Data & Analytics

Every portfolio has a set of delinquent customers who do not make their payments on time. Truth. Every lender wants to collect on those payments. Truth. But will you really ever be able to recover all of those delinquent funds? Sadly, no. Still, financial institutions often treat all delinquent customers equally, working the account the same and assuming eventually they’ll get their funds. The sentiment to recover is good, but a lot of collection resources are wasted on customers who are difficult or impossible to recover. The good news? There is a better way. Predictive analytics can help optimize the allocation of collection resources by identifying the most effective accounts to prioritize to your best collectors, do not contact and proceed to legal actions to significantly increase the recovery of dollars, and at the same time reduce collection costs. I had the opportunity to recently present at the annual Debt Buyer Association’s International Conference and chat with my peers about this very topic. We asked the room, “How many of you are using scoring to determine how to work your collection accounts?” The response was 50/50, revealing many of these well-intentioned collectors are working themselves too hard, and likely not getting the desired returns. Before you dive into your collections work, you need to respond to two questions: Which accounts am I going to work first? How am I going to work those accounts? This is where scoring enters the scene. A scoring model is a statistical algorithm that assigns a numerical expression based on known information to predict an unknown future outcome. You can then use segmentation to group individuals with others that show the same behavior characteristics and rank order groups for collection strategies. In short, you allow the score to dictate the collection efforts and slope your expenses based on the propensity and expected amount of the consumer to pay. This will inform you on: What type, if any, skip trace tactic you should use? If you should purchase additional data? What intensity you should work the account? With scoring, you will see different performances on different debts. If you have 100 accounts you are collecting on, you’ll then want to find the accounts where you will have the greatest likelihood to collect, and collect the most dollars. I like to say, “You can’t get blood from a stone.” Well the same holds true for certain accounts in your collections pile. Try all you like, but you’ll never recoup those dollars, or the dollars you do recoup will be minimal. With a scoring strategy, you can establish your “hit list” and find the most attractive accounts to collect on, and also match your most profitable accounts with your best collectors. My message to anyone managing a collections portfolio can be summed up in three key messages. You need to use scoring in your business to optimize resources and increase profits. The better data that goes into your model will net you better performance results. Get a compliance infrastructure in place so you can ensure you are collecting the right way and stay out of trouble. The beauty of scores is they tell you what to do. It will help you best match resources to the most profitable accounts, and work smarter, not harder. That’s the power of scoring.

What is blockchain? Blockchain is beginning to get a lot of attention, so I thought it might be time to figure out what it is and what it means. Basically, a blockchain is a permissionless, distributed database that maintains a growing list of records (transactions) in a linear, chronological (and time-stamped) ledger. At a high level, this is how it works. Each computer connected to the network gets a copy of the entire blockchain and performs the task of validating and relaying transactions for the whole chain. The batches of valid transactions added to the record are called “blocks.” A block is the “current” part of a blockchain that records some or all of the recent transactions and once completed goes into the blockchain as a permanent database. Each time a block gets completed, a new block is created, with every block containing a hash of the previous block. There are countless numbers of blocks in the blockchain. To use a conventional banking analogy, the blocks would be a full history of every banking transaction for every person, and the blockchain would be a complete banking history. The entire blockchain is sent to everyone who has access, and every user validates the information in the block. It’s like if Tom, Bob and Harry were standing on the street corner and saw a cyclist hit by a car. Individually, all three men will be asked if the cyclist was struck by the car, and all three will respond “yes.” The cyclist being hit by the car becomes part of the blockchain, and that fact cannot be altered. Blockchain generally is used in the context of bitcoin, where similar uses of the structure are called altchains. Why should I care or, at the very least, pay attention to this movement? Because the idea of it is inching toward the tipping point of mainstream. I recently read an article that identified some blockchain trends that could shape the industry in coming months. The ones I found most interesting were: Blockchain apps will be released Interest in use cases outside payments will pick up Consortia will prove to be important Venture capital money will flow to blockchain start-ups While it’s true that much of the hype around blockchain is coming from people with a vested interest, it is beginning to generate more generalized market buzz as its proponents emphasize how it can reduce risk, improve efficiency and ultimately provide better customer service. Let’s face it, the ability to maintain secure, fast and accurate calculations could revolutionize the banking and investment industries, as well as ecommerce. In fact, 11 major banks recently completed a private blockchain test, exchanging multiple tokens among offices in North America, Europe and Asia over five days. (You can read The Wall Street Journal article here.) As more transactions and data are stored in blockchain or altchain, greater possibilities open up. It’s these possibilities that have several tech companies, like IBM, as well as financial institutions creating what has become known as an open ledger initiative to use the blockchain model in the development of new technologies that will enable a wider array of services. There is no doubt that the concept is intriguing — so much so that even the SEC has approved a plan to issue stock via blockchain. (You can read the Wired article here.) The potential is enough to make many folks giddy. The idea that risk could become a thing of the past because of the blockchain’s immutable historical record — wow. It’s good to be aware and keep an eye on the open ledger initiative, but let’s not forget history, which has taught us that (in the wise words of Craig Newmark), “Crooks are early adopters.” Since blockchain’s original and primary usage has been with bitcoin, I don’t think it is unfair to say that there will be some perceptions to overcome — like the association of bitcoin to activities on the Dark Web such as money laundering, drug-related transactions and funding illegal activities. Until we start to see the application across mainstream use cases, we won’t know how secure blockchain is or how open business and consumers will be to embracing it. In the meantime, remind me again, how long has it taken to get to a point of practical application and more widespread use of biometrics? To learn more, click here to read the original article.

