Topics

During the last couple of years, volatile market conditions have made it more difficult for consumers to improve their finances. In addition, a lack of financial literacy has negatively impacted consumers’ ability to expand their buying power. This can include opening new lines of credit, which is a source of revenue for financial institutions. Empowering your consumers with credit education and resources can create opportunities for them to open more of these new accounts, which can help lead to additional revenue for your business. Credit card account openings decreased in 2023 Economic turbulence is affecting businesses everywhere, including financial institutions. Uncertain market conditions have forced banks and credit unions to take revenue-preserving actions, such as tightening their credit card loan standards for consumers. As a result, credit card digital account opening growth slowed in 2023, and the trend threatens to continue.[1] This decrease in the opening of new credit card accounts can negatively affect lenders that aim to grow their business by encouraging consumers to borrow more money. Consumers’ financial literacy also plays a role in their ability and inclination to open new accounts. Uninformed consumers may be less likely to open new accounts Without a strong understanding of finances, many consumers find themselves in an unfavorable financial situation. Less than 30% of Americans have a financial plan,[2] and lacking financial knowledge cost individuals $1,819 on average in 2022.[3] Consumers without basic knowledge of finance or credit best practices usually have lower credit scores and may be less likely to qualify for credit card offers with low interest rates. So, what can financial institutions do to counteract decreasing credit card account openings? Help improve consumers credit standing with credit education Credit education programs can have a positive effect on consumers’ credit standing and general understanding of healthy financial habits. More than 65% of consumers enrolled in a credit education program see an improvement on their credit scores.[4] Credit-educated individuals can typically attain higher credit scores, which can help improve their chances of meeting the more restrictive credit standards banks have put in place due to volatile market conditions. Consumers who are better informed about credit and finances make better financial decisions, save, and borrow more money, and may be more likely to open new credit card accounts. This presents a valuable opportunity for financial institutions to offer highly desired credit education services to the consumers who need it. Deliver services your customers want A recent study showed that 57% of consumers want their financial institution to provide resources and support to help them better manage their finances, and 54% feel that their bank is responsible for teaching strong financial habits.[5] Consumers expect these financial services from the banks they do business with. Refraining from offering them could put your business at a disadvantage when compared to the banks that do. Make sure the services you provide include credit education that empowers your consumers to become more financially confident. This can help drive consumers to borrow more money and potentially open more new credit lines, which can drive additional revenue for your business. Learn more about how offering credit education services can help your consumers save more, borrow more, and open more new accounts. Visit our website [1] eMarketer, Credit Card Marketing 2023. [2] BusinessDIT, The State of Financial Planning, April 2023. [3] National Financial Educators Council, Cost of Financial Illiteracy Survey, 2023. [4] Experian Internal Data, 2023 credit lift study for users tracked from Dec 2020 – Dec 2022. [5] MX Technologies Inc. What Influences Where Consumers Choose to Bank. 2023.

This article was updated on February 23, 2024. First impressions are always important – whether it’s for a job interview, a first date or when pitching a client. The same goes for financial services onboarding as it’s an opportunity for organizations to foster lifetime loyalty with customers. As a result, financial institutions are on the hunt now more than ever for frictionless online identity verification methods to validate genuine customers and maintain positive experiences during the online onboarding process. In a predominantly digital-first world, financial companies are increasingly focused on the customer experience and creating the most seamless online onboarding process. However, according to Experian’s 2023 Identity and Fraud Report, more than half of U.S. consumers considered dropping out during account opening due to friction and a less-than positive experience. And as technology continues to advance, digital financial services onboarding, not surprisingly, increases the demand for fraud protection and authentication methods – namely with digital identity (ID) verification processes. According to Experian’s report, 64% of consumers are very or somewhat concerned with online security, with identity theft being their top concern. So how can financial institutions guarantee a frictionless online onboarding experience while executing proper authentication methods and maintaining security and fraud detection? The answer? While a “frictionless” experience can seem like a bit of a unicorn, there are some ways to get close: Utilizing better data - Digital devices offer an extensive amount of data that’s useful in determining risk. Characteristics that allow the identification of a specific device, the behaviors associated with the device and information about a device’s owner can be captured without adding friction for the user. Analytics – Once the data is collected, advanced analytics uses information based on behavioral data, digital intelligence, phone intelligence and email intelligence to analyze for risk. While there’s friction in the initial ask for the input data, the risk prediction improves with more data. Document verification and biometric identity verification – Real-time document verification used in conjunction with facial biometrics, behavioral biometrics and other physical characteristics allows for rapid onboarding and helps to maintain a low friction customer journey. Financial institutions can utilize document verification to replace manual long-form applications for rapid onboarding and immediately verify new data at the point of entry. Using their mobile phones, consumers can photograph and upload identity documents to pre-fill applications. Document authenticity can be verified in real-time. Biometrics, including facial, behavioral, or other physical characteristics (like fingerprints), are low-touch methods of customer authentication that can be used synchronously with document verification. Optimize your financial services onboarding process Experian understands how critical identity management and fraud protection is when it comes to the online onboarding process and identity verification. That’s why we created layered digital identity verification and risk segmentation solutions to help legitimize your customers with confidence while improving the customer experience. Our identity verification solutions use advanced technology and capabilities to correctly identify and verify real customers while mitigating fraud and maintaining frictionless customer experiences. Learn more

While bots have many helpful purposes, they have unfortunately become a tool for malicious actors to gain fraudulent access to financial accounts, personal information and even company-wide systems. Almost every business that has an online presence will have to face and counter bot attacks. In fact, a recent study found that across the internet on a global scale, malicious bots account for 30 percent of automated internet activity.1 And these bots are becoming more sophisticated and harder to detect. What is a bot attack and bot fraud? Bots are automated software applications that carry out repetitive instructions mimicking human behavior.2 They can be either malicious or helpful, depending on their code. For example, they might be used by companies to collect data analytics, scan websites to help you find the best discounts or chat with website visitors. These "good" bots help companies run more efficiently, freeing up employee resources. But on the flip side, if used maliciously, bots can commit attacks and fraudulent acts on an automated basis. These might even go undetected until significant damage is done. Common types of bot attacks and frauds that you might encounter include: Spam bots and malware bots: Spam bots come in all shapes and sizes. Some might scrape email addresses to entice recipients into clicking on a phishing email. Others operate on social media sites. They might create fake Facebook celebrity profiles to entice people to click on phishing links. Sometimes entire bot "farms" will even interact with each other to make a topic or page appear more legitimate. Often, these spam bots work in conjunction with malware bots that trick people into downloading malicious files so they can gain access to their systems. They