloitte survey, Intent to travel between Thanksgiving and mid-January is up across all age and income groups. While reconnecting with friends and family remains paramount to travel during the holidays, fewer Americans are restricting their travel to visiting loved ones. The share of travelers planning to stay in hotels surged to 56%. Fraudsters will always take advantage of current circumstances, and with more people traveling again, they have taken notice — and action. The following techniques have been identified as the most employed by cybercriminals to target customers of airlines, hotels, and hospitality-related organizations: Travel-themed phishing and fraudulent travel agency operations, sales, and advertisements of travel fraud-related tutorials. Sales of compromised networks, user accounts, and databases containing reward/loyalty points and personally identifiable information (PII) that could be utilized for social engineering, money laundering, and other attack vectors. Since the emergence of cyber-enabled crime, services and activities facilitating travel fraud have been extensively promoted and sought after by threat actors. Cybercriminals mainly leverage stolen card-not-present (CNP) data and reward/loyalty points obtained from compromised bank accounts to procure flights, accommodations, and other travel-related services. Furthermore, threat actors persistently refine their strategies for harvesting reward/loyalty points through compromised accounts, deceiving victims into disclosing their travel-related documentation and data and circulating updated guidelines for circumventing hotel and airline reservation services, amongst other activities. Protecting travelers and improving the customer experience Combatting hospitality and hotel fraud requires collaboration between industry stakeholders, government entities, and financial institutions. Travel professionals should focus on: Enhancing data security: Invest in robust cybersecurity measures to protect guest information, payment systems for CNP, and loyalty programs. Implementing identity verification: Utilize advanced technologies, such as biometric authentication and behavioral analytics, to verify guests' identities and prevent account fraud. Educating staff and guests: Provide comprehensive training to employees on recognizing and reporting suspicious activities. Educate guests about potential scams and advise them to book directly through official channels. Sharing information: Establish platforms to share intelligence and best practices to stay ahead of evolving fraud techniques. Acting with the right solution As the travel and hospitality industry continues to thrive, so does the risk of hospitality fraud. Travelers and hoteliers alike must remain vigilant to protect their finances from various fraud schemes prevalent today. By staying informed, taking proactive measures, and fostering collaborative efforts, we can create a safer and more secure environment within the travel industry. Experian’s identity verification solutions power advanced capabilities across the travel lifecycle. With trusted data and advanced analytics, you can gain a complete view of your future guest to improve risk management and offer an enhanced, frictionless customer experience. Learn more *This article leverages/includes content created by an AI language model and is intended to provide general information.

This article was updated on November 9, 2023. Fraud – it’s a word that comes up in conversations across every industry. While there’s a general awareness that fraud is on the rise and is constantly evolving, for many the full impact of fraud is misunderstood and underestimated. At the heart of this challenge is the tendency to lump different types of fraud together into one big problem, and then look for a single solution that addresses it. It’s as if we’re trying to figure out how to un-bake a terrible cake instead of thinking about the ingredients and the process needed to put them together in the first place. This is the first of a series of articles in which we’ll look at some of the key ingredients that create different types of fraud, including first party, third party, synthetic identity, and account takeover. We’ll talk about why they’re unique and why we need to approach each one differently. At the end of the series, we’ll get a result that’s easier to digest. I had second thoughts about the cake metaphor, but in truth it really works. Creating a good fraud risk management process is a lot like baking. We need to know the ingredients and some tried-and-true methods to get the best result. With that foundation in place, we can look for ways to improve the outcome every time. Let’s start with a look at the best known type of fraud, third party. What is third-party fraud? Third-party fraud – generally known as identity theft – occurs when a malicious actor uses another person’s identifying information to open new accounts without the knowledge of the individual whose information is being used. When you consider first-party vs third-party fraud, or synthetic identity fraud, third-party stands out because it involves an identifiable victim that’s willing to collaborate in the investigation and resolution, for the simple reason that they don’t want to be responsible for the obligation made under their name. Third-party fraud is often the only type of activity that’s classified as fraud by financial institutions. The presence of an identifiable victim creates a high level of certainty that fraud has indeed occurred. That certainty enables financial institutions to properly categorize the losses. Since there is a victim associated with it, third party fraud tends to have a shorter lifespan than other types. When victims become aware of what’s happening, they generally take steps to protect themselves and intervene where they know their identity has been potentially misused. As a result, the timeline for third-party fraud is shorter, with fraudsters acting quickly to maximize the funds they’re able to amass before busting out. How does third-party fraud impact me? As the digital transformation continues, more and more personally identifiable information (PII) is available on the dark web due to data breaches and phishing scams. Given that consumer spending is expected to increase1, we anticipate that the amount of PII readily available to criminals will only continue to grow. All of this will lead to identity theft and increase the risk of third-party fraud. More than $43 billion in total losses was reported due to identity theft and fraud in the U.S. in 2022.2 Solving the third-party fraud problem We’ve examined one part of the fraud problem, and it is a complex one. With Experian as your partner, solving for it isn’t. Continuing my cake metaphor, by following the right steps and including the right ingredients, businesses can detect and prevent fraud. Third-party fraud detection and prevention involves two distinct steps. Analytics: Driven by extensive data that captures the ways in which people present their identity—plus artificial intelligence and machine learning—good analytics can detect inconsistencies, and patterns of usage that are out of character for the person, or similar to past instances of known fraud. Verification: The advantage of dealing with third-party fraud is the availability of a victim that will confirm when fraud is happening. The verification step refers to the process of making contact with the identity owner to obtain that confirmation and may involve identity resolution. It does require some thought and discipline to make sure that the contact information used leads to the identity owner—and not to the fraudster. In a series of articles, we’ll be exploring first-party fraud, synthetic identity fraud, and account takeover fraud and how a layered fraud management solution can help keep your business and customers safe and manage third-party fraud detection, first-party fraud, synthetic identity fraud, and account takeover fraud prevention. Let us know if you’d like to learn more about how Experian is using our identity expertise, data, and analytics to create robust fraud prevention solutions. Contact us 1 Experian Ascend Sandbox 2 2023 U.S. Identity and Fraud Report, Experian.