Who will take the coveted Super Bowl title in 2016? Now that we’re down to the final two teams, the commentary will heighten. Sportscasters, analysts, former athletes, co-workers ... even your local barista has an opinion. Will it be Peyton Manning's Denver Broncos or the rising Carolina Panthers? Millions will make predictions in the coming weeks, but a little research can go a long way in delivering meaningful insights. How have the teams been trending over the season? Are there injuries? Who is favored and what’s the spread? Which quarterback is leading in pass completions, passing yards, touchdowns, etc.? Who has been on this stage before, ready to embrace the spotlight and epic media frenzy? The world of sports is filled with stats resulting from historical data. And when you think about it, the world of credit could be treated similarly. Over the past several years, there has been much hype about “credit invisibles” and the need to “score more.” A traditional pull will likely leave many “no-file” and “thin-file” consumers out, so it’s in a lender’s best interest to leverage alternative scoring models to uncover more. But it’s also important to remember a score is just a snapshot, a mere moment in time. How did a consumer arrive to that particular score pulled on any given day? Has their score been trending up or down? Has an individual been paying off debt at a rapid pace or slipping further behind? Two individuals could have the exact same score, but likely arrived to that place differently. The backstory is good to know – in sports and in the world of credit. Trended data can be attached to balances, credit limits, minimum payment due, actual payment and date of payment. By assessing these areas on a consumer file for 24 months, more insights are delivered and lenders can take note of behavior patterns to assist with risk assessment, marketing and share-of-wallet analysis. For example, looking closer at those consumers with five trades or more, Experian trended data reveals: 27% are revolvers, carrying balances each month 27% are transactors, paying off large portions, or all of their balances 9% are rate surfers, who tend to frequently transfer balances to credit cards with 0% or low introductory rates. Now these consumers can be viewed beyond a score. Suddenly, lenders can look within or outside their portfolio to understand how consumers use credit, what to offer them, and assess overall profitability. In short, trended data provides a more detailed view of a borrower’s historical credit performance, and that richness makes for a more informed decision. Without a doubt, there is power in the score – and being able to score more – but when it comes time to place your bets, the trended data matters, adding a whole new dimension to an individual’s credit score. Place your wagers accordingly. As for who will win Super Bowl 2016? I haven’t a clue. I’m more into the commercials. And I hear Coldplay is on for the half-time show. If you’re betting, best of luck, and do your homework.

For marketers, the start of a new year is an opportunity to look ahead.

With Black Friday quickly approaching, a recent Experian study shows online Black Friday searches are already tracking ahead of last year. This October, the weekly search share for Black Friday averaged 12% higher than October 2014 and is expected to increase dramatically between now and Thanksgiving week. Top product searches for the week ending October 31, 2015 include: Marketers can design more successful campaigns and maximize rewards for both consumers and brands by staying on top of the latest search trends. >> Holiday Hot Sheet

While marketers typically begin deploying Halloween emails in September, last-minute mailings receive the highest response.

With the holidays around the corner, retailers are getting ready to release their holiday campaigns.
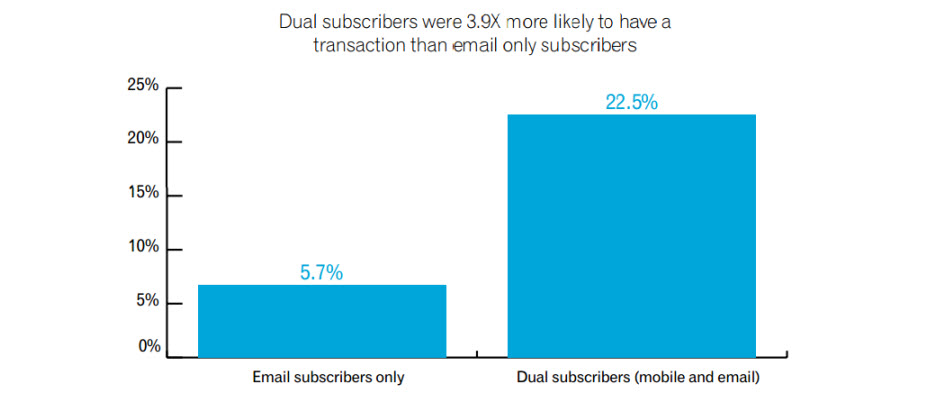
While mobile subscriber lists typically are much smaller than email lists, mobile subscribers tend to be loyal and highly engaged customers.