may distribute viruses, ransomware, spyware or other malicious files. Content scraping bots: These bots automatically scrape content from websites. They might do so to steal contact information or product details or scrape entire articles so they can post duplicate stories on spam websites. DDoS bots and click fraud bots: Distributed denial of service (DDoS) bots interact with a target website or application in such large numbers that the target can't handle all the traffic and is overwhelmed. A similar approach involves using bots to click on ads or sponsored links thousands of times, draining advertisers' budgets. Credential stealing bots: These bots use stolen usernames and passwords to try to log into accounts and steal personal and financial information. Other bots may try brute force password cracking to find one combination that works so they can gain unauthorized access to the account. Once the bot learns consumer’s legitimate username and password combination on one website, they can oftentimes use it to perform account takeovers on other websites. In fact, 15 percent of all login attempts across industries in 2022 were account takeover attacks.1 AI-generated bots: While AI, like ChatGPT, is vastly improving the technological landscape, it's also providing a new avenue for bots.3 AI can create audio and videos that appear so real that people might think they're a celebrity seeking funds. What are the impacts of bot attacks? Bot attacks and bot fraud can have a significant negative impact, both at an individual user level and a company level. Individuals might lose money if they're tricked into sending money to a fake account, or they might click on a phishing link and unwittingly give a malicious actor access to their accounts. On a company level, the impact of a bot attack can be even more widespread. Sensitive customer data might get exposed if the company falls victim to a malware attack. This can open the door for the creation of fake accounts that drain a company's money. For example, a phishing email might lead to demand deposit account (DDA) fraud, where a scammer opens a fraudulent account in a customer's name and then links it to new accounts, like new lines of credit. Malware attacks can also cause clients to lose trust in the company and take their business elsewhere.A DDoS attack can take down an entire website or application, leading to a loss of clients and money. A bot that attacks APIs can exploit design flaws to steal sensitive data. In some cases, ransomware attacks can take over entire systems and render them unusable. How can you stop bot attacks? With so much at risk, stopping bot attacks is vital. But some of the most typical defenses have core flaws. Common methods for stopping bot attacks include: CAPTCHAs: While CAPTCHAs can protect online systems from bot incursions, they can also create friction with the user process. Firewalls: To stop DDoS attacks, companies might reduce attack points by utilizing firewalls or restricting direct traffic to sensitive infrastructures like databases.4 Blocklists: These can prevent IPs associated with attacks from accessing your system entirely. Multifactor authentication (MFA): MFA requires two forms of identification or more before granting access to an account. Password protection: Password managers can ensure employees use strong passwords that are different for each access point. While the above methods can help, many simply aren't enough, especially for larger companies with many points of potential attacks. A piecemeal approach can also lead to friction on the user's side that may turn potential clients away. Our 2024 Identity and Fraud Report revealed that up to 38 percent of U.S. adults stopped creating a new account because of the friction they encountered during the onboarding process. And often, this friction is in place to try to stop fraudulent access. Incorporating behavioral analytics to combat attacks Another effective way to enhance bot detection is through the use of behavioral analytics. This technology helps track user activity and identify patterns that may suggest malicious bot behavior. By analyzing aspects such as typing speed, mouse movement and the way users interact with websites, businesses can gain real-time insights into whether a visitor is human or a bot. Behavioral analytics in fraud uses machine learning and advanced algorithms to continuously monitor and refine user behavior patterns. This allows businesses to identify bot attacks more accurately and prevent them before they cause harm. By analyzing real-time behaviors, such as how fast someone enters information or their browsing habits, businesses can flag suspicious activity that traditional methods might miss. Why partner with Experian? What companies need is fraud and bot protection with a positive customer experience. We provide account takeover fraud prevention solutions that can help protect your company from bot attacks, fraudulent accounts and other malicious attempts to access your sensitive data. Experian's approach embodies a paradigm shift where fraud detection increases efficiency and accuracy without sacrificing customer experience. We can help protect your company from bot attacks, fraudulent accounts and other malicious attempts to access your sensitive data. Learn more This article includes content created by an AI language model and is intended to provide general information. 1"Bad bot traffic accounts for nearly 30% of APAC internet traffic," SMEhorizon, June 13, 2023. https://www.smehorizon.com/bad-bot-traffic-accounts-for-nearly-30-of-apac-internet-traffic/2"What is a bot?" AWS. https://aws.amazon.com/what-is/bot/3Nield, David. "How ChatGPT — and bots like it — can spread malware," Wired, April 19, 2023. https://www.wired.com/story/chatgpt-ai-bots-spread-malware/4"What is a DDoS attack?" AWS. https://aws.amazon.com/shield/ddos-attack-protection/

This article was updated on February 21, 2024. With the rise of technology and data analytics in the financial industry today, it's no longer enough for companies to rely solely on traditional marketing methods. Data-driven marketing insights provide a more sophisticated and comprehensive view of shifting customer preferences and behaviors. With this in mind, this blog post will highlight the importance of data-driven marketing insights, particularly for financial institutions. The importance of data-driven marketing insights 30% of companies say poor data quality is a key challenge to delivering excellent customer experiences. Today’s consumers want personalized experiences built around their individual needs and preferences. Data-driven marketing insights can help marketers meet this demand, but only if it is fresh and accurate. When extending firm credit offers to consumers, lenders must ensure they reach individuals who are both creditworthy and likely to respond. Additionally, their message must be relevant and delivered at the right time and place. Without comprehensive data insights, it can be difficult to gauge whether a consumer is in the market for credit or determine how to best approach them. READ: Case study: Deliver timely and personalized credit offers The benefits of data-driven marketing insights By drawing data-driven marketing insights, you can reach and engage the best customers for your business. This means: Better understanding current and potential customers To increase response and conversion rates, organizations must identify high-propensity consumers and create personalized messaging that resonates. By leveraging customer data that is valid, fresh, and regularly updated, you’ll gain deeper insights into who your customers are, what they’re looking for and how to effectively communicate with them. Additionally, you can analyze the performance of your campaigns and better predict future behaviors. Utilizing technology to manage your customer data With different sources of information, it’s imperative to consolidate and optimize your data to create a single customer view. Using a data-driven technology platform, you can break down data silos by collecting and connecting consumer information across multiple sources and platforms. This way, you can make data available and accessible when and where needed while providing consumers with a cohesive experience across channels and devices. Monitoring the accuracy of your data over time Data is constantly changing, so implementing processes to effectively monitor and control quality over time is crucial. This means leveraging data quality tools that perform regular data cleanses, spot incomplete or duplicated data, and address common data errors. By monitoring the accuracy of your data over time, you can make confident decisions and improve the customer experience. Turning insights into action With data-driven marketing insights, you can level up your campaigns to find the best customers while decreasing time and dollars wasted on unqualified prospects. Visit us to learn more about how data-driven insights can power your marketing initiatives. Learn more Enhance your marketing strategies today This article includes content created by an AI language model and is intended to provide general information.

