Topics

If you're looking to implement and deploy a knowledge-based authentication (KBA) solution in your application process for your online and mobile customer acquisition channels - then, I have good news for you! Here’s some of the upside you’ll see right away: Revenues (remember, the primary activities of your business?) will accelerate up Your B2C acceptance or approval rates will go up thru automation Manual review of customer applications will go down and that translates to a reduction in your business operation costs Products will be sold and shipped faster if you’re in the retail business, so you can recognize the sales revenue or net sales quicker Your customers will appreciate the fact that they can do business in minutes vs. going thru a lengthy application approval process with turnaround times of days to weeks And last but not least, your losses due to fraud will go down To keep you informed about what’s relevant when choosing a KBA vendor, here’s what separates the good KBA providers from the bad: The underlying data used to create questions should be from multiple data sources and should vary in the type of data, for example credit and non-credit Relying on public record data sources is becoming a risky proposition given recent adoption of various social media websites and various public record websites Have technology that will allow you to create a custom KBA setup that is unique to your business and business customers, and the proven support structure to help you grow your business safely Provide consulting (performance monitoring)and analytical support that will keep you ahead of the fraudsters trying to game your online environment by assuring your KBA tool is performing at optimal levels Solutions that can easily interface with multiple systems, and assist from a customer experience perspective. How are your peers in the following 3 industries doing at adopting a KBA strategy to help grow and protect their businesses? E-commerce 21% use KBA today and are satisfied with the results* 13% have KBA on roadmap and the list is growing fast* Healthcare 20% use dynamic KBA* Financial Institutions 30% combination of dynamic & static KBA* 20% dynamic KBA* What are the typical uses of KBA?* Call center Web / mobile verification Enrollment ID verification Provider authentication Eligibility *According to a 2012 report on knowledge-based authentication by Aite Group LLC Knowledge-based authentication, commonly referred to as KBA, is a method of authentication which seeks to prove the identity of someone accessing a service, such as a website. As the name suggests, KBA requires the knowledge of personal information of the individual to grant access to the protected material. There are two types of KBA: "static KBA", which is based on a pre-agreed set of "shared secrets"; and "dynamic KBA", which is based on questions generated from a wider base of personal information.

Small-business credit conditions strengthened in Q2 2013, lifting the Experian/Moody's Analytics Small Business Credit Index 2.8 points to 111.7 - the highest level since it began tracking. Consumer spending growth was modest, but steady and consumer confidence is at multiyear highs. This is a reassuring signal that consumer spending is unlikely to backtrack in the near future. Furthermore, credit quality improved for every business size, with the total share of delinquent dollars 2.4 percentage points lower than a year ago and at the lowest point on record.

According to a recent survey by freecreditscore.com™, women find financial responsibility more attractive in assessing a romantic partner (96 percent) than physical attractiveness (87 percent) or career ambition (87 percent). Men slightly favor good looks over financial responsibility (92 percent versus 91 percent); however, 20 percent of men surveyed would not marry someone with a poor credit score.

The average bankcard balance per consumer in Q2 2013 was $3,831, a 1.3 percent decline from the previous year. Consumers in the VantageScore® near prime and subprime credit tiers carried the largest average bankcard balances at $5,883 and $5,903 respectively. The super prime tier carried the smallest average balance at $1,881.

Using data from IntelliViewSM, Credit.com recently compiled a list of states with the highest average bankcard utilization rates. Alaska took first place, with an average utilization ratio of 27.73 percent. This should come as no surprise since Alaska has recently topped lists for highest credit card balances and highest revolving debt.

