Tag: fraud risk

Experian’s ninth annual report on identity and fraud highlights persistent worries among consumers and businesses about fraud, including growing threats from GenAI. In this report, we explore how the evolving fraud landscape is impacting identity verification, customer experience, and business priorities for the future. Our 2024 U.S. Identity and Fraud Report draws insights from surveys of over 2,000 U.S. consumers and 200 businesses. This year’s report dives into: Evolving consumer sentiment over security and experience Businesses’ investments to tackle growing fraud challenges Effective technology solutions to accurately identify and authenticate consumers The impact of GenAI on the fraud landscape To keep pace with the evolving landscape, businesses will need to apply a multi-faceted strategy that leverages multiple types of recognition and security to stop all types of fraud while allowing real customers through. To learn more about our findings and perspective, read the full 2024 U.S. Identity and Fraud Report, watch our on-demand webinar, or read the press release. Download Now Watch Webinar Read Press Release

This article was updated on March 4, 2024. If you steal an identity to commit fraud, your success is determined by how long it takes the victim to find out. That window gets shorter as businesses get better at knowing when and how to reach an identity owner when fraud is suspected. In response, frustrated fraudsters have been developing techniques to commit fraud that does not involve a real identity, giving them a longer run-time and a bigger payday. That's the idea behind synthetic identity (SID) fraud — one of the fastest-growing types of fraud. Defining synthetic identity fraud Organizations tend to have different definitions of synthetic identity fraud, as a synthetic identity will look different to the businesses it attacks. Some may see a new account that goes bad immediately, while others might see a longer tenured account fall delinquent and default. The qualifications of the synthetic identity also change over time, as the fraudster works to increase the identity’s appearance of legitimacy. In the end, there is no person to confirm that fraud has occurred, in the very best case, identifying a synthetic identity is inferred and verified. As a result, inconsistent reporting and categorization can make tracking and fighting SID fraud more difficult. To help create a more unified understanding and response to the issue, the Federal Reserve and 12 fraud experts worked together to develop a definition. In 2021, the Boston Federal Reserve published the result, “Synthetic identity fraud is the use of a combination of personally identifiable information to fabricate a person or entity to commit a dishonest act for personal or financial gain."1 To break down the definition, personally identifiable information (PII) can include: Primary PII: Such as a name, date of birth (DOB), Social Security number (SSN) or another government-issued identifier. When combined, these are generally unique to a person or entity. Secondary PII: Such as an address, email, phone number or device ID. These elements can help verify a person or entity's identity. Synthetic identities are created when fraudsters establish an identity from scratch using fake PII. Or they may combine real and fake PII (I.e., a stolen SSN with a fake name and DOB) to create a new identity. Additionally, fraudsters might steal and use someone's SSN to create an identity - children, the elderly and incarcerated people are popular targets because they don't commonly use credit.4 But any losses would still be tied to the SID rather than the victim. Exploring the Impact of SID fraud The most immediate and obvious impact of SID fraud is the fraud losses. Criminals may create a synthetic identity and spend months building up its credit profile, opening accounts and increasing credit limits. The identities and behaviors are constructed to look like legitimate borrowers, with some having a record of on-time payments. But once the fraudster decides to monetize the identity, they can apply for loans and max out credit cards before ‘busting out’ and disappearing with the money. Aite-Novaric Group estimates that SID fraud losses totaled $1.8 billion in 2020 and will increase to $2.94 billion in 2024.2 However, organizations that do not identify SIDs may classify a default as a credit loss rather than a fraud loss. By some estimates, synthetic identity fraud could account for up to 20 percent of loan and credit card charge-offs, meaning the annual charge-off losses in the U.S. could be closer to $11 billion.3 Additionally, organizations lose time and resources on collection efforts if they do not identify the SID fraud. Those estimates are only for unsecured U.S. credit products. But fraudsters use synthetic identities to take out secured loans, including auto loans. As part of schemes used to steal relief funds during the pandemic, criminals used synthetic identities to open demand deposit accounts to receive funds. These accounts can be used to launder money from other sources and commit peer-to-peer payment fraud. Deposit account holders are also a primary source of cross-marketing for some financial institutions. Criminals can take advantage of vulnerable onboarding processes for deposit accounts where there’s low risk to the institution and receive offers for lending products. Building a successful SID prevention strategy Having an effective SID prevention strategy is more crucial than ever for organizations. Aside from fraud losses, consumers listed identity theft as their top concern when conducting activities online. And while 92% of businesses have an identity verification strategy in place, 63% of consumers are "somewhat confident" or "not very confident" in businesses' ability to accurately identify them online. Read: Experian's 2023 Identity and Fraud Report Many traditional fraud models and identity verification methods are not designed to detect fake people. And even a step up to a phone call for verification isn't enough when the fraudster will be the one answering the phone. Criminals also quickly respond when organizations update their fraud detection methods by looking for less-protected