As Big Data becomes the norm in the credit industry and others, the seemingly non-stop efforts to accumulate more and more data leads me to ask the question - when is Big Data too much data? The answer doesn’t lie in the quantity of data itself, but rather in the application of it – Big Data is too much data when you can’t use it to make better decisions. So what do I mean by a better decision? From any number of perspectives, the answer to that question will vary. From the viewpoint of a marketer, maybe that decision is about whether new data will result in better response rates through improved segmentation. From a lender perspective, that decision might be about whether a borrower will repay a loan or the right interest rate to charge the borrower. That is one the points of the hype around Big Data – it is helping companies and individuals in all sorts of situations make better decisions – but regardless of the application, it appears that the science of Big Data must not just be based on an assumption that more data will always lead to better decisions, but that more data can lead to better decisions – if it is also the “right data”. Then how does one know when another new data source is helping? It’s not obvious that additional data won’t help make a better decision. It takes an expert to understand not only the data employed, but ultimately the use of the data in the decision-making process. It takes expertise that is not found just anywhere. At Experian, one of our core capabilities is based on the ability to distinguish between data that is predictive and can help our clients make better decisions, and that which is noise and is not helpful to our clients. Our scores and models, whether they be used for prospecting new customers, measuring risk in offering new credit, or determining how to best collect on an outstanding receivable, are all designed to optimize the decision making process. Learn more about our big data capabilities

According to a recent Experian Marketing Services study, informational or "thanks for joining" messages drive significantly higher open and transaction rates than promotional emails, as well as higher revenue per email.

By: Barbara Rivera Every day, 2.5 quintillion bytes of data are created – in fact, 90% of the world’s data was created in only the last few years. With the staggering amount of data available, we have an unprecedented opportunity to uncover new insights and improve the way our world functions. The implications of these new capabilities are perhaps nowhere else as crucial as within our government. Public sector officials carry the great responsibility of conducting complex missions that directly affect our communities, our economy, and our nation’s future. The ability to make more informed, insightful choices and better decisions is paramount. Especially at a time of broader global unrest and uncertainty, Americans rely on our government to be transparent, fair, ready and to make the right decisions – our trust is in the hands of our elected officials and public servants. Data alone is not enough to inform and affect change. However, with integrated information assets, insightful analysts and collaborative processes, data can be transformed into something meaningful and actionable. Our government has already begun leveraging data for good across agencies and varied missions, with more potential unlocked each day. Local governments like Orange County, California are utilizing data through address verification services to keep their voting lists accurate – ensuring the integrity of elections and saving the taxpayers thousands of dollars otherwise wasted on mailings to outdated lists. The Orange County Registrar of Voters – the fifth largest voting jurisdiction in the county – has been able to cancel 40,000 voting records, with an estimated savings of $94,000 expected from 2012 through 2016. The examples are numerous and growing: A suite of optimization tools helps states find non-custodial parents, determine their capacity and likelihood to pay child support, and trigger alerts with new critical information, maximizing the likelihood of payment and recovery, ultimately improving the welfare of children and reducing poverty More than 150 state, county and local law enforcement agencies leverage data to help identify persons of interest, conduct background screening for employees and contractors and provide financial backgrounds for criminal investigations, ensuring our continued safety By using the power of data to manage user authentication, credentials and access controls, the government is working harder – and smarter – to protect our security The government is leveraging verified commercial data to help agencies validate the fiscal responsibility of potential contractors and monitor existing contractors, which helps provide transparency and reduce risk By using data and analytics to authenticate applicants and validate financial data, the government is ensuring access to benefits for those who meet eligibility requirements, while at the same time reducing fraud Private sector partners are supporting municipal efforts to improve financial stability in households by providing the current credit standing of consumers and monitoring overall changes in financial behaviors over time, to help counsel and educate citizens And that’s only the beginning. The possibilities are endless – from healthcare to finance to energy – data can be leveraged for the advancement of our society. It even happens behind the scenes, working to protect information in ways most citizens never realize. Data insights are used to ensure citizens have secure online access to their information – ever see those randomized, personal questions? That’s data at work. The same technology is the de facto ID Proofing standard for the VA and CMS. How does it all work? By combing through the data carefully, putting it in context, looking at it in new ways, and thinking about what all this information really means. Much of this is made possible through public-private partnerships between the government and companies like Experian. So the next time someone complains about the slow pace of government, let them know the truth is government is moving quickly, leveraging data and private sector partnerships to uncover new insights that impact the greater good.

This season’s peak week, the Wednesday before Thanksgiving through the Tuesday after Cyber Monday, had an 18 percent increase in email volume, an 11 percent rise in transactions and a 7 percent increase in email revenue in comparison to peak week 2013. Cyber Monday provided 27 percent of total peak week revenue followed by Black Friday, which accounted for 18 percent of revenue. Marketers can design more successful holiday campaigns by staying on top of the latest email trends. View the December Holiday Hot Sheet

According to a recent Experian Data Quality study, three out of four organizations personalize their marketing messages or are in the process of doing so.

According to Experian Marketing Services’ Q1 2014 Email Benchmark Report, personalized abandoned cart emails that dynamically show the actual customer cart had 25 percent higher transaction rates than reminder emails that just linked back to the brand’s Website.

As part of its guidance, the Office of the Comptroller of the Currency recommends that lenders perform regular validations of their credit score models in order to assess model performance.