Developing machine learning (ML) credit risk models can be more challenging than traditional credit risk modeling approaches. But once deployed, ML models can increase automation and expand a lender’s credit universe. For example, by using ML-driven credit risk models and combining traditional credit data with transactional bank data, a type of alternative credit data* , some lenders see a Gini uplift of 60 to 70 percent compared to a traditional credit risk model.1 New approaches to model operations are also helping lenders accelerate their machine learning model development processes and go from collecting data to deploying a new model in days instead of months. READ MORE: Getting AI-driven decisioning right in financial services What is machine learning model development? Machine learning model development is what happens before the model gets deployed. It's often broken down into several steps. Define the problem: If you’re building an ML credit risk model, the problem you may be trying to solve is anticipating defaults, improving affordability for borrowers or expanding your lending universe by scoring more thin-file and previously unscorable consumers. Gather, clean and stage data: Identify helpful data sources, such as internal, credit bureau and alternative credit data. The data will then need to be consolidated, structured, labeled and categorized. Machine learning can be useful here as well, as ML models can be trained to label and categorize raw data. Feature engineering: The data is then analyzed to identify the individual variables and clusters of variables that may offer the most lift. Features that may directly or unintentionally create bias should be removed or limited. Create the model: Deciding which algorithms and techniques to use when developing a model can be part art and part science. Because lenders need to be able to explain the decisions they make to consumers and regulators, many lenders build model explainability into new ML-driven credit risk models. Validate and deploy: New models are validated and rigorously tested, often as challengers to the existing champion model. If the new model can consistently outperform, it may move on to production. The work doesn’t stop once a model is live — it needs to be continuously monitored for drift, and potentially recalibrated or replaced with a new model. About 10 percent of lenders use tools to automatically alert them when their models start to drift. But around half make a point of checking deployed models for drift every month or quarter.3 READ MORE: Journey of an ML Model What is model deployment? Model deployment is one of the final steps in the model lifecycle — it’s when you move the model from development and validation to live production. New models can be deployed in various ways, including via API integration and cloud service deployment using public, private or hybrid architecture. However, integrating a new model with existing systems can be challenging. About a third (33 percent) of consumer lending organizations surveyed in 2023 said it took them one to two months for model deployment-related activities. A little less (29 percent) said it took them three to six months. Overall, it often takes up to 15 months for the entire development to deployment process — and 55 percent of lenders report building models that never get deployed.2 READ MORE: Accelerating the Model Development and Deployment Lifecycle Benefits of deploying machine learning credit risk models Developing, deploying, monitoring and recalibrating ML models can be difficult and costly. But financial institutions have a lot to gain from embracing the future of underwriting. Improve credit risk assessment: ML-driven models can incorporate more data sources and more precisely assess credit risk to help lenders price credit offers and decrease charge-offs. Expand automation: More precise scoring can also increase automation by reducing how many applications need to go to manual review. Increase financial inclusion: ML-models may be able to evaluate consumers who don’t have recent credit information or thick enough credit files to be scorable by traditional models. In short, ML models can help lenders make better loan offers to more people while taking on less risk and using fewer internal resources to review applications. CASE STUDY: Atlas Credit, a small-dollar lender, partnered with Experian® to develop a fully explainable machine learning credit risk model that incorporated internal data, trended data, alternative financial services data and Experian’s attributes. Atlas Credit can use the new model to make instant decisions and is expected to double its approvals while decreasing losses by up to 20 percent. How we can help Experian offers many machine learning solutions for different industries and use cases via the Experian Ascend Technology Platform™. For example, with Ascend ML Builder™, lenders can access an on-demand development environment that can increase model velocity — the time it takes to complete a new model’s lifecycle. You can configure Ascend ML Builder based on the compute you allocate and your use cases, and the included code templates (called Accelerators) can help with data wrangling, analysis and modeling. There’s also Ascend Ops™, a cloud-based model operations solution. You can use Ascend Ops to register, test and deploy custom features and models. Automated model monitoring and management can also help you track feature and model data drift and model performance to improve models in production. Learn more about our machine learning and model deployment solutions *When we refer to “Alternative Credit Data,” this refers to the use of alternative data and its appropriate use in consumer credit lending decisions, as regulated by the Fair Credit Reporting Act. Hence, the term “Expanded FCRA Data” may also apply and can be used interchangeably. 1. Experian (2023). Raising the AI Bar 2. Experian (2023). Accelerating Model Velocity in Financial Institutions 3. Ibid.

It's 2024, and it has never been easier to buy a car in person or online, but automobiles are not quite as affordable as prior to the pandemic. While everyone is looking for the best car deal, some folks are pushing it too far and are falling for auto scams. What is auto lending fraud? Fraud perpetrators are drawn to sectors they perceive as highly lucrative. The accessibility of online vehicle financing and purchasing, coupled with the substantial financial magnitude associated with automotive transactions, renders the auto industry an optimal avenue for cash-out endeavors. Auto lending fraud refers to deceptive or fraudulent activities related to obtaining or processing auto finance. This can involve various schemes aimed at misleading lenders, financial institutions, or individuals involved in the lending process. Criminal networks now operate on social media sites like Facebook and Telegram, offering a unique car buying service using synthetic identities. They create synthetic identities, finance cars with no down payment, and deliver vehicles to addresses chosen by buyers. The process involves selecting a car online, sending a small amount of dollars and a photo against a white background, and receiving a fake driver's license. Those networks claim to exploit car sites' policies successfully. While appealing to those in urgent need of a car, the service poses significant risks as the synthetic identity may be used for other fraudulent activities beyond car purchase. Who is at risk? Everyone involved in the car buying process is at risk of falling victim to auto loan fraud. Car buyers looking to secure financing, as well as lenders, need to be aware of the potential red flags and take necessary precautions to safeguard their interests. Thieves leverage the internet and electronic transactions to perpetrate auto loan fraud. While the growth of online commerce has improved many aspects of trade, it has also made personally identifiable information and financial details vulnerable to data breaches. Unscrupulous individuals can gain unauthorized access to such information, providing the foundation for various identity theft schemes. The internet also facilitates the creation of seemingly legitimate documents that support auto loan fraud. Online services exist to help fraudsters fabricate income statements and fake employment verification from fictitious companies. This trend has made auto loan fraud an increasingly popular method for acquiring vehicles with minimal cash and risk. Another auto loan fraud trend is the increased use of CPN (Credit Privacy Number). Credit Repair firms introduced a novel strategy targeting consumers — the CPN (Credit Privacy Number). Marketed as a nine-digit alternative to a Social Security Number (SSN), CPNs are purportedly usable for obtaining credit. However, it is crucial to note that utilizing a CPN for credit applications constitutes a criminal offense, potentially leading to legal consequences, and car dealerships should not accept them. Detecting auto loan fraud There are several types of auto loan fraud worth noting to better understand the landscape: Income fabrication: Prospective buyers may falsify their income details to qualify for a larger loan or better terms. Lenders should verify income using documents like pay stubs, tax returns, or bank statements and watch out for inconsistencies. Employment misrepresentation: Applicants could lie about their job titles or employment status. Lenders should verify employment details through HR departments or by directly contacting the employer. Trade-in vehicle deception: Some individuals may overstate the value of their trade-in vehicle to secure a higher loan amount. Lenders should perform thorough appraisals or consult trusted sources to ascertain the accurate value of the trade-in. Identity fraud: Fraudsters can assume someone else's identity, commit first party fraud or create a fictitious persona to obtain an auto loan. Lenders must verify the applicant's identity using reliable identification documents and consider using identity verification tools. Forged documentation: Fraudsters may forge or alter documents like income statements, bank statements, or driver's licenses. Lenders should scrutinize documents carefully for discrepancies or signs of tampering. Straw borrower fraud: In this scenario, someone with poor credit convinces a friend or relative with better credit to front the deal, posing as the buyer. A better credit score allows for better terms or a more valuable vehicle. The actual buyer may continue to make payments to the friend, or the loan may become delinquent, negatively affecting the friend's credit score. In extreme cases, the straw buyer is part of a fraud ring, and the vehicle has already been sold in a foreign market. Synthetic identity fraud: Data breaches providing personally identifying information enable identity theft schemes. Perpetrators use illicitly acquired information to create false borrower profiles that appear authentic. These profiles typically have excellent credit, a social security number, an affluent home address, stable employment, and other attributes that make them seem like desirable borrowers. However, a detailed investigation reveals subtle inconsistencies indicative of high risk. How to prevent auto loan fraud To combat auto loan fraud and protect profitability, auto lenders can leverage technological advancements. By applying analytics and machine learning to millions of loan applications and histories, you can identify fraudulent patterns and inconsistencies. Machine learning can determine the type of suspected fraud and provide a confidence factor to guide further investigation and verification. Additionally, you should: Conduct thorough background checks on prospective buyers and verify their personal information and documents. and verify their personal information and documents. Implement a comprehensive loan underwriting process that includes income verification, employment verification, and collateral evaluation. Educate employees about common fraud schemes, warning signs, and best practices to ensure they remain vigilant during loan applications. Foster a culture of cooperation with local law enforcement agencies, sharing information about suspected fraudsters to help prevent future incidents. It is important for individuals and businesses to be vigilant and report any suspicious activity. Car dealerships and financial institutions work to prevent fraud through proper identification verification, credit checks, and adherence to legal and ethical standards. If you suspect fraudulent activity or identity theft, it is crucial to report it to the appropriate authorities immediately. Gearing-up Taking advantage of the latest fintech capabilities, such as cloud-based loan origination that integrates analytics, machine learning, and automated verification services, can significantly reduce the likelihood of fraudulent applications becoming another auto lending fraud statistic. By combining the best data with our automated ID verification checks, Experian helps you safeguard your business and onboard customers efficiently. Our best-in-class solutions employ device recognition, behavioral biometrics, machine learning, and global fraud databases to spot and block suspicious activity before it becomes a problem. Learn more about our automotive fraud prevention solutions *This article includes content created by an AI language model and is intended to provide general information.