targets. Fraudsters have even signed their SIDs up for social media accounts and apps with low verification hurdles to help their SIDs pass identity checks.5 Understand synthetic identity risks across the lifecycle Synthetic Identities are dynamic. When lending criteria is tightened to synthetics from opening new accounts, they simply come back when they can qualify. If waiting brings a higher credit line, they’ll wait. It’s important to recognize that synthetic identity isn’t a new account or a portfolio management problem - it’s both. Use analytics that are tailored to synthetic identity Many of our customers in the financial services space have been trying to solve synthetic identity fraud with credit data. There’s a false sense of security when criteria is tightened and losses go down—but the losses that are being impacted tend to not be related to credit. A better approach to synthetic ID fraud leverages a larger pool of data to assess behaviors and data linkages that are not contained in traditional credit data. You can then escalate suspicious accounts to require additional reviews, such as screening through the Social Security Administration's Electronic Consent Based SSN Verification (eCBSV) system or more stringent document verification. Find a trusted partner Experian's interconnected data and analytics platforms offer lenders turnkey identity and synthetic identity fraud solutions. In addition, lenders can take advantage of the risk management system and continuous monitoring to look for signs of SIDs and fraudulent activity, which is important for flagging accounts after opening. These tools can also help lenders identify and prevent other common forms of fraud, including account takeovers, e-commerce fraud, child identity theft fraud and elderly fraud. Learn more about our synthetic identity fraud solutions. Learn more 1Federal Reserve Bank (2021). Defining Synthetic Identity Fraud 2Aite Novarica (2022). Synthetic Identity Fraud: Solution Providers Shining Light into the Darkness 3Experian (2022). Preventing synthetic identity fraud 4The Federal Reserve (2022). Synthetic Identity Fraud: What Is it and Why You Should Care? 5Experian (2022). Preventing synthetic identity fraud
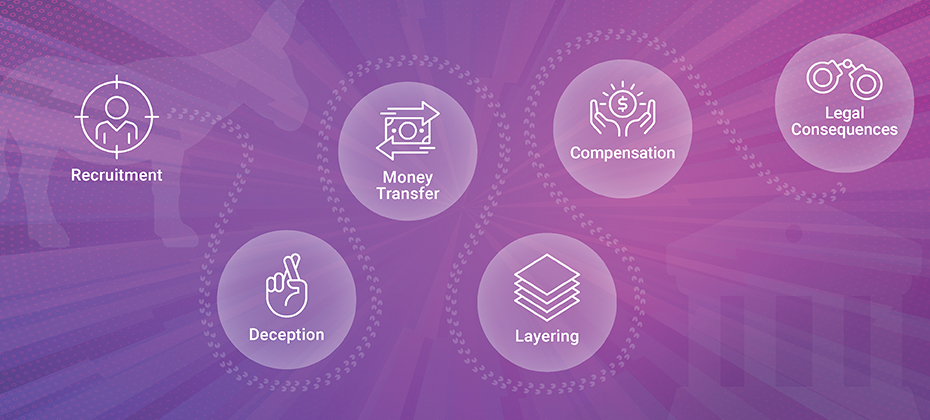
Money mule fraud is a type of financial scam in which criminals exploit individuals, known as money mules, to transfer stolen money or the proceeds of illegal activities. Money mule accounts are becoming increasingly difficult to distinguish from legitimate customers, especially as criminals find new ways to develop hard-to-detect synthetic identities. How money mule fraud typically works: Recruitment: Fraudsters seek out potential money mules through various means, such as online job ads, social media, or email/messaging apps. They will often pose as legitimate employers offering job opportunities promising compensation or claiming to represent charitable organizations. Deception: Once a potential money mule is identified, the fraudsters use persuasive tactics to gain their trust. They may provide seemingly legitimate explanations like claiming the money is for investment purposes, charity donations or for facilitating business transactions. Money Transfer: The mule is instructed to receive funds to their bank or other financial account. The funds are typically transferred from other compromised bank accounts obtained through phishing or hacking. The mule is then instructed to transfer the money to another account, sometimes located overseas. Layering: To mask the origin of funds and make them difficult to trace, fraudsters will employ layering techniques. They may ask the mule to split funds into smaller amounts, make multiple transfers to different accounts, or use various financial platforms such as money services or crypto. Compensation: The money mule is often promised a percentage of transferred funds as payment. However, the promised monies are lower than the dollars transferred, or sometimes the mule receives no payment at all. Legal consequences: Regardless whether mules know they are supporting a criminal enterprise or are unaware, they can face criminal charges. In addition, their personal information could be compromised leading to identity theft and financial loss. How can banks get ahead of the money mule curve: Know your beneficiaries Monitor inbound paymentsEngage identity verification solutionsCreate a “Mule Persona” behavior profileBeware that fraudsters will coach the mule, therefore confirmation of payee is no longer a detection solution Educate your customers to be wary of job offers that seem too good to be true and remain vigilant of requests to receive and transfer money, particularly from unknown individuals and organizations. How financial institutions can mitigate money mule fraud risk When new accounts are opened, a financial institution usually doesn’t have enough information to establish patterns of behavior with newly registered users and devices the way they can with existing users. However, an anti-fraud system should catch a known behavior profile that has been previously identified as malicious. In this situation, the best practice is to compare the new account holder’s behavior against a representative pool of customers, which will analyze things like: Spending behavior compared to the averagePayee profileSequence of actionsNavigation data related to machine-like or bot behaviorAbnormal or risky locationsThe account owner's relations to other users The risk engine needs to be able to collect and score data across all digital channels to allow the financial institution to detect all possible relationships to users, IP addresses and devices that have proven fraud behavior. This includes information about the user, account, location, device, session and payee, among others. If the system notices any unusual changes in the account holder’s personal information, the decision engine will flag it for review. It can then be actively monitored and investigated, if necessary. The benefits of machine learning This is a type of artificial intelligence (AI) that can analyze vast amounts of disparate data across digital channels in real time. Anti-fraud systems based on AI analytics and predictive analytics models have the ability to aggregate and analyze data on multiple levels. This allows a financial institution to instantly detect all possible relationships across users, devices, transactions and channels to more accurately identify fraudulent activity. When suspicious behavior is flagged via a high risk score, the risk engine can then drive a dynamic workflow change to step up security or drive a manual review process. It can then be actively monitored by the fraud prevention team and escalated for investigation. How Experian can help Experian’s fraud prevention solutions incorporate technology, identity-authentication tools and the combination of machine learning analytics with Experian’s proprietary and partner data to return optimal decisions to protect your customers and your business. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call