For companies that regularly engage in financial transactions, having a customer identification program (CIP) is mandatory to comply with the regulations around identity verification requirements across the customer lifecycle. In this blog post, we will delve into the essentials of a customer identification program, what it entails, and why it is important for businesses to implement one. What is a customer identification program? A CIP is a set of procedures implemented by financial institutions to verify the identity of their customers. The purpose of a CIP is to be a part of a financial institution’s fraud management solutions, with similar goals as to detect and prevent fraud like money laundering, identity theft, and other fraudulent activities. The program enables financial institutions to assess the risk level associated with a particular customer and determine whether their business dealings are legitimate. An effective CIP program should check the following boxes: Confidently verify customer identities Seamless authentication Understand and anticipate customer activities Where does Know Your Customer (KYC) fit in? KYC policies must include a robust CIP across the customer lifecycle from initial onboarding through portfolio management. KYC solutions encompass the financial institution’s customer identification program, customer due diligence and ongoing monitoring. What are the requirements for a CIP? Customer identification program requirements vary depending on the type of financial institution, the type of account opened, and other factors. However, the essential components of a CIP include verifying the customer's identity using government-issued identification, obtaining and verifying the customer's address, and checking the customer against a list of known criminals, terrorists, or suspicious individuals. These measures help detect and prevent financial crimes. Why is a CIP important for businesses? CIP helps businesses mitigate risk by ensuring they have accurate and up-to-date information about their customers. This also helps financial institutions comply with laws and regulations that require them to monitor financial transactions for any suspicious activities. By having a robust CIP in place, businesses can establish trust and rapport with their customers. According to Experian’s 2024 U.S. Identity and Fraud Report, 63% of consumers say it's extremely or very important for businesses to recognize them online. Having an effective CIP in place is part of financial institutions showing their consumers that they have their best interests top of mind. Finding the right partner It’s important to find a partner you trust when working to establish processes and procedures for verifying customer identity, address, and other relevant information. Companies can also utilize specialized software that can help streamline the CIP process and ensure that it is being carried out accurately and consistently. Experian’s proprietary and partner data sources and flexible monitoring and segmentation tools allow you to resolve CIP discrepancies and fraud risk in a single step, all while keeping pace with emerging fraud threats with effective customer identification software. Putting consumers first is paramount. The security of their identity is priority one, but financial institutions must pay equal attention to their consumers’ preferences and experiences. It is not just enough to verify customer identities. Leading financial institutions will automate customer identification to reduce manual intervention and verify with a reasonable belief that the identity is valid and eligible to use the services you provide. Seamless experiences with the right amount of friction (I.e., multi-factor authentication) should also be pursued to preserve the quality of the customer experience. Putting it all together As cybersecurity threats are becoming more sophisticated, it is essential for financial institutions to protect their customerinformation and level up their fraud prevention solutions. Implementing a customer identification program is an essential component in achieving that objective. A robust CIP helps organizations detect, prevent, and deter fraudulent activities while ensuring compliance with regulatory requirements. While implementing a CIP can be complex, having a solid plan and establishing clear guidelines is the best way for companies to safeguard customer information and maintain their reputation. CIPs are an integral part of financial institutions security infrastructures and must be a business priority. By ensuring that they have accurate and up-to-date data on their customers, they can mitigate risk, establish trust, and comply with regulatory requirements. A sound CIP program can help financial institutions detect and prevent financial crimes and cyber threats while ensuring that legitimate business transactions are not disrupted, therefore safeguarding their customers' information and protecting their own reputation. Learn more

In today’s fast-paced world, the telecommunications industry is not just about connecting calls or sending messages. It’s about creating seamless digital experiences, especially when onboarding new customers. However, with the rise of digital services, the industry faces an increasing challenge: the need to mitigate fraud while streamlining the onboarding process. The digital onboarding revolution Digital onboarding has transformed the way customers join telecommunications services. No longer are people required to visit a physical store or wait for lengthy paperwork. Instead, they can sign up for mobile, internet or TV services from the comfort of their homes, often within minutes. The convenience, however, has opened new doors for fraudsters. As the onboarding process happens online, the risk of identity theft, synthetic identity fraud and other fraudulent activities has surged. So, how can telecom companies provide fritctionless experiences while keeping fraud at bay? Mitigating fraud in telecommunications onboarding Know your customer (KYC) verification: Implement robust KYC solutions to verify the identity of new customers. This may include identity document checks, facial recognition or biometric authentication. Device and location data; and velocity: Analyze the device and location data of applicants. Does the device match the customer’s claimed location? Unusual patterns could signal potential fraud. Behavioral analysis: Monitor user behavior during the onboarding process. Frequent changes in information or suspicious browsing activity may indicate fraudulent intent. Machine learning (ML) and artificial intelligence (AI): Leverage AI/ML algorithms to detect patterns and anomalies humans might miss. These technologies can adapt and evolve to stay ahead of fraudsters. Document verification: Use document verification services to ensure that documents provided by customers are genuine. This can include checks for altered or forged documents. Industry data sharing–consortia: Collaborate with industry databases and share fraud-related information to help identify applicants with a history of fraudulent activity or reveal patterns. The balancing act While it’s crucial to mitigate fraud, telecommunication companies must strike a balance between security and a seamless onboarding experience. Customers demand a hassle-free process, and overly stringent security measures can deter potential subscribers. By combining advanced technology, behavioral analysis and proactive fraud prevention strategies, telecom companies can create a secure digital onboarding journey that minimizes risk without compromising user experience. In doing so, they empower customers to embrace the convenience of digital services while staying one step ahead of fraudsters in today’s interconnected world. Learn more about Experian and the telecom industry Learn more about our fraud and identity solutions

In this article...Fraud fueled by real-time paymentsReimbursement is vital to victimsAuthorized push payment fraud preventionTaking the next steps with the right partner Authorized Push Payment fraud, also known as APP fraud or APP scams, involves a fraudster persuading a victim to willingly deposit funds to their account or to the account of a complicit third party, also known as a money mule. This type of fraud often includes social engineering of the victim using fake investment schemes, impersonation scams, purchase scams or other schemes. Social engineering clouds victims' judgments and encourages them to make payments willingly to one or more money mules, with funds eventually reaching fraudsters' accounts. This type of fraud has become more attractive to criminals since the advent of real-time payment systems, which are now a reality worldwide. Fraud fueled by real-time payments Authorized push payment fraud is becoming more prevalent, and it is imperative that you know how to detect and prevent it to safeguard your organization. Real-time payment systems, such as Faster Payments in the United Kingdom (UK), PIX in Brazil, the New Payments Platform in Australia, and FedNow in the USA, make real-time payment fraud a reality. APP fraud is notoriously difficult for banks to prevent because the victim is sending the money themselves, and steps that banks take to authenticate customers are ineffective, as the customer will pass identity checks. The victims cannot reverse a payment once they realize they have been conned, as payments made using real-time payment schemes are irrevocable. APP fraud