Our Econ to Action podcast series dives into the top economic trends and the implications of those trends in the market. In each episode, we explore the challenges different market segments are facing and how businesses in the segment are navigating the current economic climate. Listen to our host, Josee Farmer, Economic Analyst, discuss these topics with other Experian experts. In a special episode of Econ to Action to commemorate the start of the new year, Josee is joined by three market experts to discuss the 2024 forecast. The experts discuss the broader U.S. economic forecast, according to the Federal Reserve’s SEP (Summary of Economic Projections), as well as the forecasts for the mortgage, collections and national bank market segments. Shawn Rife, Client Executive, returns to Econ to Action with more collections insights, along with new guests Kendall Hellman, Senior Account Executive, Strategic Sales and Rob Rollo, Senior Account Executive, Strategic Mortgage Sales. Watch our first video episode and learn how the 2024 forecast will affect the market. Be sure to go back and catch up on previous episodes on our Econ to Action podcast hub and visit Experian Edge for our latest economic, credit and market insights.

Spoiler alert: Gen AI is everywhere, including the top of Experian’s list of fraud trends 2024. “The speed and complexity of fraud attacks due to new technology and sophisticated fraudsters is leaving both businesses and consumers at risk in 2024,” said Kathleen Peters, chief innovation officer at Experian Decision Analytics in North America. “At Experian, we’re constantly innovating to deliver data-driven solutions to help our customers fight fraud and to protect the consumers they serve.” To deter fraudulent activity in 2024, businesses and consumers must get tactical for their fraud fighting strategies. And for businesses, the need for more sophisticated fraud protection solutions leveraging data and technology is greater than ever before. Experian suggests consumers and businesses watch out for these big five rounding out our fraud trends 2024. Generative AI: Generative AI accelerates DIY fraud: Experian predicts fraudsters will use generative AI to accelerate “do-it-yourself” fraud ranging from deepfake content – think emails, voice and video – as well as code creation to set up scam websites. A previous blog post of ours highlighted four types of generative AI used for fraud, including fraud automation at scale, text content generation, image and video manipulation and human voice generation. The way around it? Fight AI fraud with AI as part of a multilayered fraud prevention solution. Fraud at bank branches: Bank branches are making a comeback. A growing number of consumers prefer visiting bank branches in person to open new accounts or get financial advice with the intent to conduct safer transactions. However, face-to-face verification is not flawless and is still susceptible to human error or oversight. According to an Experian report, 85% of consumers report physical biometrics as the most trusted and secure authentication method they’ve recently encountered, but the measure is only currently used by 32% of businesses to detect and protect against fraud. Retailers, beware: Not all returns are as they appear. Experian predicts an uptick in cases where customers claim to return their purchases, only for the business to receive an empty box in return. Businesses must be vigilant with their fraud strategy in order to mitigate risk of lost goods and revenue. Synthetic identity fraud will surge: Pandemic-born synthetic identities may have been dormant, but now have a few years of history, making it easier to elude detection leading to fraudsters using those dormant accounts to “bust out” over the next year. Cause-related and investment deception: Fraudsters are employing new methods that strike an emotional response from consumers with cause-related asks to gain access to consumers’ personal information. Experian predicts that these deceptive cause-related methods will surge in 2024 and beyond. How businesses and consumers feel about fraud in 2024 According to an Experian report, over half of consumers feel they’re more of a fraud target than a year ago and nearly 70% of businesses report that fraud losses have increased in recent years. Business are facing mounting challenges – from first-party fraud and credit washing to synthetic identity and the yet-to-be-known impacts generative AI may have on fraud schemes. Synthetic identity fraud has been mentioned in multiple Experian Fraud Forecasts and the threat is ever growing. As technology continues to enhance consumers’ connectedness, it also heightens the stakes for various fraud attacks. As highlighted by this list of fraud trends 2024, the ways that fraudsters are looking to deceive is increasing from all angles. “Now more than ever, businesses need to implement a multilayered approach to their identity verification and fraud prevention strategies that leverages the latest technology available,” said Peters. Consumers are increasingly at risk from sophisticated fraud schemes. Increases in direct deposit account and check fraud, as well as advanced technologies like deepfakes and AI-generated phishing emails, put consumers in a precarious position. The call to action for consumers is to remain vigilant of seemingly authentic interactions. Experian can help with your fraud strategy To learn more about Experian’s fraud prevention solutions, please visit https://www.experian.com/business/solutions/fraud-management. Download infographic Watch Future of Fraud webinar

As a community bank or credit union, your goal is to provide personalized care and attention to your customers and members while effectively managing regulatory requirements and operational efficiency. By incorporating tools such as income and employment verification, you can streamline the approval process for both account holders and prospects. With the ability to validate their information in seconds, you'll be able to make well-informed decisions faster and accelerate conversion. In this blog post, we will explore the empowering impact of income and employment verification on financial institutions. Better Data, Better Decisions Choosing a verification partner with an instant employer payroll network allows financial institutions to access reliable and up-to-date income and employment information for confident decision-making. With accurate and timely data at their fingertips, you can gain a deeper understanding of your account holders’ capacity to pay, a critical component to assessing overall financial health. This not only helps mitigate risk but also helps you serve your customers and members more effectively. There are additional benefits to partnering with a verification solution provider that is also a Credit Reporting Agency (CRA) offering FCRA-compliant technologies. These organizations are well versed in compliance matters and can help you more effectively mitigate risk. Streamline Approval Times and Remove Friction When developing your verification process, it is advantageous to adopt a waterfall or multi-step approach that encompasses instant verification, permissioned verification, and, as a last resort, manual verification. This tiered approach will significantly reduce approval times, manage costs effectively, and streamline the approval process. Instant verification relies on advanced technology to provide swift and efficient results. In cases where instant verification is unavailable, the process seamlessly transitions to permissioned verification, where explicit consent is obtained from individuals to access their payroll data directly from their respective providers. Lastly, manual verification involves collecting payroll and employment documents, which is a more time-consuming and costly process. By implementing this comprehensive approach, you can enhance the efficiency and effectiveness of your verification process while maintaining the integrity of the results. A Flexible Solution Community banks and credit unions are integral to the lending industry. It is crucial for them to select a versatile verification solution that can keep pace with the approval speed of both regional and large banks. Given that community banks and credit unions operate in smaller geographic regions compared to larger institutions, it is imperative for them to have a verification solution that is versatile and can be applied across their entire spectrum of loan