The rise of the digital channel lead to a rise in new types of fraud – like cryptocurrency and buy now, pay later scams. While the scams themselves are new, they’re based on tried-and-true schemes like account takeover and synthetic identity fraud that organizations have been working to thwart for years, once again driving home the need for a robust fraud solution. While the digital channel is extremely attractive to many consumers due to convenience, it represents a balancing act for organizations – especially those with outdated fraud programs who are at increased risk for fraud. As organizations look for ways to keep themselves and the consumers they serve safe, many turn to fraud risk mitigation. What are fraud risk management strategies? Fraud risk management is the process of identifying, understanding, and responding to fraud risks. Proper fraud risk management strategies involve creating a program that detects and prevents fraudulent activity and reduces the risks associated with fraud. Many fraud risk management strategies are built on five principles: Fraud Risk AssessmentFraud Risk GovernanceFraud PreventionFraud DetectionMonitoring and Reporting By understanding these principles, you can build an effective strategy that meets consumer expectations and protects your business. Fraud risk assessment Fraud protection begins with an understanding of your organization’s vulnerabilities. Review your top risk areas and consider the potential losses you could face. Then look at what controls you currently have in place and how you can dial those up or down to impact both risk and customer experience. Fraud risk governance Fraud risk governance generally takes the form of a program encompassing the structure of rules, practices, and processes that surround fraud risk management. This program should include the fraud risk assessment, the roles and responsibilities of various departments, procedures for fraud events, and the plan for on-going monitoring. Fraud prevention “An ounce of prevention is worth a pound of cure.” This adage certainly rings true when it comes to fraud risk management. Having the right controls and procedures in place can help organizations stop a multitude of fraud types before they even get a foot in the door. Account takeover fraud prevention is an ideal example of how organizations can keep themselves and consumers safe. Fraud detection The only way to stop 100% of fraud is to stop 100% of interactions. Since that’s not a sustainable way to run a business, it’s important to have tools in place to detect fraud that’s already entered your ecosystem so you can stop it before damage occurs. These tools should monitor your systems to look for anomalies and risky behaviors and have a way to flag and report suspicious activity. Monitoring and reporting Once your fraud detection system is in place, you need active monitoring and reporting set up. Some fraud detection tools may include automatic next steps for suspicious activity such as step-up authentication or another risk mitigation technique. In other cases, you’ll need to get a person involved. In these cases it’s critical to have documented procedure and routing in place to ensure that potential fraud is assessed and addressed in a timely fashion. How to implement fraud risk management By adhering to the principles above, you can gain a holistic view of your current risk level, determine where you want your risk level to be, and what changes you’ll need to make to get there. While you might already have some of the necessary tools in place, the right next step is usually finding a trusted partner who can help you review your current state and help you use the right fraud prevention services that fit your risk tolerance and customer experience goals. To learn more about how Experian can help you leverage fraud prevention solutions, visit us or request a call. Learn more

With fraud expected to surge amid uncertain economic conditions, fraudsters are preparing new deception techniques to outsmart businesses and deceive consumers. To help businesses prepare for the coming fraud threats, we created the 2023 Future of Fraud Forecast. Here are the fraud trends we expect to see over the coming year: Fake texts from the boss: Given the prevalence of remote work, there’ll be a sharp rise in employer text fraud where the “boss” texts the employee to buy gift cards, then asks the employee to email the gift card numbers and codes. Beware of fake job postings and mule schemes: With changing economic conditions, fraudsters will create fake remote job postings, specifically designed to lure consumers into applying for the job and providing private details like a social security number or date of birth on a fake employment application. Frankenstein shoppers spell trouble for retailers: Fraudsters can create online shopper profiles using synthetic identities so that the fake shopper’s legitimacy is created to outsmart retailers’ fraud controls. Social media shopping fraud: Social commerce currently has very few identity verification and fraud detection controls in place, making the retailers that sell on these platforms easy targets for fraudulent purchases. Peer-to-peer payment problems: Fraudsters love peer-to-peer payment methods because they’re an instantaneous and irreversible way to move money, enabling fraudsters to get cash with less work and more profit “As fraudsters become more sophisticated and opportunistic, businesses need to proactively integrate the latest technology, data and advanced analytics to mitigate the growing fraud risk,” said Kathleen Peters, Chief Innovation Officer at Experian Decision Analytics in North America. “Experian is committed to continually innovating and bringing solutions to market that help protect consumers and enable businesses to detect and prevent current and future fraud.” To learn more about how to protect your business and customers from rising fraud trends, download the Future of Fraud Forecast and check out Experian’s fraud prevention solutions. Future of Fraud Forecast Press Release