is particularly prevalent in countries where banks have an infrastructure that facilitates fast or immediate transfers, like the UK. Reimbursment is vital to victims Some common types of authorized push payment fraud include attacks on individuals like romance scams, family emergency swindles, targeting property transactions, and intercepting supplier payments. To protect against APP fraud, it is important to employ layered fraud protection across all products and channels used to manage real-time payments. But that alone is not enough. Reimbursement is vital in reversing the financial distress caused by APP scams, but it cannot reverse the emotional distress these scams cause. Prevention, detection, and awareness measures must be moved up on the agenda for banks, non-traditional lenders, PSPs (Payment Service Providers), and customers alike to ensure that the customer is protected at every stage of the payment journey. Effective alerts are a key focus area for preventing customers from falling victim to APP scams. An effective warning is one that is dynamic and tailored to the customer’s payment journey. Recent research indicates that minor changes to notifications across banking apps can have the potential to drastically reduce the number of individuals that fall victim to APP fraud. The biggest effects were achieved when a combination of risk-based and Call to Action (CTA) warnings were implemented over a period of time. A collective effort across the banking industry and beyond is crucial to protect customers and tackle the fight against APP fraud. Banks, non-traditional lenders, and PSPs can raise awareness to educate their customers on the signs and risks of APP scams, and work with industry oversight bodies to commit to voluntary standards and codes to ensure good customer outcomes. Online forums, social media platforms, and influential voices also have a role to play in raising awareness of and preventing scams. Customers can also help by being vigilant and reading and acting upon warnings and information presented to them. Authorized push payment fraud prevention To effectively combat authorized push payment fraud, financial institutions must implement a range of measures, including: Direct communication with consumers. Enhanced transaction monitoring. Effective risk mitigation and management. Improved employee education. Public awareness campaigns. In response to this growing threat, banks have introduced various checks and balances, such as the Confirmation of Payee (CoP) service in the UK, which cross-references bank details with the account holder's name when processing online payments. Banks are also leveraging sophisticated fraud prevention software stacks, incorporating machine learning and contextual data to identify and flag suspicious transactions. By utilizing AI technologies, financial institutions can process data points faster and enhance their fraud detection capabilities, mitigating identity risk and safeguarding customer accounts. Clear communication with customers is essential in the fight against APP fraud. Higher-risk companies now include warnings in their communications, advising customers not to act on messages that request payment into new bank accounts. Financial institutions can also offer cool-off periods before payments are sent, increase due diligence around payment destinations, and monitor accounts that regularly receive high-value payments. Additionally, financial institutions can play a crucial role in educating their customers and promoting awareness around this increasingly common type of fraud. By combining these approaches with robust fraud prevention software, the public can fight against this type of fraudulent attack. Taking the next steps with the right partner At Experian, we offer rich data sources, advanced analytics capabilities, and the consultancy services needed to rapidly adopt data analytics solutions that mitigate fraud risks. Our solutions are used by PSPs of all types and sizes – including some of the largest banks – to identify potentially fraudulent customers and transactions, and to ensure that action is taken in real time to prevent fraudulent payments being made. Learn more about our fraud management solutions

Have you heard about the mischievous ghosts haunting our educational institutions? No, I am not talking about Casper's misfit pals. These are the infamous ghost students! They are not here for a spooky study session, oh no! They are cunning fraudsters lurking in the shadows, pretending to be students who never attend classes. It is taking ghosting to a whole new level. Understanding ghost student fraud Ghost student fraud is a serious and alarming issue in the educational sector. The rise of online classes due to the pandemic has made it easier for fraudsters to exploit application systems and steal government aid meant for genuine students. Community colleges have become primary targets due to slower adoption of cybersecurity defenses. It is concerning to hear that a considerable number of applications, such as in California (where Social Security numbers are not required at enrollment), are fictitious, with potential losses in financial aid meant for students in need. The use of stolen or synthetic identities in creating bot-powered applications further exacerbates the problem. The consequences of enrollment fraud can have a profound impact on institutions and students. The recent indictment of individuals involved in enrollment fraud, where identities were stolen to receive federal student loans, highlights the severity of the issue. Unfortunately, the lack of awareness and inadequate identity document verification processes in many institutions make it difficult to fully grasp the extent of the problem. What is a ghost student? Scammers use different methods to commit ghost student loan fraud, including creating fake schools or enrolling in real colleges. Some fraudsters use deceitful tactics to obtain the real identities of students, and then they use it to fabricate loan applications. Types of ghost loan fraud, include: Fake loan offers: Fraudsters contact students via various channels, claiming to offer exclusive student loan opportunities with attractive terms and low interest rates. They often request personal and financial information including their SSN and bank account information and use it to create ghost loans. Identity theft: Threat actors will steal personal info through data breaches or phishing. They will then forge loan applications using the victim’s identity. Targeting vulnerable individuals: Ghost student loan fraud tends to prey on those already burdened by debt. Scammers may target borrowers with poor credit history, promising loan forgiveness or debt consolidation plans in exchange for a fee. Once the victim pays, the fraudsters disappear. Ultimately, addressing ghost student fraud requires a multi-faceted approach involving collaboration between educational institutions, government agencies, and law enforcement to safeguard the accessibility and integrity of education for all deserving students. Safeguarding the financial integrity of educational institutions One powerful weapon in the battle against ghost student fraudsters is the implementation of robust identity verification solutions. Financial institutions, online marketplaces, and government entities have long employed such tools to verify the authenticity of individuals, and their application in the educational domain can be highly effective. By leveraging these tools, institutions can swiftly and securely carry out synthetic fraud detection and confirm the identity of applicants by cross-referencing multiple credible sources of information. For instance, government-issued IDs can be verified against real-time selfies, email addresses can be screened against reliable databases, and personally identifiable information (PII) can be compared to third-party dark web data to detect compromised identities. Clinching evidence from various sources renders it nearly impossible for fraudsters to slip past the watchful eyes of enrollment officers. Moreover, implementation of identity verification measures can be facilitated through low-code implementation, ensuring seamless integration into existing enrollment workflows without requiring extensive technical expertise or incurring exorbitant development costs. To further fortify security measures, educational institutions may consider incorporating biometric enrollment and authentication solutions. By requiring face or voice biometrics for accessing school resources, institutions can create an additional layer of protection against fraudsters and their ethereal counterparts. The reluctance of fraudsters to enroll their own biometric data serves as a powerful deterrent against their intrusive activities. Taking action By adopting these robust measures, higher educational institutions can fortify their defenses against ghost student fraud and maintain the integrity of their finances. The use of online identity verification methods and biometric authentication systems not only strengthens the enrollment process but serves as a stringent reminder that there is no resting place for fraudsters within the hallowed halls of education. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call. *The SSN Verification tool, better known as eCBSV is also a tool that can be utilized to verify SSN. *This article leverages/includes content created by an AI language model and is intended to provide general information.