By: Maria Moynihan Government organizations that handle debt collection have similar business challenges regardless of agency focus and mission. Let’s face it, debtors can be elusive. They are often hard to find and even more difficult to collect from when information and processes are lacking. To accelerate debt recovery, governments must focus on optimization--particularly, streamlining how resources get used in the debt collection process. While the perception may be that it’s difficult to implement change given limited budgets, staffing constraints or archaic systems, minimal investment in improved data, tools and technology can make a big difference. Governments most often express the below as their top concerns in debt collection: Difficulty in finding debtors to collect on late tax submissions, fines or fees. Prioritizing collection activities--outbound letters, phone calls, and added steps in decisioning. Difficulty in incorporating new tools or technology to reduce backlogs or accelerate current processes. By simply utilizing right party contact data and tools for improved decisioning, agencies can immediately expose areas of greater possible ROI over others. Credit and demographic data elements like address, income models, assets, and past payment behavior can all be brought together to create a holistic view of an individual or business at a point in time or over time. Collections tools for improved monitoring, segmentation and scoring could be incorporated into current systems to improve resource allotment. Staffing can then be better allocated to not only focus on which accounts to pursue by size, but by likelihood to make contact and payment. Find additional best practices to optimize debt recovery in this guide to Maximizing Revenue Potential in the Public Sector. Be sure to check out our other blog posts on debt collection.

I don’t know about your neighborhood this past Fourth of July, but mine contained an interesting mix of different types of fireworks. From our front porch, we watched a variety of displays simultaneously: an organized professional fireworks show several miles away, our next-door neighbor setting off the “Safe and Sane” variety and the guy at the end of the street with clearly illegal ones. This made me think about how our local police approach this night. There’s no way they can investigate every report or observance of illegal fireworks as well as all of the other increased activity that occurs on a holiday. So it must come down to prioritization, resources and risk assessment. When it comes to fraud prevention, compliance and risk, businesses — much the same as the police — have a lot of ground to cover and limited resources. Consider the bureau alerts (aka high-risk conditions) on a credit report. They’re an easy, quick tool that can help mitigate risk and save money cost-effectively. When considering bureau alerts, clients commonly ask the following questions: How do I investigate all of the alerts with the limited resources I have? How should I prioritize the ones I am able to review? I usually recommend that, if possible, they incorporate a fraud risk score into their evaluation process. The job of the fraud risk score is to take a very large amount of data and put it into an easy-to-understand and actionable form. It is built to evaluate negative or risky information (at Experian, this includes bureau alerts and many other items) as well as positive or low-risk information (analysis of address, Social Security number, date of birth, and other current and historical personal information). The result is a holistic assessment rather than a binary flag, which can be tuned to resource levels, risk tolerance or other drivers. That’s always where I start. If a fraud score is not an option, then I suggest prioritizing the alerts by the most risk and the frequency of occurrence. With some light analysis, you’ll typically see that the frequency of the most risky alerts is often low, so you can be sure to review each one — or as many as possible. As the frequency of occurrence increases, you then can make decisions about which ones to review or how many of them you can handle. For example, I worked with a client recently to prioritize high-risk but low-frequency alerts. Almost all involved the Social Security number (SSN): The inquiry SSN was recorded as deceased The report contained a security statement There was a high probability that the SSN belongs to another person The best on-file SSN was recorded as deceased I would expect other organizations to have a similar prioritized risk-to-frequency ratio. However, it’s always good (and pretty easy) to make sure your data backs this up. That way, you’re making the most of your limited resources and your tools.

A recent survey of government benefit agencies shows an increased need for fraud detection technology to prevent eligibility fraud. Only 26 percent of respondents currently use fraud detection technology, and 57 percent cite false income reporting as the leading cause of fraud. Insufficient resources and difficulty integrating multiple data sources were the greatest challenges in preventing eligibility fraud.