Lately, I’ve been surprised by the emphasis that some fraud prevention practitioners still place on manual fraud reviews and treatment. With the market’s intense focus on real-time decisions and customer experience, it seems that fraud processing isn’t always keeping up with the trends. I’ve been involved in several lively discussions on this topic. On one side of the argument sit the analytical experts who are incredibly good at distilling mountains of detailed information into the most accurate fraud risk prediction possible. Their work is intended to relieve users from the burden of scrutinizing all of that data. On the other side of the argument sits the human side of the debate. Their position is that only a human being is able to balance the complexity of judging risk with the sensitivity of handling a potential customer. All of this has led me to consider the pros and cons of manual fraud reviews. The Pros of Manual Review When we consider the requirements for review, it certainly seems that there could be a strong case for using a manual process rather than artificial intelligence. Human beings can bring knowledge and experience that is outside of the data that an analytical decision can see. Knowing what type of product or service the customer is asking for and whether or not it’s attractive to criminals leaps to mind. Or perhaps the customer is part of a small community where they’re known to the institution through other types of relationships—like a credit union with a community- or employer-based field of membership. In cases like these, there are valuable insights that come from the reviewer’s knowledge of the world outside of the data that’s available for analytics. The Cons of Manual Review When we look at the cons of manual fraud review, there’s a lot to consider. First, the costs can be high. This goes beyond the dollars paid to people who handle the review to the good customers that are lost because of delays and friction that occurs as part of the review process. In a past webinar, we asked approximately 150 practitioners how often an application flagged for identity discrepancies resulted in that application being abandoned. Half of the audience indicated that more than 50% of those customers were lost. Another 30% didn’t know what the impact was. Those potentially good customers were lost because the manual review process took too long. Additionally, the results are subjective. Two reviewers with different levels of skill and expertise could look at the same information and choose a different course of action or make a different decision. A single reviewer can be inconsistent, too—especially if they’re expected to meet productivity measures. Finally, manual fraud review doesn’t support policy development. In another webinar earlier this year, a fraud prevention practitioner mentioned that her organization’s past reliance on manual review left them unable to review fraud cases and figure out how the criminals were able to succeed. Her organization simply couldn’t recreate the reviewer’s thought process and find the mistake that lead to a fraud loss. To Review or Not to Review? With compelling arguments on both sides, what is the best practice for manually reviewing cases of fraud risk? Hopefully, the following list will help: DO: Get comfortable with what analytics tell you. Analytics divide events into groups that share a measurable level of fraud risk. Use the analytics to define different tiers of risk and assign each tier to a set of next steps. Start simple, breaking the accounts that need scrutiny into high, medium and low risk groups. Perhaps the high risk group includes one instance of fraud out of every five cases. Have a plan for how these will be handled. You might require additional identity documentation that would be hard for a criminal to falsify or some other action. Another group might include one instance in every 20 cases. A less burdensome treatment can be used here – like a one-time-passcode (OTP) sent to a confirmed mobile number. Any cases that remain unverified might then be asked for the same verification you used on the high-risk group. DON’T: Rely on a single analytical score threshold or risk indicator to create one giant pile of work that has to be sorted out manually. This approach usually results in a poor experience for a large number of customers, and a strong possibility that the next steps are not aligned to the level of risk. DO: Reserve manual review for situations where the reviewer can bring some new information or knowledge to the cases they review. DON’T: Use the same underlying data that generated the analytics as the basis of a review. Consider two simplistic cases that use a new address with no past association to the individual. In one case, there are several other people with different surnames that have recently been using the same address. In the other, there are only two, and they share the same surname. In the best possible case, the reviewer recognizes how the other information affects the risk, and they duplicate what the analytics have already done – flagging the first application as suspicious. In other cases, connections will be missed, resulting in a costly mistake. In real situations, automated reviews are able to compare each piece of information to thousands of others, making it more likely that second-guessing the analytics using the same data will be problematic. DO: Focus your most experienced and talented reviewers on creating fraud strategies. The best way to use their time and skill is to create a cycle where risk groups are defined (using analytics), a verification treatment is