In financial crime, fraudsters are always looking for new avenues to exploit. The mortgage industry has traditionally been a primary target for fraudsters. But with the 30-year fixed-mortgage rate average above 7.19% for the month of September, it has caused an inherent slowdown in the volume of home purchases. As a result, criminals are turning to other lucrative opportunities in mortgage transactions. They have evolved their techniques to capitalize on unsuspecting homeowners and lenders by shifting their focus from home purchases to Home Equity Line of Credit (HELOC), as they see it as a more compelling option. Understanding mortgage fraud Mortgage fraud occurs when individuals or groups intentionally misrepresent information during the mortgage application process for personal gain. The most common forms of mortgage fraud include income misrepresentation, false identity, property flipping schemes, and inflated property appraisals. Over the years, financial institutions and regulatory bodies have implemented robust measures to combat such fraudulent activities. As the mortgage industry adapts to counter established forms of fraud, perpetrators are constantly seeking new opportunities to circumvent detection. This has led to a shift in fraud trends, with fraudsters turning their focus to alternative aspects of the mortgage market. One area that has captured recent attention is HELOC fraud, also known as home equity loan fraud. HELOC fraud: An attractive target for fraudsters What is a HELOC? HELOCs are financial products that allow homeowners to borrow against the equity in their homes, often providing flexible access to funds. While HELOCs can be a valuable financial tool for homeowners, they also present an attractive opportunity for fraudsters due to their unique characteristics. HELOC fraud schemes An example of a home equity loan fraud scheme is a fraudster misrepresenting himself to deceive a credit union call center employee into changing a member’s address and phone number. Three days later, the fraudster calls back to reset the member’s online banking password, allowing the fraudster to login to the member’s account. Once logged in, the fraudster orders share drafts to be delivered to the new address they now control. The fraudster then forges three share drafts totaling $309,000 and funds them through unauthorized advances against the member’s HELOC through online banking platforms. Why HELOCs are becoming the next target for mortgage fraud Rising popularity: HELOCs have gained significant popularity in recent years, enticing fraudsters seeking out opportunities with larger potential payouts. Vulnerabilities in verification: The verification process for HELOCs might be less rigorous than traditional mortgages. Fraudsters could exploit these vulnerabilities to manipulate property valuations, income statements, or other critical information. Lack of awareness: Unlike conventional mortgages, there may be a lack of awareness among homeowners and lenders regarding the specific risks associated with HELOCs. This knowledge gap can make it easier for fraudsters to perpetrate their schemes undetected. Home equity loans do not have the same arduous process that traditional first mortgages do. These loans do not require title insurance, have less arduous underwriting processes, and do not always require the applicant to be physically present at a closing table to gain access to cash. The result is that those looking to defraud banks can apply for multiple HELOC loans simultaneously while escaping detection. Prevention and safeguards There are several preventive measures and fraud prevention solutions that can be established to help mitigate the risks associated with HELOCs. These include: Education and awareness: Homeowners and lenders must stay informed about the evolving landscape of mortgage fraud, including the specific risks posed by HELOCs. Awareness campaigns and educational materials can play a significant role in spreading knowledge and promoting caution. Enhanced verification protocols: Lenders should implement advanced verification processes and leverage data analytics and modeling thorough property appraisals, income verification, and rigorous background checks. Proper due diligence can significantly reduce the chances of falling victim to HELOC-related fraud. Collaboration and information sharing: Collaboration between financial institutions, regulators, and law enforcement agencies is essential to combat mortgage fraud effectively. Sharing information, best practices, and intelligence can help identify emerging fraud trends and deploy appropriate countermeasures. Acting with the right solution Mortgage fraud is a constant threat that demands ongoing vigilance and adaptability. As fraudsters evolve their tactics, the mortgage industry must stay one step ahead to safeguard homeowners and lenders alike. With concerns over HELOC-related fraud rising, it is vital to raise awareness, strengthen preventive measures, and foster collaboration to protect the integrity of the mortgage market. By staying informed and implementing robust safeguards, we can collectively combat and prevent mortgage fraud from disrupting the financial security of individuals and the industry. Experian mortgage is powering advanced capabilities across the mortgage lifecycle by gaining market intelligence, enhancing customer experience to remove friction and tapping into industry leading data sources to gain a complete view of borrower behavior. To learn more about our HELOC fraud prevention solutions, visit us online or request a call. *This article leverages/includes content created by an AI language model and is intended to provide general information.