offerings, including mortgage loans, automotive loans, credit cards, home equity loans, and consumer loans. This adaptability enables community banks and credit unions to consistently serve their account holders and enhances their ability to compete effectively with larger financial institutions. With a robust verification solution in place, community banks and credit unions can confidently navigate the complexities of the lending landscape and deliver exceptional results for their valued account holders. World-Class Service and Support To ensure a seamless verification journey, community banks and credit unions should choose a solution provider that delivers exceptional service and support. From the initial onboarding process and comprehensive training to ongoing troubleshooting and guidance, a dedicated and knowledgeable support team becomes indispensable in establishing a successful verification process. Having hands-on training and support not only instills peace of mind but also empowers community-focused financial institutions to consistently provide a high level of personalized service, fostering trust and loyalty among their customers and members. By investing in a robust support system, community banks and credit unions can confidently navigate the verification landscape and stay ahead in an ever-evolving financial industry, reinforcing their commitment to delivering an outstanding experience to their communities. As a longstanding leader in the financial industry, Experian understands the unique challenges faced by community banks and credit unions. Our verification solution, Experian VerifyTM, provides accurate, efficient, and compliant income and employment verification services. With Experian Verify, community focused financial institutions can navigate the complexities of income and employment verification with ease, achieving new levels of efficiency and success. To learn more about how Experian Verify can benefit your bank or credit union, we invite you to visit our website and schedule a personalized demo. Together, let's unlock the potential of income and employment verification and elevate your financial institution to new heights of success. Learn more

This article was updated on February 13, 2024. Traditional credit data has long been a reliable source for measuring consumers' creditworthiness. While that's not changing, new types of alternative credit data are giving lenders a more complete picture of consumers' financial health. With supplemental data, lenders can better serve a wider variety of consumers and increase financial access and opportunities in their communities. What is alternative credit data? Alternative credit data, also known as expanded FCRA-regulated data, is data that can help you evaluate creditworthiness but isn't included in traditional credit reports.1 To comply with the Fair Credit Reporting Act (FCRA), alternative credit data must be displayable, disputable and correctable. Lenders are increasingly turning to new types and sources of data as the use of alternative credit data becomes the norm in underwriting. Today, lenders commonly use one or more of the following: Alternative financial services data: Alternative financial services (AFS) credit data can include information on consumers' use of small-dollar installment loans, single-payment loans, point-of-sale financing, auto title loans and rent-to-own agreements. Consumer permission data: With a consumer's permission, you can get transactional and account-level data from financial accounts to better assess income, assets and cash flow. The access can also give insight into payment history on non-traditional accounts, such as utilities, cell phone and streaming services. Rental payment history: Property managers, electronic rent payment services and rent collection companies can share information on consumers' rent payment history and lease terms. Full-file public records: Local- and state-level public records can tell you about a consumer's professional and occupational licenses, education, property deeds and address history. Buy Now Pay Later (BNPL) data: BNPL tradeline and account data can show you payment and return histories, along with upcoming scheduled payments. It may become even more important as consumers increasingly use this new type of point-of-sale financing. By gathering more information, you can get a deeper understanding of consumers' creditworthiness and expand your lending universe. From market segmentation to fraud prevention and collections, you can also use alternative credit data throughout the customer lifecycle. READ: 2023 State of Alternative Credit Data Report Challenges in underwriting today While unemployment rates are down, high inflation, rising interest rates and uncertainty about the economy are impacting consumer sentiment and the lending environment.2 Additionally, lenders may need to shift their underwriting approaches as pandemic-related assistance programs and loan accommodations end. Lenders may want to tighten their credit criteria. But, at the same time, consumers are becoming accustomed to streamlined application processes and responses. A slow manual review could lead to losing customers. Alternative credit data can help you more accurately assess consumers' creditworthiness, which may make it easier to identify high-risk applicants and find the hidden gems within medium-risk segments. Layering traditional and alternative credit data with the latest approaches to model building, such as using artificial intelligence, can also help you implement precise and predictive underwriting strategies. Benefits of using alternative data for credit underwriting Using alternative data for credit underwriting — along with custom credit attributes and automation — is the modern approach to a risk-based credit approval strategy. The result can offer: A greater view of consumer creditworthiness: Personal cash flow data and a consumer's history of making (or missing) payments that don't appear on traditional credit reports can give you a better understanding of their financial position. Improve speed and accuracy of credit decisions: The expanded view helps you create a more efficient underwriting process. Automated underwriting tools can incorporate alternative credit data and attributes with meaningful results. One lender, Atlas Credit, worked with Experian to create a custom model that incorporated alternative credit data and nearly doubled its approvals while reducing risk by 15 to 20 percent.3 Increase financial inclusion: There are 28 million American adults who don't have a mainstream credit file and 21 million who aren't scoreable by conventional scoring models.4 With alternative credit data, you may be able to more accurately assess the creditworthiness of adults who would otherwise be deemed thin file or unscorable. Broadening your pool of applications while appropriately managing risk is a measurable success. What Experian builds and offers Experian is continually expanding access to expanded FCRA-regulated data. Our Experian RentBureau and Clarity Services (the leading source of alternative financial credit data) have long given lenders a more complete picture of consumers' financial situation. Experian also helps lenders effectively use these new types of data. You can also incorporate the data into your proprietary marketing, lending and collections strategies. Experian is also using alternative credit data for credit scoring. The Lift Premium™ model can score 96 percent of U.S. adults — compared to the 81 percent that conventional models can score using traditional data.5 The bottom line Lenders have been testing and using alternative credit data for years, but its use in underwriting may become even more important as they need to respond to changing consumer expectations and economic uncertainty. Experian is supporting this innovation by expanding access to alternative data sources and helping lenders understand how to best use and implement alternative credit data in their lending strategies. Learn more 1When we refer to “Alternative Credit Data," this refers to the use of alternative data and its appropriate use in consumer credit lending decisions, as regulated by the Fair Credit Reporting Act. Hence, the term “Expanded FCRA Data" may also apply and can be used interchangeably. 2Experian (2024). State of the Economy Report 3Experian (2020). OneAZ Credit Union [Case Study] 4Oliver Wyman (2022). Financial Inclusion and Access to Credit [White Paper] 5Ibid.