prescribed and used consistently, and the results are measured. With this approach, the outcome of every case is the result of deliberate action. When fraud occurs, it’s either because the case was miscategorized and received treatment that was too easy to discourage the criminal—or it was categorized correctly and the treatment wasn’t challenging enough. Gaining Value While there is a middle ground where manual review and skill can be a force-multiplier for strong analytics, my sense is that many organizations aren’t getting the best value from their most talented fraud practitioners. To improve this, businesses can start by understanding how analytics can help group customers based on levels of risk—not just one group but a few—where the number of good vs. fraudulent cases are understood. Decide how you want to handle each of those groups and reserve challenging treatments for the riskiest groups while applying easier treatments when the number of good customers per fraud attempt is very high. Set up a consistent waterfall process where customers either successfully verify, cascade to a more challenging treatment, or abandon the process. Focus your manual efforts on monitoring the process you’ve put in place. Start collecting data that shows you how both good and bad cases flow through the process. Know what types of challenges the bad guys are outsmarting so you can route them to challenges that they won’t beat so easily. Most importantly, have a plan and be consistent. Be sure to keep an eye out for a new post where we’ll talk about how this analytical approach can also help you grow your business. Contact us

Recently, I wrote about how Experian is assisting NASWA (National Association of State Workforce Agencies) with identity verification to help mitigate the spike in fraudulent unemployment insurance claims. Because of this I was not all that surprised when I found a letter in my mailbox from the Texas Workforce Commission with a fraudulent claim using my identity, inspiring me to follow up on this topic with a focus on fraud prevention best practices. Identity theft is on the rise According to Experian data analysis and a recent study on unemployment insurance fraud, at least 25% of new claims are a result of identity theft. This is 50 times higher than what we have traditionally seen in the highest ID theft fraud use case, new credit card applications, which generally amounts to less than 0.5% of new applications. Increasing digitization of the last few years—culminating in the huge leap forward in 2020—has resulted in a massive amount of information available online. Of that information, a reported 1.03 billion records were exposed between 2016 and 2020. There are currently approximately 330 million Americans, so on average more than three records per person have been exposed, creating an environment ripe for identity theft. In fact, a complete identity consisting of name, address, date of birth, and Social Security number (SSN) can be purchased for as little as $8. This stolen data is then often leveraged by both criminal rings who are able to perpetrate fraud on a large scale and smaller scale opportunists – like the ones in Riverside, CA leveraging access to identities of prison inmates. Fraud prevention through layered identity controls In the 20 years that I have been combatting ID theft both in the private and public sectors, I’ve learned that the most effective identity proofing goes beyond traditional identity resolution, validation, and verification. To be successful, you must take advantage of all available data and incorporate it into a layered and risk-based approach that utilizes device details, user behavior, biometrics, and more. Below, I outline three key layers to design an effective process for ID proofing new unemployment insurance claims. Layer 1: Resolve and Validate Identities Traditional identity data consists of the same basic information—name, address, date of birth, telephone number, and SSN—which is now readily available to fraudsters. These have been the foundation for ID proofing in the past and are still critical to resolving the identity in question. The key is to also include additional identity elements like email address and phone number to gain a more holistic view of the applicant. Layer 2: Assess Fraud Risk Determining an identity belongs to a real-life subject is not sufficient to mitigate the risk of ID theft associated with a new unemployment insurance claim. You must go beyond identity validation to assess the risk associated with their claim. Risk assessment risk falls into two categories – identity and digital risk. Identity Risk When assessing a claim, it’s important to check the identity for: Velocity: How often have you (or other states) seen the information being presented with this application? Has the information been associated with multiple identities? Recency of change: How long has the identity been associated with the contact information (phone, email, address, etc.)? Red flags: Has the subject been a recent victim of ID theft, or are they reported as deceased? Synthetic Identity: Are there signs that the identity itself is fictitious or manipulated and does not belong to a real-life person? Digital Risk Similar to the identity risk layer above, the device itself and how the subject interacts with the device are significantly important in identifying the likelihood a new claim is fraudulent. Device risk can be assessed by utilizing geolocation and checking for inconsistent settings or high-risk browsers, while behavioral risk might check for mouse movement, typing speed, or screen pressure. Layer 3: Verify Highest Risk Subjects The final stage in this process is to require additional verification for the highest risk claims, which helps to balance the experience of your valid subjects while minimizing the impact of fraud. Additional steps might include: Document verification: Scanning a government-issued ID (driver’s license, passport, or similar), which includes assessing for document security features and biometric comparison to the applicant. One-time passcode (OTP): It is key to deploy this sparingly only to phone numbers that have been associated with the subject for a significant time frame and incorporate checks