In today's fast-paced financial landscape, financial institutions must stay ahead of the curve when it comes to account opening and onboarding. Digital account opening, empowering a prospective client to securely and efficiently open a new account, is key to how banks, credit unions and other financial institutions grow their business and expand their portfolio. Regardless of the time, money and other resources a financial institution invests in marketing to the right target prospect and tailoring an attractive offer, it’s worthless if that prospective customer can’t complete the process due to a poor account opening experience. Unhappy customers vote with their feet. A recent Experian study found that of the more 2,000 consumers surveyed who’d opened a new account in the last six months, 37% took their business elsewhere due to a negative account opening experience. The choice of a reliable partner can make all the difference to your account opening and onboarding experience. The right partner must provide your financial institution with access to the freshest credit data; advanced analytics, scores and models to empower you to say yes to the right customers that meet your lending criteria; and industry-leading decision engines that make the best decisions and enable you to provide a seamless customer experience. Moreover, the right partner will also help you in maintaining high levels of security without compromising user experience, all while adhering to regulatory compliance. Recently, Liminal, a leading advisory and market intelligence firm specializing in the digital identity, cybersecurity, and fintech markets, released its highly anticipated Link™ Index Report for Account Opening in Financial Services, which evaluates solution providers in the financial sector, in the areas of compliance and fraud prevention for account opening. The report recognized Experian as a market leader for compliance and fraud prevention capabilities and market execution. Experian’s identity verification and fraud prevention solutions, including CrossCore® and Precise ID®, received the highest score out of the 32 companies highlighted in the report. It found that Experian was recognized by 94% of buyers and 89% identified Experian as a market leader. “We’re thrilled to be named the top market leader in compliance and fraud prevention capabilities and execution by Liminal’s Link Index Report,” said Kathleen Peters, Chief Innovation Officer for Experian’s Decision Analytics business in North America. “We’re continually innovating to deliver the most effective identity verification and fraud prevention solutions to our clients so they can grow their business, mitigate risk and provide a seamless customer experience.” You can access the full report here. To learn more about Experian’s award-winning fraud solutions, visit our identity fraud hub. Download Liminal Link Index Report

Are you looking for ways to make your financial institution more secure without adding unnecessary friction to the customer experience? Automated identity verification is an essential part of this process, safeguarding sensitive consumer information and helping to prevent fraud. This blog post will serve as the ultimate guide to automated identity verification so that you can understand why it's important and how it works. We'll cover all the details, like what automated ID verification is, how authentication software works with identifying documents, why automated identification technology is preferred over manual processes, and tips on implementing automation identity verification solutions into your business practices. What is automated identity verification? Automated identity verification is a secure, efficient process for verifying the identity of individuals or entities. This process is integral in various industries, especially the financial sector, to curb identity theft and fraudulent activities. It operates by using advanced analytics and authentication software that cross-references the provided data with a set of stored information. This technology eliminates manual ID verification, saving time and improving accuracy. ID verification automation uses artificial intelligence and machine learning to compare identifying credentials against various authenticating sources. Automated identity verification also comes into play for employment and income verification. Experian VerifyTM enables businesses through precise, real-time employment and income verification, ultimately helping businesses reduce risk, accelerate conversion and remove friction. For a more comprehensive understanding of automated identity verification, you can visit Experian's Identity Verification Solutions webpage, which provides a deep dive into the intricacies of identity verification, including insights on its importance in modern business operations and how it keeps your business secure. Benefits of automated identity verification for businesses and consumers Automated ID verification has revolutionized the way businesses conduct their operations and interact with customers. For businesses, AIV offers a range of benefits such as: Improved efficiency – businesses can automate the time-consuming process of identity verification, freeing up resources (staff) to focus on other critical tasks. Enhanced security – the technology ensures that customer data is secure and accurate, minimizing fraud risks and/or data breaches. Reduced costs – with the process being faster and more secure, costs are reduced as a byproduct. On the other hand, consumers enjoy a hassle-free experience as they can verify their identity within seconds, without physical documentation. This is essential for today’s consumers who expect frictionless experiences that keep them and their information safe. Data from Experian’s annual U.S. Identity and Fraud Report reflects these sentiments: 37% of consumers moved a new account opening process to another organization because of a poor experience; 95% of consumers say it's important to be repeatedly recognized online by businesses; and 60% of consumers are concerned about their online privacy. With automated identity verification, businesses can build trust, streamline their processes, and ultimately improve their bottom line. Furthermore, automated identity verification is a necessary component for businesses to minimize fraud risks in our evolving digital landscape. Living in an era where cybercrime is rampant, AIV safeguards businesses from potential fraudulent attempts and data breaches that could cause significant financial and reputational damage. From a compliance standpoint, automated identity verification ensures regulatory compliance, which is critical, considering the stringent regulations regarding customer data protection. Non-compliance can lead to severe legal repercussions and financial penalties. For financial institutions, Know Your Customer (KYC) policies must include Customer Identification Programs. Experian can help across the entire customer journey, from onboarding through portfolio management, while reducing risk of non-compliance and providing seamless authentication. Common challenges of automated identity verification As more companies turn to artificial intelligence and automation to deliver superior customer service experiences, the challenges businesses face have multiplied. One of the most common issues is ensuring identity proofing and accurate information protection within their networks. Although account takeover prevention has become more advanced, fraudsters still use increasingly sophisticated methods to circumvent it. As such, businesses must continuously develop new strategies to overcome these challenges, ensuring that their AI-powered solutions continue to provide reliable and secure user experiences. Types of identity verification solutions As the digital world continues to evolve, automated identity verification solutions have become a crucial part of online interactions. These solutions not only enhance security measures, but also provide faster and more efficient ways of identifying individuals. For instance, facial recognition is one example. Experian’s CrossCore® Doc Capture enables confident identity verification via facial recognition, which scans a person's face and compares it to their identification documents. Another type is voice recognition, which uses speech patterns to verify an identity. Additionally, document verification scans and validates various identification documents, such as driver's licenses and passports. It's essential to choose the most suitable AIV solution for your organization to ensure robust and reliable security measures. How to implement an automated ID verification solution It’s not new news that identity theft and fraud continue to be major concerns, particularly in an increasingly digital-only world. Implementing automated identity verification solutions to safeguard against such threats can seem daunting, particularly for businesses with limited IT resources. However, the benefits of automated ID verification, such as increased accuracy and efficiency, make it a worthwhile investment. When choosing a solution, consider factors such as the level of security provided, ease of implementation and integration with existing systems, and the ability to customize rules and settings. With careful planning and the right solution, , organizations can take a significant step towards improving their security posture and protecting their customers. Best Practices for automated identity verification Automated identity verification presents one way that financial institutions can increase automation. In doing so, organizations can improve accuracy, speed, and security in the verification process. One technique that has proven effective is the use of biometric technology, such as facial recognition and fingerprint scanning, to verify a person's identity. Additionally, utilizing various data sources, such as credit bureaus like Experian and government agencies, can increase the accuracy of verification. Implementing these best practices can not only save time and resources but also enhance customer experience by providing a seamless and secure verification process. In summary, automated identity verification is a vital tool for businesses and consumers to enhance their safety and security when engaging with customers. Automated identity verification streamlines customer processes across the lifecycle by eliminating manual checks and lengthy delays. As technology continues to evolve, it’s important for organizations to remain mindful that the methodologies used within automated identity verification will rapidly change as well. The key is to stay ahead. Automated identity verification solutions offer many advantages for businesses who want to maintain their trustworthiness while staying competitive in an ever-changing market. To learn more about Experian’s automated identity verification solutions, visit our website. Learn More *This article includes content created by an AI language model and is intended to provide general information.