The desire to return to portfolio growth is a clear trend in mature credit markets, such as the US and Canada. Historically, credit unions and banks have driven portfolio growth with aggressive out-bound marketing offers designed to attract new customers and members through loan acquisitions. These offers were typically aligned to a particular product with no strategy alignment between multiple divisions within the organization. Further, when existing customers submitted a new request for credit, they were treated the same as incoming new customers with no reference to the overall value of the existing relationship. Today, however, financial institutions are looking to create more value from existing customer relationships to drive sustained portfolio growth by increasing customer retention, loyalty and wallet share. Let’s consider this idea further. By identifying the needs of existing customers and matching them to individual credit risk and affordability, effective cross-sell strategies that link the needs of the individual to risk and affordability can ensure that portfolio growth can be achieved while simultaneously increasing customer satisfaction and promoting loyalty. The need to optimize customer touch-points and provide the best possible customer experience is paramount to future performance, as measured by market share and long-term customer profitability. By also responding rapidly to changing customer credit needs, you can further build trust, increase wallet share and profitably grow your loan portfolios. In the simplest sense, the more of your products a customer uses, the less likely the customer is to leave you for the competition. With these objectives in mind, financial organizations are turning towards the practice of setting holistic, customer-level credit lending parameters. These parameters often referred to as umbrella, or customer lending, limits. The challenges Although the benefits for enhancing existing relationships are clear, there are a number of challenges that bear to mind some important questions to consider: · How do you balance the competing objectives of portfolio loan growth while managing future losses? · How do you know how much your customer can afford? · How do you ensure that customers have access to the products they need when they need them · What is the appropriate communication method to position the offer? Few credit unions or banks have lending strategies that differentiate between new and existing customers. In the most cases, new credit requests are processed identically for both customer groups. The problem with this approach is that it fails to capture and use the power of existing customer data, which will inevitably lead to suboptimal decisions. Similarly, financial institutions frequently provide inconsistent lending messages to their clients. The following scenarios can potentially arise when institutions fail to look across all relationships to support their core lending and collections processes: 1. Customer is refused for additional credit on the facility of their choice, whilst simultaneously offered an increase in their credit line on another. 2. Customer is extended credit on a new facility whilst being seriously delinquent on another. 3. Customer receives marketing solicitation for three different products from the same institution, in the same week, through three different channels. Essentials for customer lending limits and successful cross-selling By evaluating existing customers on a periodic (monthly) basis, financial institutions can assess holistically the customer’s existing exposure, risk and affordability. By setting customer level lending limits in accordance with these parameters, core lending processes can be rendered more efficient, with superior results and enhanced customer satisfaction. This approach can be extended to consider a fast-track application process for existing relationships with high value, low risk customers. Traditionally, business processes have not identified loan applications from such individuals to provide preferential treatment. The core fundamentals of the approach necessary for the setting of holistic customer lending (umbrella) limits include: · The accurate evaluation of credit and default risk · The calculation of additional lending capacity and affordability · Appropriate product offerings for cross-sell · Operational deployment Follow my blog series over the next few months as we explore the essentials for customer lending limits and successful cross-selling.