to determine if it is at high risk (e.g., recently ported or forwarded). Knowledge-based verification (KBV): Leveraging non-public information from a variety of sources. By adding additional, context-based identity elements, it becomes possible to improve the three main objectives of most agencies’ identity proofing process – get good constituents through the first time, protect the agency and citizens from fraud, and deliver a smooth and secure customer experience in online channels. While there’s no quick fix to prevent unemployment insurance fraud, a layered identity strategy can help prevent it. Finding a partner that has a single, holistic solution empowers agencies to defend against unemployment insurance fraud while minimizing friction for the end-user, and preparing for future fraud schemes. To learn more about how you can protect your constituents and your agency from unemployment insurance fraud request a call today. Contact us

Previously, we discussed the risks of account takeover and how a Defense in Depth strategy can protect your business. Before implementation it’s important to understand the financial benefits of the strategy. There are a few key steps to assessing and quantifying the value of Defense in Depth. Transaction risk assessment: This requires taking inventory of all possible transactions. Session-level risk analysis: With the transactions categorized by risk level, the next step is to review session history based on the highest risk activity within the session. Quantify the cost of a challenge: There are multiple costs associated with challenging a user using step-up authentication. Consider both direct and indirect costs – failure rate, contact center operational cost, and attrition rate following failed challenges (consider lifetime value of account) Quantify the expected challenge rate: This can be done by comparing the Defense in Depth approach to a traditional approach. Below is a calculator that will help determine the cost of the reduced challenges associated with a Defense in Depth strategy versus a traditional strategy. initIframe('5f039d2e4c508b1b0aafa4bd'); In addition to the quantitative benefits, it is important to consider some of the qualitative benefits of this approach: Challenging at moments that matter: Customers appreciate and expect protection in online banking, especially when moving money externally or updating contact information. This is a great way to achieve both convenience and security. Improved fraud management: By staging the risk decision at the transaction level, the business can balance the type of challenge with the transaction risk. There are incremental cost considerations to include in the business case as well. For instance, there is an increase in transaction calls for a risk assessment at the medium/high risk transactions – about 10% in the example above. Generally, the increased transaction cost is more than offset by the reduction in cost of challenges alone. A Defense in Depth strategy can help businesses manage fraud risk and prevent account takeover in online banking without sacrificing user experience. If you are interested in assistance with building your business case and understanding the strategies to implement a successful Defense in Depth strategy, contact us today. Contact us 1Identity Fraud in the Digital Age, Javelin Strategy & Research, September 2020

This is the second of a three part series of blog posts highlighting key focus areas for your response to the COVID-19 health crisis: Risk, Operations, Consumer Behavior, and Reporting and Compliance. For more information and the latest resources, please visit Look Ahead 2020, Experian’s COVID-19 resource center with the latest news and tools for our business partners as well as links to consumer resources and a risk simulator. To read the introductory post, click here. Strategic Focus on Risk The last recession spurred an industry-wide systemic focus on stressed scenario forecasting. Now’s the time to evaluate the medium- to long-term impacts of the downturn response on portfolio risk measurement. The impact will be wide ranging, requiring recalibration of scorecards and underwriting processes and challenging assumptions related to fees, net interest income, losses, expenses and liquidity. There are critical inputs to understand portfolio monitoring and benchmarking by account types and segments. Higher unemployment across the country is likely. You need a thorough response to successfully navigate the emerging risks. Expanding credit line management efforts for existing accounts is critical. Proactively responding to the needs of your customers will demand a wide range of data and analytics and more frequent and active processes to take action. Current approaches and tools with increased automation may need to be reevaluated. When sudden economic shocks occur, statistical models may still rank-order effectively, while the odds-to-score relationships deteriorate. This is the time to take full advantage of explainable machine learning techniques to quickly calibrate or rebuild scorecards with refreshed data (traditional and alternative) and continue the learning cycle. As your risk management tools are evaluated and refreshed, there are many opportunities to target your servicing strategies where they can produce results. This may take the form of identifying segments exhibiting financial stress that can benefit from deferred payments, loan consolidation or refinancing. It might also involve more typical risk mitigation strategies, such as credit line reduction. There are several scenarios that may emerge over the next nine to 12 months that can offer opportunities to deepen relationships with your customers while managing long-term risk exposure. Optimizing Business Operations One of the most significant impacts to your business is the increase in transaction volumes as a result of the economic shock. We expect material increases in collections, refinancing and hardship programs. These increases are arriving at a time when many businesses have streamlined their teams in concert with periods of low delinquency and credit losses. Additional strain from call center shutdowns and limited staffing can easily overwhelm operations and cause business continuity plans to breakdown. More than ever, the use of digital channels and self-servicing technology are no longer nice-to-haves. Customers expect online access, and efficiency demands automation, including virtual assistants. As more volume migrates to these channels, it’s critical to have the right customer experience and fraud risk controls deployed through flexible, cloud-based systems. Learn More