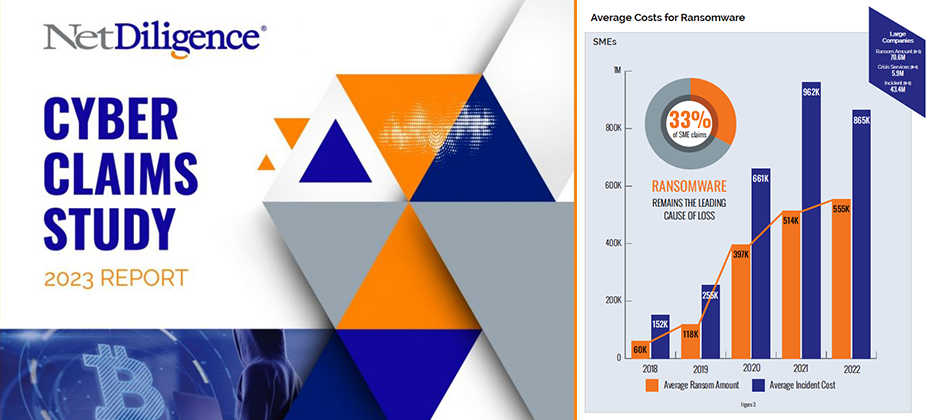
Review of Findings & Front-line Insights Panel Participants: Richard Goldberg (Moderator) – Constangy, Brooks, Smith & Prophete, LLP Michael Bruemmer – Experian Sean Renshw – RSM US, LLP Mark Greisiger – NetDiligence About NetDiligence Cyber Claims Study It is NetDiligence’s 13th year of doing this Cyber Claims Study. A total of 9,028 claims were analyzed during the past five years 2018-2022.An observation from the over 9,000 Cyber Claims (5000 of which are brand new claims this past year in 2023) analyzed is while many of the categories over the last five years have remained the same, the data has changed, sometimes dramatically. About Experian We provide call center coverage, notification coverage, as well as, identity theft protection, and all the consumer resolutions that go along with it for about 5000 data breaches every year, and I was delighted to be on the panel. Key Insights Experian has proudly sponsored the annual NetDiligence Cyber Claims Study for three years. During this time, I’ve witnessed companies adapt and transform their operations to confront the growing tide of cyber threats. The evolution of their infrastructure to anticipate and respond to these challenges has been remarkable and necessary. However, despite my front-row seat in this fast-changing landscape, the results of each study never fail to surprise and intrigue me. The insights from the latest study, conducted in 2023, continue to shape our understanding of the evolving cyber landscape. Ransomware’s Dominance Mark kicked off the discussion by shedding light on the escalating costs associated with cyber incidents. In 2022, the average incident cost for SME organizations remained stable at $169,000 (similar to the combined five-year window from 2018 to 2022 at about 175,000). However, there was a substantial increase for large companies, reaching $20.3 million in 2022 (and if you look at the five-year average, it was about 13 million). This surge raised eyebrows and set the stage for a deep dive into ransomware, a leading cause of concern. Examining Ransomware Trends The conversation swiftly shifted to ransomware, a pervasive threat in the cyber insurance landscape. As I stated, at Experian we see a correlation between the rise in ransomware and third-party breaches. Most of the industry experts on the panel participate in a Ransomware Advisory Group together. Mark brought up a good insight from our advisory group on the brazen tactics employed by threat actors lately, showcasing their intimate knowledge of the cyber insurance world. Business Sectors Under Siege Richard and Sean added to the discussion the top ten business sectors affected by ransomware, with professional services leading the pack. The impact on technology, with a payout of $830,000, stood out as well. Beyond Ransomware The conversation broadened to encompass other types of losses, such as social engineering and business email compromise. The focus on business interruption emerged as a key concern for cyber insurance claims, with the industry grappling with criminal acts versus non-criminal acts. Looking Ahead As the discussion unfolded, industry experts, including myself, expressed eagerness to anticipate the future cyber landscape. Predictions range from the industry mutating to the emergence of new players in the nation-state game. The role of artificial intelligence and innovative solutions from new vendors becomes a focal point of interest. In conclusion, the NetDiligence Cyber Claims Study 2023 Report paints a vivid picture of the challenges and transformations within the cyber insurance domain. The increasing sophistication of threat actors, coupled with evolving business strategies, sets the stage for continuous adaptation and innovation in the fight against cyber threats. As we look ahead, the resilience of businesses and the collaboration between industry stakeholders will play a pivotal role in shaping the cybersecurity landscape. I invite you to access the report and view the discussion replay for a deeper understanding of the challenges and transformations within the cyber insurance claims domain. Get NetDiligece Cyber Claims Study resources on-demand now! Download the report Watch the webinar NetDiligence’s latest Cyber Claims Study and Webinar, sponsored by Experian Data Breach, is available on-demand. This report serves as a resounding call to action, prompting businesses to ready themselves against cyber threats. Dive in to get insights and stay one step ahead of cyber adversaries.