The Federal Reserve (Fed) took a big step towards revolutionizing the U.S. payment landscape with the official launch of FedNow, a new instant payment service, on July 20, 2023. While the new payment network offers advantages, there are concerns that fraudsters may be quick to exploit the new real-time technology with fraud schemes like automated push payment (APP) fraud. How is FedNow different from existing payment networks? To keep pace with regions across the globe and accelerate innovation, the U.S. created a alternative to the existing payment network known as The Clearing House (TCH) Real-Time Payment Network (RTP). Fraudsters can use the fact that real-time payments immediately settle to launder the stolen money through multiple channels quickly. The potential for this kind of fraud has led financial regulators to consider measures to better protect against it. While both FedNow and RTP charge a comparable fee of 4.5 cents per originated transaction, the key distinction lies in their governance. RTP is operated by a consortium of large banks, whereas FedNow falls under the jurisdiction of the Federal Reserve Bank. This distinction could give FedNow an edge in the market. One of the advantages of FedNow is its integration with the extensive Federal Reserve network, allowing smaller local banks across the country to access the service. RTP estimates accessibility to institutions holding approximately 90% of U.S. demand deposit accounts (DDAs), but currently only reaches 62% of DDAs due to limited participation from eligible institutions. What are real-time payments? Real-time payments refer to transactions between bank accounts that are initiated, cleared, and settled within seconds, regardless of the time or day. This immediacy enhances transparency and instills confidence in payments, which benefits consumers, banks and businesses.Image sourced from JaredFranklin.com Real-time payments have gained traction globally, with adoptions from over 70 countries on six continents. In 2022 alone, these transactions amounted to a staggering $195 billion, representing a remarkable year-over-year growth of 63%. India leads the pack with its Unified Payments Interface platform, processing a massive $89.5 billion in transaction volume. Other significant markets include Brazil, China, Thailand, and South Korea. The fact that real-time payments cannot be reversed promotes trust and ensures that contracts are upheld. This also encourages the development of new methods to make processes more efficient, like the ability to pay upon receiving the goods or services. These advancements are particularly crucial for small businesses, which disproportionately bear the burden of delayed payments, amounting to a staggering $3 trillion globally at any given time. The launch of FedNow marks a significant milestone in the U.S. financial landscape, propelling the country towards greater efficiency, transparency, and innovation in payments. However, it also brings a fair share of challenges, including the potential for increased fraud. Are real-time payments a catalyst for fraud? As the financial landscape evolves with the introduction of real-time payment systems, fraudsters are quick to exploit new technologies. One particular form of fraud that has gained prominence is authorized push payment (APP) fraud. APP fraud is a type of scam where fraudsters trick individuals or businesses into authorizing the transfer of funds from their bank accounts to accounts controlled by the fraudsters. The fraudster poses as a legitimate entity and deceives the victim into believing that there is an urgent need to transfer money. They gain the victim's trust and provide instructions for the transfer, typically through online or telephone banking channels. The victim willingly performs the payment, thinking it is legitimate, but realizes they have been scammed when communication halts. APP fraud is damaging as victims authorize the payments themselves, making it difficult for banks to recover the funds. To protect against APP fraud, it's important to be cautious, verify the legitimacy of requests independently, and report any suspicious activity promptly. Fraud detection and prevention with real-time payments Advances in fraud detection software, including machine learning and behavioral analytics, make unusual urgent requests and fake invoices easier to spot — in real time — but some governments are considering legislation to ensure more support for victims. For example, in the U.K., frameworks like Confirmation of Payee have rolled out instant account detail checks against the account holder’s name to help prevent cases of authorized push payment fraud. The U.K.’s real-time payments scheme Pay.UK also introduced the Mule Insights Tactical Solution (MITS), which tracks the flow of fraudulent transactions used in money laundering through bank and credit union accounts. It identifies these accounts and stops the proceeds of crimes from moving deeper into the system – and can help victims recover their funds. While fraud levels related to traditional payments have slowly come down, real-time payment-related fraud has recently skyrocketed. India, one of the primary innovators in the space, recorded a 23% rise in fraud related to its real-time payments system in 2022. The same ACI report stated that the U.S., making up only 1.2% of all real-time payment transactions in 2022, had, for now, avoided the effects. However, “there is no reason to assume that without action, the U.S. will not follow the path to crisis levels of APP scams as seen in other markets.” FedNow currently has no specific plans to bake fraud detection into their newly launched technology, meaning the response is left to financial institutions. Fight instant fraud with instant answers Artificial Intelligence (AI) holds tremendous potential in combating the ever-present threat of fraud. With AI technologies, financial institutions can process vast amounts of data points faster and enhance their fraud detection capabilities. This enables them to identify and flag suspicious transactions that deviate from the norm, mitigating identity risk and safeguarding customer accounts. The ability of AI-powered systems to ingest and analyze real-time information empowers institutions to stay one step ahead in the battle against account takeover fraud. This type of fraud, which poses a significant challenge to real-time payment systems, can be better addressed through AI-enabled tools. With ongoing monitoring of account behavior, such as the services provided by FraudNet, financial institutions gain a powerful weapon against APP fraud. In addition to behavioral analysis, location data has emerged as an asset in the fight against fraud. Incorporating location-based information into fraud detection algorithms has proven effective in pinpointing suspicious activities and reducing fraudulent incidents. As the financial industry continues to grapple with the constant evolution of fraud techniques, harnessing the potential of AI, coupled with comprehensive data analysis and innovative technologies, becomes crucial for securing the integrity of financial transactions. Taking your next step in the fight against fraud Ultimately, the effectiveness of fraud prevention measures depends on the implementation and continuous improvement of security protocols by financial institutions, regulators, and technology providers. By staying vigilant and employing appropriate safeguards, fraud risks in real-time payment systems, such as FedNow, can be minimized. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call. *This article leverages/includes content created by an AI language model and is intended to provide general information.