This is the introduction to a series of blog posts highlighting key focus areas for your response to the COVID-19 health crisis: Risk, Operations, Consumer Behavior, and Reporting and Compliance. For more information and the latest resources, please visit Look Ahead 2020, Experian's COVID-19 resource center with the latest news and tools for our business partners as well as links to consumer resources and a risk simulator. Responding to COVID-19 The response to COVID-19 is rolling out across the global financial system and here in North America. Together, we’re adapting to working remotely and adjusting to our “new normal.” It seems the long forecasted economic recession is finally and abruptly on our doorstep. Recession planning has been a focus for many organizations, and it’s now time to act on these contingency plans and respond to the downturn. The immediate effects and those that quickly follow the pandemic will widely impact the economy, affecting businesses of all sizes, employment and consumer confidence. We learned from the housing crisis and Great Recession how to identify and adapt to emerging risks. We can apply those skills while rebuilding the economy and focusing on the consumer. How should you respond? What strategies should you deploy? How can you balance emerging risks, changing consumer expectations and regulatory impacts? First, let's draw upon the best knowledge we gained from the last recession and apply those learnings. Second, we need to understand the current environment including the impact of major changes in technology and consumer behavior over the last few years. This approach will allow us to identify key themes to help build-out strategies to focus resources, respond successfully and deliver for stakeholders. Anticipate the pervasive and highly impactful market dynamics and trends The impact of this downturn on the consumer, on businesses and on financial institutions will be very different to that of the Great Recession. There will be a complete loss of income for many workers and small businesses. In a survey conducted by the Center for Financial Services Innovation (CFSI), more than 112 million Americans said that they don’t have enough savings to cover three months of living expenses*. These volatile market conditions and consumer insecurity will cause changes to your business models. You must prepare to manage increased fraud attacks, continue to push toward digital banking and understand regulatory changes. Learn More *U.S. Financial Health Pulse, 2018 Baseline Survey Results. https://s3.amazonaws.com/cfsi-innovation-files-2018/ wp-content/uploads/2018/11/20213012/Pulse-2018- Baseline-Survey-Results-11-16.18.pdf

Last month, Kenneth Blanco, Director of the Financial Crimes Enforcement Network, warned that cybercriminals are stealing data from fintech platforms to create synthetic identities and commit fraud. These actions, in turn, are alleged to be responsible for exploiting fintech platforms’ integration with other financial institutions, putting banks and consumers at risk. According to Blanco, “by using stolen data to create fraudulent accounts on fintech platforms, cybercriminals can exploit the platforms’ integration with various financial services to initiate seemingly legitimate financial activity while creating a degree of separation from traditional fraud detection efforts.” Fintech executives were quick to respond, and while agreeing that synthetic IDs are a problem, they pushed back on the notion that cybercriminals specifically target fintech platforms. Innovation and technology have indeed opened new doors of possibility for financial institutions, however, the question remains as to whether it has also created an opportunity for criminals to implement more sophisticated fraud strategies. Currently, there appears to be little evidence pointing to an acute vulnerability of fintech firms, but one thing can be said for certain: synthetic ID fraud is the fastest-growing financial crime in the United States. Perhaps, in part, because it can be difficult to detect. Synthetic ID is a type of fraud carried out by criminals that have created fictitious identities. Truly savvy fraudsters can make these identities nearly indistinguishable from real ones. According to Kathleen Peters, Experian’s SVP, Head of Fraud and Identity, it typically takes fraudsters 12 to 18 months to create and nurture a synthetic identity before it’s ready to “bust out” – the act of building a credit history with the intent of maxing out all available credit and eventually disappearing. These types of fraud attacks are concerning to any company’s bottom line. Experian’s 2019 Global Fraud and Identity Report further details the financial impact of fraud, noting that 55% of businesses globally reported an increase in fraud-related losses over the past 12 months. Given the significant risk factor, organizations across the board need to make meaningful investments in fraud prevention strategies. In many circumstances, the pace of fraud is so fast that by the time organizations implement solutions, the shelf life may already be old. To stay ahead of fraudsters, companies must be proactive about future-proofing their fraud strategies and toolkits. And the advantage that many fintech companies have is their aptitude for being nimble and propensity for early adoption. Experian can help too. Our Synthetic Fraud Risk Level Indicator helps both fintechs and traditional financial institutions in identifying applicants likely to be associated with a synthetic identity based on a complex set of relationships and account conditions over time. This indicator is now available in our credit report, allowing organizations to reduce exposure to identity fraud through early detection. To learn more about Experian’s Synthetic Fraud Risk Level Indicator click here, or visit experian.com/fintech.