There are two core fundamentals of evaluating loan loss performance to consider when generating organic portfolio growth through the setting of customer lending limits. Neither of which can be discussed without first considering what defines a “customer.” Definition of a customer The approach used to define a customer is critical for successful customer management and is directly correlated to how joint accounts are managed. Definitions may vary by how joint accounts are allocated and used in risk evaluation. It is important to acknowledge: Legal restrictions for data usage related to joint account holders throughout the relationship Impact on predictive model performance and reporting where there are two financially linked individuals with differently assigned exposures Complexities of multiple relationships with customers within the same household – consumer and small business Typical customer definitions used by financial services organizations: Checking account holders: This definition groups together accounts that are “fed” by the same checking account. If an individual holds two checking accounts, then she will be treated as two different and unique customers. Physical persons: Joint accounts allocated to each individual. If Mr. Jones has sole accounts and holds joint accounts with Ms. Smith who also has sole accounts, the joint accounts would be allocated to both Mr. Jones and Ms. Smith. Consistent entities: If Mr Jones has sole accounts and holds joint accounts with Ms. Smith who also has sole accounts, then 3 “customers” are defined: Jones, Jones & Smith, Smith. Financially-linked individuals: Whereas consistent entities are considered three separate customers, financially-linked individuals would be considered one customer: “Mr. Jones & Ms. Smith”. When multiple and complex relationships exist, taking a pragmatic approach to define your customers as financially-linked will lead to a better evaluation of predicted loan performance. Evaluation of credit and default risk Most financial institutions calculate a loan default probability on a periodic basis (monthly) for existing loans, in the format of either a custom behavior score or a generic risk score, supplied by a credit bureau. For new loan requests, financial institutions often calculate an application risk score, sometimes used in conjunction with a credit bureau score, often in a matrix-based decision. This approach is challenging for new credit requests where the presence and nature of the existing relationship is not factored into the decision. In most cases, customers with existing relationships are treated in an identical manner to those new applicants with no relationship – the power and value of the organization’s internal data goes overlooked whereby customer satisfaction and profits suffer as a result. One way to overcome this challenge is to use a Strength of Relationship (SOR) indicator. Strength of Relationship (SOR) indicator The Strength of Relationship (SOR) indicator is a single-digit value used to define the nature of the relationship of the customer with financial institution. Traditional approaches for the assignment of a SOR are based upon the following factors Existence of a primary banking relationship (salary deposits) Number of transactional products held (DDA, credit cards) Volume of transactions Number of loan products held Length of time with bank The SOR has a critical role in the calculation of customer level risk grades and strategies and is used to point us to the data that will be the most predictive for each customer. Typically the stronger the relationship, the more we know about our customer, and the more robust will be predictive models of consumer behavior. The more information we have on our customer, the more our models will lean towards internal data as the primary source. For weaker relationships, internal data may not be robust enough alone to be used to calculate customer level limits and there will be a greater dependency to augment internal data with external third party data (credit bureau attributes.) As such, the SOR can be used as a tool to select the type and frequency of external data purchase. Customer Risk Grade (CRG) A customer-level risk grade or behavior score is a periodic (monthly) statistical assessment of the default risk of an existing customer. This probability uses the assumption that past performance is the best possible indicator of future performance. The predictive model is calibrated to provide the probability (or odds) that an individual will incur a “default” on one or more of their accounts. The customer risk grade requires a common definition of a customer across the enterprise. This is required to establish a methodology for treating joint accounts. A unique customer reference number is assigned to those customers defined as “financially-linked individuals”. Account behavior is aggregated on a monthly basis and this information is subsequently combined with information from savings accounts and third party sources to formulate our customer view. Using historical customer information, the behavior score can accurately differentiate between good and bad credit risk individuals. The behavior score is often translated into a Customer Risk Grade (CRG). The purpose of the CRG is to simplify the behavior score for operational purposes making it easier for noncredit/ risk individuals to interpret a grade more easily than a mathematical probability. Different methods for evaluating credit risk will yield different results and an important aspect in the setting of customer exposure thresholds is the ability to perform analytical tests of different strategies in a controlled environment. In my next post, I’ll dive deeper into adaptive control, champion challenger techniques and strategy design fundamentals. Related content: White paper: Improving decisions across the Customer Life Cycle

Small-business credit conditions improved in Q1 2013, reversing much of the deterioration seen during Q4 2012. The Q1 rise was fueled primarily by falling delinquency rates in every segment compared with a year earlier. The total share of delinquent dollars was 11.2 percent for Q1 2013 - 1.4 percentage points lower than a year ago.

A recent Experian credit trends analysis of new mortgages and bankcards from Q1 2013 shows a 16 percent year-over-year increase in mortgage origination volume and a 20 percent increase in bankcard limits. Providing further evidence of continued economic recovery throughout the nation, mortgage delinquency rates reached multi-year lows and bankcard delinquency rates reached near-record lows.