This article was updated on February 12, 2024. The Buy Now, Pay Later (BNPL) space has grown massively over the last few years. But with rapid growth comes an increased risk of fraud, making "Buy Now, Pay Never" a crucial fraud threat to watch out for in 2024 and beyond. What is BNPL? BNPL, a type of short-term financing, has been around for decades in different forms. It's attractive to consumers because it offers the option to split up a specific purchase into installments rather than paying the full total upfront. The modern form of BNPL typically offers four installments, with the first payment at the time of purchase, as well as 0% APR and no hidden fees. According to an Experian survey, consumers cited managing spending (34%), convenience (31%), and avoiding interest payments (23%) as main reasons for choosing BNPL. Participating retailers generally offer BNPL at point-of-sale, making it easy for customers to opt-in and get instantly approved. The customer then makes a down payment and pays off the installments from their preferred account. BNPL is on the rise The fintech and online-payment-driven world is seeing a rise in the popularity of BNPL. According to Experian research, 3 in 4 consumers have used BNPL in 2023, with 11% using BNPL weekly to make purchases. The interest in BNPL also spans generations — 36% of Gen Z, 43% of Millennials, 32% of Gen X, and 12% of Baby Boomers have used this payment method. The risks of BNPL While BNPL is a convenient, easy way for consumers to plan for their purchases, experts warn that with lax checkout and identity verification processes it is a target for digital fraud. Experian predicts an uptick in three primary risks for BNPL providers and their customers: identity theft, first-party fraud, and synthetic identity fraud. WATCH: Fraud and Identity Challenges for Fintechs Victims of identity theft can be hit with charges from BNPL providers for products they have never purchased. First-party and synthetic identity risks will emerge as a shopper's buying power grows and the temptation to abandon repayment increases. Fraudsters may use their own or fabricated identities to make purchases with no intent to repay. This leaves the BNPL provider at the risk of unrecoverable monetary losses and can impact the business' risk tolerance, causing them to narrow their lending band and miss out on properly verified consumers. An additional risk lies with fraudsters who may leverage account takeover to gain access to a legitimate user's account and payment information to make unauthorized purchases. READ: Payment Fraud Detection and Prevention: What You Need to Know Mitigating BNPL risks Luckily, there are predictive credit, identity verification, and fraud prevention tools available to help businesses minimize the risks associated with BNPL. Paired with the right data, these tools can give businesses a comprehensive view of consumer payments, including the number of outstanding BNPL loans, total BNPL loan amounts, and BNPL payment status, as well as helping to detect and apply the relevant treatment to different types of fraud. By accurately identifying customers and assessing risk in real-time, businesses can make confident lending and fraud prevention decisions. To learn more about how Experian is enabling the protection of consumer credit scores, better risk assessments, and more inclusive lending, visit us or request a call. And keep an eye out for additional in-depth explorations of our Future of Fraud Forecast. Learn more Future of Fraud Forecast

Companies depend on quality information to make decisions that move their business objectives forward while minimizing risk exposure. And in today’s modern, tech-driven, innovation-led world, there’s more information available than ever before. Expansive datasets from sources, both internal and external, allow decision-makers to leverage a wide range of intelligence to fuel how they plan, forecast and set priorities. But how can business leaders be sure that their data is as robust, up-to-date and thorough as they need — and, most importantly, that they’re able to use it to its fullest potential? That’s where the power of advanced analytics comes in. By making use of cutting-edge datasets and analytics insights, businesses can stay on the vanguard of business intelligence and ahead of their competitors. What is advanced analytics? Advanced analytics is a form of business intelligence that takes full advantage of the most modern data sources and analytics tools to create forward-thinking analysis that can help businesses make well-informed, data-driven decisions that are tailored to their needs. Simply put, advanced analytics is an essential component of any proactive business strategy that aims to maximize the future potential of both customers and campaigns. These advanced business intelligence and analytics solutions help leaders make profitable decisions no matter the state of the current economic climate. They use both traditional and non-traditional data sources to provide businesses with actionable insights in the formats best suited to their needs and goals. One key aspect of advanced analytics is the use of AI analytics solutions. These efficient and effective tools help businesses save time and money by harnessing the power of cutting-edge technologies and deploying them in optimal use-case scenarios. These AI and machine-learning solutions use a wide range of tools, such as neural network methodologies, to help organizations optimize their allocation of resources, expediting and automating some processes while creating valuable insights to help human decision-makers navigate others. Benefits of advanced analytics Traditional business intelligence tends to be limited by the scope and quality of available data and ability of analysts to make use of it in an effective, comprehensive way. Modern business intelligence analytics, on the other hand, integrates machine learning and analytics to maximize the potential of data sets that, in today's technology-driven world, are often overwhelmingly large and complex: think not just databases of customer decisions and actions but behavioral data points tied to online and offline activity and the internet of things. What's more, advanced analytics does this in a way that's accessible to an entire organization — not just those who know their way around data, like IT departments and trained analysts. With the right advanced analytics solution, decision-makers can access convenient cloud-based dashboards designed to give them the information they want and need — with no clutter, noise or confusing terminology. Another key advantage of advanced analytics solutions is that they don't just analyze data — they optimize it, too. Advanced analytics offers the ability to clean up and integrate multiple data sets to remove duplicates, correct errors and inaccuracies and standardize formats, leading to high-quality data that creates clarity, not confusion. The result? By analyzing and identifying relationships across data, businesses can uncover hidden insights and issues. Advanced analytics also automate some aspects of the decision-making process to make workflows quicker and nimbler. For example, a business might choose to automate credit scoring, product recommendations for existing customers or the identification of potential fraud. Reducing manual interventions translates to increased agility and operational efficiency and, ultimately, a better competitive advantage. Use cases in the financial services industry Advanced analytics gives businesses in the financial world the power to go deeper into their data — and to integrate alternative data sources as well. With predictive analytics models, this data can be transformed into highly usable, next-level insights that help decision-makers optimize their business strategies. Credit risk, for instance, is a major concern for financial organizations that want to offer customers the best possible options while ensuring their credit products remain profitable. By utilizing advanced analytics solutions combined with a broad range of datasets, lenders can create highly accurate credit risk scores that forecast future customer behavior and identify and mitigate risk, leading to better lending decisions across the credit lifecycle. Advanced analytics solutions can also help businesses problem-solve. Let's say, for instance, that uptake of a new loan product has been slower than desired. By using business intelligence analytics, companies can determine what factors might be causing the issue and predict the tweaks and changes they can make to improve results. Advanced analytics means better, more detailed segmentation, which allows for more predictive insights. Businesses taking advantage of advanced analytics services are simply better informed: not only do they have access to more and better data, but they're able to convert it into actionable insights that help them lower risk, better predict outcomes, and boost the performance of their business. How we can help Experian offers a wide range of advanced analytics tools aimed at helping businesses in all kinds of industries succeed through better use of data. From custom machine learning models that help financial institutions assess risk more accurately to self-service dashboards designed to facilitate more agile responses to changes in the market, we have a solution that's right for every business. Plus, our advanced analytics offerings include a vast data repository with insights on 245 million credit-active individuals and 25 million businesses, as well as the industry's largest alternative data set from non-traditional lenders. Ready to explore? Click below to learn about our advanced analytics solutions. Learn more