Although half of businesses globally report an increase in fraud management over the past 12 months, many still experience fraud losses and attacks. To help address these challenges, Experian held its first-ever Fintech Fraud & Identity Meetup on February 5 in San Francisco, Calif. The half-day event was aimed at offering insights on the main business drivers of fraud, market trends, challenges and technology advancements that impact identity management and fraud risk strategy operations. “We understand the digital landscape is changing – inevitably, with technology enhancements come increased fraud risk for businesses operating in the online space,” said Jon Bailey, Experian’s Vice President of Fintech. “Our focus today is on fraud and identity, and providing our fintech customers with the tools and insights needed to grow and thrive.” The meetup was attended by number of large fintech companies with services spanning across a broad spectrum of fintech offerings. To kick off the event, Tony Hadley, Experian’s Senior Vice President of Government & Regulatory Affairs, provided an update on the latest regulatory news and trends impacting data and the fintech space. Next followed a fraud and identity expert panel, which engaged seasoned professionals in an in-depth discussion around two main themes 1) fraud trends and risk mitigation; and 2) customer experience, convenience, and trust. Expert panelists included: David Britton, Experian’s Vice President of Industry Solutions; Travis Jarae, One World Identity’s Founder & CEO; George Kurtyka, Joust’s Co-Founder & COO; and Filip Verley, Airbnb’s Product Manager. “The pace of fraud is so fast, by the time companies implement solutions, the shelf-life may already be old,” Britton said. “That is the crux – how to stay ahead. The goal is to future-proof your fraud strategy and capabilities.” At the close of the expert panel, Kathleen Peters, Experian’s Senior Vice President Head of Fraud and Identity, demoed Experian’s CrossCore™ solution – the first smart, open, plug-and-play platform for fraud and identity services. Peters began by stating, “Fraud is constant. Over 60% of businesses report an increase in fraud-related losses over the past year, with the US leading the greatest level of concern. The best way to mitigate risk is to create a layered approach; that’s why Experian invented CrossCore.” With the sophistication of fraudsters, it’s no surprise that many businesses are not confident with the effectiveness of their fraud strategy. Learn more about how you can stay one step ahead of fraudsters and position yourself for success in the ever-changing fraud landscape; download Experian’s 2019 Global Identity and Fraud Report here. For an inside look at Experian’s Fintech Fraud & Identity Meetup, watch our video below.

Identity-related fraud exposure and losses are increasing, and the underlying schemes are becoming more complex. To make better decisions on the need for step-up authentication in this dynamic environment, you should take a layered approach to the services you need. Some of these services include: Identity verification and reverification checks for ongoing reaffirmation of your customer identity data quality and accuracy. Targeted identity risk scores and underlying attributes designed to isolate identity theft, first-party fraud and synthetic identity. Layered, passive or more active authentication, such as document verification, biometrics, knowledge-based authentication and alternate data sources. Bad guys are more motivated, and they’re getting better at identity theft and synthetic identity attacks. Fraud prevention needs to advance as well. Future-proof your investments. More fraud prevention strategies to consider>

Turns out, Americans still don’t know much about CyberSecurity. That’s according to new research from the Pew Data Center, which conducted a cybersecurity knowledge quiz. The 13 question quiz was designed to test American’s knowledge on a number of cybersecurity issues and terms. A majority of online adults can identify a strong password and recognize the dangers of using public Wi-Fi. However, many struggle with more technical cybersecurity concepts, such as how to identify true two-factor authentication or determine if a webpage they are using is encrypted. As we in the industry know, cybersecurity is a complicated and diverse subject, but given the pervasiveness of news around cybersecurity, I was still a little surprised by the lack of knowledge. The typical (median) respondent answered only five of the 13 questions correctly (with a mean of 5.5 correct answers). 20% answered more than eight questions accurately, and just 1% received a “perfect score” by correctly answering all 13 questions. The study showed that public knowledge of cybersecurity is low on some relatively technical issues, like identifying the correct example of multi-factor authentication, understanding how VPNs minimize risk and knowing what a botnet is. On the flip side, the two questions that the majority of respondents answered correctly included identifying the strongest password from a list of four options and understanding that public Wi-Fi networks have risk even when they are password protected. Given the median scores, I was proud of missing only one question – guess I have more reading to do on Botnets. As an industry, it is our duty to not only create systems and securities to improve the tactical effectiveness of fraud prevention, but to educate consumers on many of these topics as well. They often are the first line of defense in stopping fraud and reducing the threat of breaches.

Experian is recognized as a leading security solution provider for fraud and identity solutions in order to protect customers and financial institutions