In a recent episode of the Used Car Dealer Podcast, host Zach Klempf, sat down with Jim Maguire, Experian’s senior director of product marketing for automotive, to discuss the prevalence of fraud in the automotive industry. During their conversation, Jim highlighted the findings in Experian’s 2023 Identity and Fraud Report, giving listeners a deeper understanding into the evolving dynamics of fraud, with data and insights on the current landscape and what actionable strategies dealers can take to prevent it. The episode is now available across all major podcast platforms, click the link below to watch: YouTube For more information on the Used Car Dealer Podcast, visit - https://www.sellyautomotive.com/podcast Facebook - @SellyAutomotive Twitter - @SellyAutomotive LinkedIn - @SellyAutomotive

"Grandma, it’s me, Mike.” Imagine hearing the voice of a loved one (or what sounds like it) informing you they were arrested and in need of bail money. Panicked, a desperate family member may follow instructions to withdraw a large sum of money to provide to a courier. Suspicious, they even make a video call to which they see a blurry image on the other end, but the same voice. When the fight or flight feeling settles, reality hits. Sadly, this is not the scenario of an upcoming Netflix movie. This is fraud – an example of a new grandparent scam/family emergency scam happening at scale across the U.S. While generative AI is driving efficiencies, personalization and improvements in multiple areas, it’s also a technology being adopted by fraudsters. Generative AI can be used to create highly personalized and convincing messages that are tailored to a specific victim. By analyzing publicly available social media profiles and other personal information, scammers can use generative AI to create fake accounts, emails, or phone calls that mimic the voice and mannerisms of a grandchild or family member in distress. The use of this technology can make it particularly difficult to distinguish between real and fake communication, leading to increased vulnerability and susceptibility to fraud. Furthermore, generative AI can also be used to create deepfake videos or audio recordings that show the supposed family member in distress or reinforce the scammer's story. These deepfakes can be incredibly realistic, making it even harder for victims to identify fraudulent activity. What is Generative AI? Generative artificial intelligence (GenAI) describes algorithms that can be used to create new content, including audio, code, images, text, simulations, and videos. Generative AI has the potential to revolutionize many industries by creating new and innovative content, but it also presents a significant risk for financial institutions. Cyber attackers can use generative AI to produce sophisticated malware, phishing schemes, and other fraudulent activities that can cause data breaches, financial losses, and reputational damage. This poses a challenge for financial organizations, as human error remains one of the weakest links in cybersecurity. Fraudsters capitalizing on emotions such as fear, stress, desperation, or inattention can make it difficult to protect against malicious content generated by generative AI, which could be used as a tactic to defraud financial institutions. Four types of Generative AI used for Fraud: Fraud automation at scale Fraudulent activities often involve multiple steps which can be complex and time-consuming. However, GenAI may enable fraudsters to automate each of these steps, thereby establishing a comprehensive framework for fraudulent attacks. The modus operandi of GenAI involves the generation of scripts or code that facilitates the creation of programs capable of autonomously pilfering personal data and breaching accounts. Previously, the development of such codes and programs necessitated the expertise of seasoned programmers, with each stage of the process requiring separate and fragmented development. Nevertheless, with the advent of GenAI, any fraudster can now access an all-encompassing program without the need for specialized knowledge, amplifying the inherent danger it poses. It can be used to accelerate fraudsters techniques such as credential stuffing, card testing and brute force attacks. Text content generation In the past, one could often rely on spotting typos or errors as a means of detecting such fraudulent schemes. However, the emergence of GenAI has introduced a new challenge, as it generates impeccably written scripts that possess an uncanny authenticity, rendering the identification of deceit activities considerably more difficult. But now, GenAI can produce realistic text that sounds as if it were from a familiar person, organization, or business by simply feeding GenAI prompts or content to replicate. Furthermore, the utilization of innovative Language Learning Model (LLM) tools enables scammers to engage in text-based conversations with multiple victims, skillfully manipulating them into carrying out actions that ultimately serve the perpetrators' interests. Image and video manipulation In a matter of seconds, fraudsters, regardless of their level of expertise, are now capable of producing highly authentic videos or images powered by GenAI. This innovative technology leverages deep learning techniques, using vast amounts of collected datasets to train artificial intelligence models. Once these models are trained, they possess the ability to generate visuals that closely resemble the desired target. By seamlessly blending or superimposing these generated images onto specific frames, the original content can be replaced with manipulated visuals. Furthermore, the utilization of AI text-to-image generators, powered by artificial neural networks, allows fraudsters to input prompts in the form of words. These prompts are then processed by the system, resulting in the generation of corresponding images, further enhancing the deceptive capabilities at their disposal. Human voice generation The emergence of AI-generated voices that mimic real people has created new vulnerabilities in voice verification systems. Firms that rely heavily on these systems, such as investment firms, must take extra precautions to ensure the security of their clients' assets. Criminals can also use AI chatbots to build relationships with victims and exploit their emotions to convince them to invest money or share personal information. Pig butchering scams and romance scams are examples of these types of frauds where AI chatbots can be highly effective, as they are friendly, convincing, and can easily follow a script. In particular, synthetic identity fraud has become an increasingly common tactic among cybercriminals. By creating fake personas with plausible social profiles, hackers can avoid detection while conducting financial crimes. It is