By: Joel Pruis So we know we need to determine the overall net yield on assets required to cover the cost of funds and the operating expenses but how? In the movie Moneyball, the Oakland A’s develop a strategy to win 99 games by scoring 814 runs and only allowing 645 runs by the opposition. In order to generate the necessary runs, Peter Brand boils down all the stats into one number, on base percentage. By looking at the on-base percentage of all the players in the league, Brand is able to determine the likelihood of generating runs. There are a few key phrases/quotes from this scene that need to be highlighted: “it’s about getting things down to one number” “People are overlooked for a variety of biased reasons and ‘perceived’ flaws.” “Bill James and mathematics cut straight through that [biased reasons and perceived flaws].” Getting things down to one number is the liberating element for the Oakland A’s and for banking. We have already identified the one number for banking – Net Yield on Assets. Let’s define this a bit further though. For this exercise, net yield means the gross yield (interest income plus fee income) on assets less charge offs. We are looking to see what is going to be the consistent return on the assets less what can be expected net charge off related to the assets. When Billy Beane and Peter Brand got it down to the one number “On Base Percentage” it altered the player selection process and highlighted the biases of the scouts such as: Giambi’s brother was “getting a little thick around the waist” “Old Man” Justice Justice will be “lucky if he hits his weight” in July and August Justice’s “legs are gone Hatteberg “can’t throw” Hatteberg’s “best part of his career is over” Hatteberg “walks a lot” None of the above comments used any facts or data to disprove each player’s on base percentage. Can you imagine if they were underwriters or lenders? What type of compliance issues would we have on our hands with the above comments? Biased against disabilities (Hatteberg with nerve damage); Age Discrimination (“Old Man” Justice), Physical Appearance (Giambi’s brother “getting a little thick around the waist”), these scouts would be a compliance liability let alone obstacles in any type of organizational change. But one can readily see how focusing on one number liberates the thinking and removes the old constraints or ways of thinking. One of the scouts commented that Hatteberg had a high on base percentage because he walks a lot, considering a walk as a negative while a hit is a positive but why? Why is getting on base by being walked a negative but getting on base with a hit is positive? The result is the same as the movie points out. How about in commercial lending? If we focus on net yield on the portfolio as the one number, does that do anything to remove biases? I believe that it does. One example is the perception of charge offs in a portfolio. To this day the notion of a charge off in a commercial portfolio, even in the small business portfolio, is frowned upon and can jeopardize one’s career. Similar to the walk, the charge off is not desired but if we focus on the one number, net yield, it actually removes the stigma of the charge off! If we need at minimum a 6% net asset yield and we are able to generate a gross yield of 9% with an expected loss rate of 2%, we actually exceed our “one number” of a targeted net yield of 6% with an expected net yield of 7%. With that change that removes the biases and flawed perception, can we now start to find opportunities that provide us with the ability to step away from the norm; stop competing with the rest; and generate that higher return that is required? What are the potential biases and flawed perceptions that will need to be addressed? “High Risk” Industries? “Undesired” Loan types? Consumer vs. Commercial? Real Estate Secured vs. Unsecured? Loans vs. Treasuries or other earning asset types? But just as in the movie, you need to be prepared for the response you may get from the traditional ‘seasoned’ lenders in your organization. When Billy Beane puts the new strategy into place at the Oakland A’s, the lead scout responds with: “You don’t put a team together with a computer” “Baseball isn’t just numbers, it isn’t science. If it was anybody could do what we do but they can’t.” “They don’t know what we know. They don’t have our experience and they don’t have our intuition.” Ah, just like the traditional baseball scout is the traditional commercial lender with the years of experience, judgment and intuition. I used to be one and used almost word for word the same argument against credit scoring and small business before I truly understood what it was all about. Don’t get me wrong. Experience, judgment and intuition is valuable and necessary. But that type of judgment tends to get into trouble when it stops looking outside for data and only relies on past personal experience to assess the next moves. Experience is always important but it has to continually review, assess and interpret the data. So let’s start looking at the different types of data. On deck – How do we know how many runs the opposition is going to score? The use of external data.