This article was updated on February 6, 2024. Lenders looking to gain a competitive edge need to improve their credit underwriting process in the coming years. The most obvious developments are the advances in artificial intelligence (AI) — machine learning in particular — the increased available computing capacity, and access to vast amounts of data. But when it comes to credit underwriting models, those are tools you can use to reach your goals, not a strategy for success. The evolution of credit underwriting Credit underwriters have had the same goal for millennia — assess the creditworthiness of a borrower to determine whether to offer them a loan. But the process has changed immensely, and the pace of change has recently increased. Fewer than 50 years ago, an underwriter might consider an applicant's income, occupation, marital status, and sex to make a decision. The Equal Credit Opportunity Act didn't pass until 1974. And it wasn't expanded to prohibit lending discrimination based on other factors, such as color, age, and national origin, until two years later. Regulatory changes can have an immediate and immense impact on credit underwriting, but there were also slower changes developing. As credit bureaus centralized and computers became more readily available, credit decisioning systems offered new insights. The systems could segment groups and help lenders make more complex and profitable decisions at scale, such as setting risk-appropriate credit limits and terms. INFOGRAPHIC: Data-driven decisioning journey map With access to more data and computing power, lenders get a more complete picture of applicants and their current customers. Technological advances also lead to automated decisions, which can improve lenders' workflows and customer satisfaction. In the late 2000s, fintech lenders entered the scene and disrupted the ecosystem with a completely online underwriting and funding process. More recently, AI and machine learning started as buzzwords, but quickly became business necessities. In fact, 66% of businesses believe advanced analytics, including machine learning and artificial intelligence, are going to rapidly change the way they do business.1 The latest explainable machine learning models can increase automation and efficiency while outperforming traditional modeling approaches. Access to increased computing power is, once again, helping power this shift.2 But it's also only possible because of the lenders access to alternative credit data.* WATCH: Why Advanced Analytics is Now Available for All Future-proofing your credit underwriting strategy Today's leading lenders use innovative technology and comprehensive data to improve their credit decisioning — including fraud detection, underwriting, account management, and collections. To avoid getting left behind, you need to consider how you can incorporate new tools and processes into your strategy. Get comfortable with machine learning models Although machine learning models have repeatedly shown they can offer performance improvements, lenders may hesitate to adopt them if they can't explain how the models work. It's smart to be cautious as so-called “black box" models generally don't pass regulatory muster — even if they can offer a greater lift. But there is a middle ground, and credit modelers use machine learning techniques to develop more effective models that are fully explainable. READ MORE: Explainability: ML and AI in credit decisioning Explore new data sources Machine learning models are great at recognizing patterns, but you need to train them on large data sets if you want to unlock their full potential. Lenders' internal data can be important, especially if they're developing custom models. But lenders should also try leveraging various types of alternative credit data to train models and more accurately assess an applicant's creditworthiness. This can include data from public records, rental payments, alternative financial services, and consumer-permissioned data. READ MORE: 2023 State of Alternative Credit Data Report Focus on financial inclusion Using new data sources can also help you more accurately understand the risk of an applicant who isn't scorable with traditional models. For example, Lift Premium™ uses machine learning and a combination of traditional consumer bureau credit data and alternative credit data to score 96 percent of U.S. consumers — 15 percent more than conventional scores.3 As a result, lenders can expand their lending universe and offer right-sized terms to people and groups who might otherwise be overlooked. Use AI to fuel automation Artificial intelligence can accelerate automation throughout the credit life cycle. Machine learning models do this within underwriting by more precisely estimating the creditworthiness of applicants. The more accurate a model is, the better it will be at identifying applicants who lenders want to approve or deny. Consider your decisioning strategy Although a machine learning model might offer more precise insight, lenders still need to set their decisioning strategy and business rules, including the cutoff points. Credit decisioning software can help lenders implement these decisions with speed, accuracy, and scalability. CASE STUDY: Experian partnered with OneAZ Credit Union to upgrade to an advanced credit decisioning platform and automate its underwriting strategy. The credit union increased load funding rates by 26 percent within one month and reduced manual reviews by 25 percent. Use underwriting as a component of strategic optimization Advanced analytics allow companies to move away from simpler rule-based decisions and toward strategies that take the business's overall goals into account. For example, lenders may be able to optimize decisions that involve competing goals — such as targets for volume and bad debt — to help the business reach its goals. Test and benchmark Underwriting is an iterative process. Lenders can use machine learning techniques to build and test challenger models and see how well they perform. You can also compare the results to industry benchmarks to see if there's likely room for more improvement. Why lenders choose Experian Lenders have used Experian's consumer and business credit data to underwrite loans for decades, but Experian is also a leader in advanced analytics. As lenders try to figure out how they'll approach underwriting in the coming years, they can partner with Experian's data scientists, who understand how to develop and deploy the latest types of compliant and explainable credit underwriting models. Experian also offers credit underwriting software and cloud-based and integrated decisioning platforms, along with modular solutions, such as access to alternative credit data, predictive attributes and scores. And lenders can explore collaborative approaches to developing ML-aided models that incorporate internal and third-party data. If you're not sure where to start, a business review can help you identify a few quick wins and create a road map for future improvements. Explore our credit decisioning solutions. * When we refer to “Alternative Credit Data," this refers to the use of alternative data and its appropriate use in consumer credit lending decisions as regulated by the Fair Credit Reporting Act (FCRA). Hence, the term “Expanded FCRA Data" may also apply in this instance and both can be used interchangeably. 1Experian (2022). Explainability: ML and AI in credit decisioning2Experian (2022). Webinar: Driving Growth During Economic Uncertainty with AI/ML Strategies 3Experian (2022). Lift Premium

Insights from the Cyber Risk Summit Beverly Hills – October 2023 Authored by Ryan Coyne I recently participated in a panel with industry experts, delving into third-party cyber risks. The panel shed light on best practices, challenges, and strategies to mitigate the impact of third-party incidents. Panel Participants: Stu Panensky (Moderator) – FisherBroyles, LLP Ryan Coyne – Experian Tom Egglestone – Resilience Mark Grazman – Fenix24 Matthew Saidel – FTI Consulting Agenda: Incident Best Practices: Collaboration & Coordination on IR Action Items Upstream Risk of Third Parties: Vendors, Suppliers & Business Partners Downstream Risk in the Policyholder Supply Chain The Cyber Risk Summit held in Beverly Hills provided valuable insights into the risks of engaging unsecured third parties. Key Takeaways Understanding the Significance Tom emphasized the longstanding nature of cyber risk exposure tied to third-party relationships. The increasing reliance on external vendors in a tech-enabled world has heightened this risk, especially with the surge in outsourcing and software adoption. Tom highlighted that, even in 2019, Gartner research indicated that 60% of surveyed companies worked with over 1000 third parties in their supply chain, setting the stage for the escalated risk environment post-pandemic. Crisis Communications in Third-Party Incidents Matt shared insights into the challenges faced when third-party incidents unfold. The necessity of involving crisis communications consultants early in the process, especially for upstream and downstream, was stressed. Preserving the right to operate and maintaining client trust amid incidents were key points Matt made.Hands-On Restoration PerspectiveMark, providing a hands-on restoration perspective, discussed the rarity of involvement at the inception of an event. His emphasis on locking down infrastructure, understanding the threat actor’s persistency, and encouraging robust backup strategies showcased the intricacies involved in restoration efforts.“Restoration efforts often kick in when patient zero is unidentified. Locking down the infrastructure and focusing on repairing affected elements are essential” – Mark Grazman, Fenix24 Notification Strategies and Legal Implications Representing Experian, I shared my perspective on notification complexities that the average consumer may not be aware of, such as notifying everyone upfront versus opt-in processes. The legal implications of notifying on behalf of others and coordinating with multiple parties. The nuanced approach to call center communication and the crucial factor of making details clear in notification letters in minimizing confusion for recipients.I want to emphasize a point I made earlier in the panel on the downstream impact of notification strategies and the need to customize communication for recipients.“For these incidents, it’s most important to minimize complexity on the notification side and minimize confusion for the recipient of your notification letter.” – Ryan Coyne, Experian Insights from an Insurance Claims Handler Tom, as an insurance claims handler, underscored the importance of understanding vendor contracts, particularly clauses related to defense and indemnity. He highlighted the need for transparency in the vendor’s incident response process, especially when the insured isn’t in control, adding a layer of complexity to communication and expectation setting. Crafting a Seamless Notification Process: Public-Private Partnerships Stu Panensky, Moderator: Public-private partnerships emerged as a recurring theme during the panel discussions. The need for collaboration between law enforcement, insurance companies, and businesses became evident. Stu emphasized the role of public-private partnerships in influencing better outcomes and impacting data protection, regulation, and litigation. The insights from the 2023 Beverly Hills Cyber Risk Summit underline the interconnected nature of cyber risks and the critical importance of proactive measures. Stakeholders are urged to adopt a collaborative approach, navigate legal complexities, and stay vigilant in the face of evolving challenges. I welcome you to watch the full discussion on-demand. Watch the panel session on-demand now