essential for organizations to remain vigilant and verify the identities of any new contacts or suppliers before engaging with them. Failure to do so could result in significant monetary loss and reputational damage. Leverage AI to fight bad actors In today's digital landscape, businesses face increased fraud risks from advanced chatbots and generative technology. To combat this, businesses must use the same weapons than criminals, and train AI-based tools to detect and prevent fraudulent activities. Fraud prediction: Generative AI can analyze historical data to predict future fraudulent activities. By analyzing patterns in data and identifying potential risk factors, generative AI can help fraud examiners anticipate and prevent fraudulent behavior. Machine learning algorithms can analyze patterns in data to identify suspicious behavior and flag it for further investigation. Fraud Investigation: In addition to preventing fraud, generative AI can assist fraud examiners in investigating suspicious activities by generating scenarios and identifying potential suspects. By analyzing email communications and social media activity, generative AI can uncover hidden connections between suspects and identify potential fraudsters. To confirm the authenticity of users, financial institutions should adopt sophisticated identity verification methods that include liveness detection algorithms and document-centric identity proofing, and predictive analytics models. These measures can help prevent bots from infiltrating their systems and spreading disinformation, while also protecting against scams and cyberattacks. In conclusion, financial institutions must stay vigilant and deploy new tools and technologies to protect against the evolving threat landscape. By adopting advanced identity verification solutions, organizations can safeguard themselves and their customers from potential risks. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call
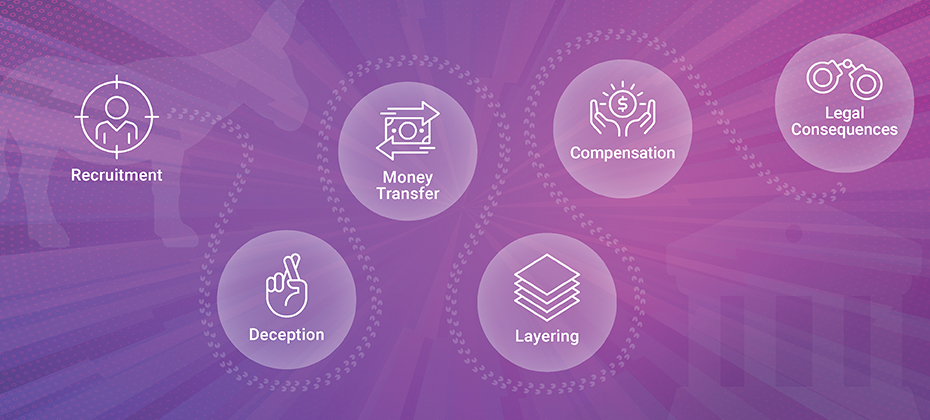
Money mule fraud is a type of financial scam in which criminals exploit individuals, known as money mules, to transfer stolen money or the proceeds of illegal activities. Money mule accounts are becoming increasingly difficult to distinguish from legitimate customers, especially as criminals find new ways to develop hard-to-detect synthetic identities. How money mule fraud typically works: Recruitment: Fraudsters seek out potential money mules through various means, such as online job ads, social media, or email/messaging apps. They will often pose as legitimate employers offering job opportunities promising compensation or claiming to represent charitable organizations. Deception: Once a potential money mule is identified, the fraudsters use persuasive tactics to gain their trust. They may provide seemingly legitimate explanations like claiming the money is for investment purposes, charity donations or for facilitating business transactions. Money Transfer: The mule is instructed to receive funds to their bank or other financial account. The funds are typically transferred from other compromised bank accounts obtained through phishing or hacking. The mule is then instructed to transfer the money to another account, sometimes located overseas. Layering: To mask the origin of funds and make them difficult to trace, fraudsters will employ layering techniques. They may ask the mule to split funds into smaller amounts, make multiple transfers to different accounts, or use various financial platforms such as money services or crypto. Compensation: The money mule is often promised a percentage of transferred funds as payment. However, the promised monies are lower than the dollars transferred, or sometimes the mule receives no payment at all. Legal consequences: Regardless whether mules know they are supporting a criminal enterprise or are unaware, they can face criminal charges. In addition, their personal information could be compromised leading to identity theft and financial loss. How can banks get ahead of the money mule curve: Know your beneficiaries Monitor inbound paymentsEngage identity verification solutionsCreate a “Mule Persona” behavior profileBeware that fraudsters will coach the mule, therefore confirmation of payee is no longer a detection solution Educate your customers to be wary of job offers that seem too good to be true and remain vigilant of requests to receive and transfer money, particularly from unknown individuals and organizations. How financial institutions can mitigate money mule fraud risk When new accounts are opened, a financial institution usually doesn’t have enough information to establish patterns of behavior with newly registered users and devices the way they can with existing users. However, an anti-fraud system should catch a known behavior profile that has been previously identified as malicious. In this situation, the best practice is to compare the new account holder’s behavior against a representative pool of customers, which will analyze things like: Spending behavior compared to the averagePayee profileSequence of actionsNavigation data related to machine-like or bot behaviorAbnormal or risky locationsThe account owner's relations to other users The risk engine needs to be able to collect and score data across all digital channels to allow the financial institution to detect all possible relationships to users, IP addresses and devices that have proven fraud behavior. This includes information about the user, account, location, device, session and payee, among others. If the system notices any unusual changes in the account holder’s personal information, the decision engine will flag it for review. It can then be actively monitored and investigated, if necessary. The benefits of machine learning This is a type of artificial intelligence (AI) that can analyze vast amounts of disparate data across digital channels in real time. Anti-fraud systems based on AI analytics and predictive analytics models have the ability to aggregate and analyze data on multiple levels. This allows a financial institution to instantly detect all possible relationships across users, devices, transactions and channels to more accurately identify fraudulent activity. When suspicious behavior is flagged via a high risk score, the risk engine can then drive a dynamic workflow change to step up security or drive a manual review process. It can then be actively monitored by the fraud prevention team and escalated for investigation. How Experian can help Experian’s fraud prevention solutions incorporate technology, identity-authentication tools and the combination of machine learning analytics with Experian’s proprietary and partner data to return optimal decisions to protect your customers and your business. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call