By: Joel Pruis I am going to take some liberties here. Nowhere in the movie Moneyball does Peter Brand tell us how he got to the magic number of winning 99 games to get to the playoffs. My assumption is that given the way that he evaluates the Oakland A’s, he also evaluations the other teams in their conference. Assessing the competitive landscape provides Brand with the estimated runs their opponents will generate. Now we could take the approach that such analysis would correlate to assessing how your competition is going to perform but I am going to take a different approach. I would compare the conference assessment in Moneyball to be similar to an economic forecast/assessment. We need to assess what are the overall conditions in which we must operate that will allow us to generate the net yield on the assets of our financial institution. Some of the things we need to assess to determine what we will be able to generate related to the net yield on assets would be: Gross yield on assets Current interest rate environment (yield on treasuries, federal home loan bank, etc. Interest rate trends (increasing, declining, trends toward fixed rates, variable rates) Industry information General trend of businesses across the nation How are businesses faring? How well are they paying their creditors? Are they relying more or less on credit? Are new businesses being started? Are they succeeding? Are they failing? General trends (same as above) within your financial institution’s market footprint One such source of the industry information is the Small Business Credit Index generated by Experian & Moody’s Analytics. In the recent release of the Small Business Credit Index, small business is indicating stronger from the prior quarter moving from 104.3 to 109. But this is from a national perspective. Depending on your financial institution, it is important to always get an overall view of the economy but more importantly, what is happening in your particular market footprint. Just as the Oakland A’s in Moneyball maintained an overall perspective of Major League Baseball, their focus for success was targeting their specific conference to reach the playoffs. So as we look at information such as the Small Business Credit Index, we are able to see highlights of regional trends (certain states west of the Mississippi are doing better while certain states along the east coast are not) and specific industry trends. From such data we need to drill down into our specific footprint and current portfolio. We need to review such items as: What industry concentrations do we have that are doing well in the economy and how is our portfolio doing compared to the external data? What industries are we not engaging that may provide a good opportunity for our financial institution? What changes are taking place in the general economy that may impact our ability to achieve our expected results? What external factors must we be monitoring that may impact our strategy (such as the impact of Obamacare and how it will impact the hiring for businesses with more than 50 employees?) Just as in Moneyball, Brand continues to monitor the performance of the overall league (and the individual players for future trades), we need to continually monitor the national, state and local economies to determine what adjustments we will need to make to achieve our strategies. So we have assessed the general environment, on to strategies or “How do we win 99 games with a total payroll of $38 million?”
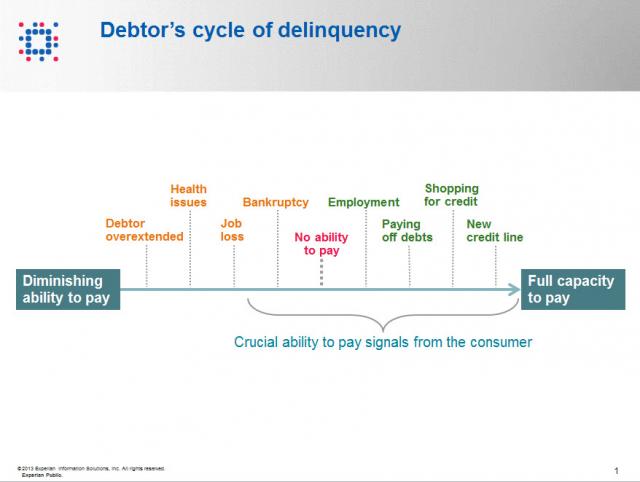
Contact information such as phone numbers and addresses are fundamental to being able to reach a debtor, but knowing when to reach out to the debtor is also a crucial factor impacting success or failure in getting payment. As referenced in the chart below, when a consumer enters the debtor life cycle, they often avoid talking with you about the debt because they do not have the ability to pay. When the debtor begins to recover financially, you want to be sure you are among the first to reach out to them so you can be the first to be paid. According to Don Taylor, President of Automated Collection Services, they have seen a lift of more than 12% of consumers with trigger hits entering repayment, and this on an aged portfolio that has already been actively worked by debt collection staff. Monitoring for a few key changes on the credit profiles of debtors provides the passive monitoring that is needed to tell you the optimal time to reach back to the consumer for payment. Experian compiled several recent collection studies and found that a debtor paying off an account that was previously past due provided a 710% increase in the average payment. Positive improvement on a consumers’ credit profile is one of those vital indicators that the consumer is beginning to recover financially and could have the will—and ability—to pay bad debts. The collection industry is not like the big warehouse stores—quantity and value do not always work hand in hand for the debt collection industry. Targeting the high value credit events that are proven to increase collection amounts is the key to value, and Experian has the expertise, analytics and data to help you collect in the most effective manner. Be sure to check out our other debt collection blog posts to learn how to recover debt more quickly and efficiently.