Topics

Data quality should be a priority for retailers at any time of the year, but even more so as the holiday season approaches. According to recent research from Experian, organizations feel that, on average, 25 percent of their data is inaccurate and 12 percent of departmental budgets are wasted due to inaccuracies in contact data. During the 2013 holiday season, consumer spending is expected to increase by at least 11 percent. Retailers need to improve data quality early on in order to ensure that relevant holiday offers reach consumers and to take advantage of the expected increase in consumer spending. View our recent Webinar: Unique insights on consumer credit trends and the impact of consumer behavior on the economic recovery Source: View our data quality infographic: ’Twas the month before the holidays

The credit appetite for small businesses is strong and growing. Total outstanding balances have risen at their fastest rate in two years, and delinquency rates have fallen at a consistent pace. Only 10 percent of outstanding small-business credit balances were past-due in Q3 — the lowest level of delinquency seen since the recovery began. While this is an encouraging sign, it is important to note that these improvements have come at the cost of hiring new employees and investments. Sign up for the Quarterly Business Credit Review Webinar on Dec. 10 Source: Download the full Experian/Moody’s Analytics Small Business Credit Index report.

Credit trends from the most recent Experian–Oliver Wyman Market Intelligence Report point to a steady economic recovery. Bankcard charge-offs decreased 13 percent year over year (4.5 percent versus 3.9 percent) and delinquent dollars for the 90–180 day past due delinquencies decreased 17.5 percent for the same timeframe (1.6 percent to 1.3 percent). These trends are a positive sign for overall economic recovery and evidence that the current growth in bankcard originations is not coming at the expense of increased delinquencies. Sign up to attend our upcoming Webinar on Q3 credit trends and take a closer look at the impact of consumer behavior on the economic recovery. Source: Data for this article was sourced from Experian’s IntelliViewSM, a Web-based data query, analysis and reporting tool.

In the 1970s, it took an average of 18 days before a decision could be made on a credit card application. Credit decisioning has come a long way since then, and today, we have the ability to make decisions faster than it takes to ring up a customer in person at the point of sale. Enabling real-time credit decisions helps retail and online merchants lay a platform for customer loyalty while incentivizing an increased customer basket size. While the benefits are clear, customers still are required to be at predetermined endpoints, such as: At the receiving end of a prescreened credit offer in the mail At a merchant point of sale applying for retail credit In front of a personal computer The trends clearly show that customers are moving away from these predetermined touch-points where they are finding mailed credit offers antiquated, spending even less time at a retail point of sale versus preferring to shop online and exchanging personal computers for tablets and smartphones. Despite remaining under 6 percent of retail spending, e-commerce sales for Q2 2013 have reportedly been up 18.5 percent from Q2 2012, representing the largest year-over-year increase since Q4 2007, before the 2008 financial crisis. Fueled by a shift from personal computers to connected devices and a continuing growth in maturity of e-commerce and m-commerce platforms, this trend is only expected to grow stronger in the future. To reflect this shift, marketers need to be asking themselves how they should apportion their budgets and energies to digital while executing broader marketing strategies that also may include traditional channels. Generally, traditional card acquisitions methods have failed to respond to these behavioral shifts, and, as a whole, retail banking was unprepared to handle the disintermediation of traditional products in favor of the convenience mobile offers. Now that the world of banking is finding its feet in the mobile space, accessibility to credit must also adapt to be on the customer’s terms, unencumbered by historical notions around customer and credit risk. Download this white paper to learn how credit and retail private-label issuers can provide an optimal customer experience in emerging channels such as mobile without sacrificing risk mitigation strategies — leading to increased conversions and satisfied customers. It will demonstrate strategies employed by credit and retail private-label issuers who already have made the shift from paper and point of sale to digital, and it provides recommendations that can be used as a business case and/or a road map.

Credit unions were the only type of lender to have their 30 day plus delinquency rate fall below 2 percent for several key product categories. The table below provides the delinquency rate by lender and product. 30 day plus delinquency rate Q2 2013 Auto* Mortgage Bankcard Credit unions 1.52% 1.36% 1.99% Banks 2.01% 4.91% 2.73% Captive auto 2.40% N/A N/A Sign up to attend our upcoming Webinar on Q3 credit trends and take a closer look at the impact of consumer behavior on the economic recovery. Source : Data for this article was sourced from IntelliViewSM, a Web-based data query, analysis and reporting tool. *Auto delinquency rate includes automotive loans and leases.

Personalized credit education can have a measurable impact on a person’s credit score. Consumers who used a personalized consumer credit-education service that offers one-on-one guidance and score simulation improved their average VantageScore® credit score by 21 points (684 to 705) and decreased their credit utilization by 15 percent. Download our recent Webinar: It's a new reality ... and time for a new risk score VantageScore® is a registered trademark of VantageScore Solutions, LLC.

The growing cost and number of data breaches has spurred more interest in cyber insurance. While companies often increase investments in technology and training programs to reduce the likelihood of a breach, a recent Ponemon Institute survey of risk-management professionals found that 31 percent of companies surveyed have cyber insurance and 39 percent plan to purchase cyber insurance in the future. Learn how to outline your response plan with our data breach response guide. Source: Managing Cyber Security as a Business Risk: Cyber Insurance in the Digital Age

By: Zach Smith On September 13, the Consumer Financial Protection Bureau (CFPB) announced final amendments to the mortgage rules that it issued earlier this year. The CFPB first issued the final mortgage rules in January 2013 and then released subsequent amendments in June. The final amendments also make some additional clarifications and revisions in response to concerns raised by stakeholders. The final modifications announced by the CFPB in September include: Amending the prohibition on certain servicing activities during the first 120 days of a delinquency to allow the delivery of certain notices required under state law that may provide beneficial information about legal aid, counseling, or other resources. Detailing the procedures that servicers should follow when they fail to identify or inform a borrower about missing information from loss mitigation applications, as well as revisions to simplify the offer of short-term forbearance plans to borrowers suffering temporary hardships. Clarifying best practices for informing borrowers about the address for error resolution documents. Exempting all small creditors, including those not operating predominantly in rural or underserved areas, from the ban on high-cost mortgages featuring balloon payments. This exemption will continue for the next two years while the CFPB re-examines the definitions of “rural” and “underserved.” Explaining the "financing” of credit insurance premiums to make clear that premiums are considered to be “financed” when a lender allows payments to be deferred past the month in which it’s due. Clarifying the circumstances when a bank’s teller or other administrative staff is considered to be a “loan originator” and the instances when manufactured housing employees may be classified as an originator under the rules. Clarifying and revising the definition of points and fees for purposes of the qualified mortgage cap on points and fees and the high-cost mortgage points and fees threshold. Revising effective dates of many loan originator compensation rules from January 10, 2014 to January 1, 2014. While the industry continues to advocate for an extension of the effective date to provide additional time to implement the necessary compliance requirements, the CFPB insists that both lenders and mortgage servicers have had ample time to comply with the rules. Most recently, in testimony before the House Financial Services Committee, CFPB Director Richard Cordray stated that “most of the institutions have told us that they will be in compliance” and he didn’t foresee further delays. Related Research Experian's Global Consulting Practice released a recent white paper, CCAR: Getting to the Real Objective, that suggests how banks, reviewers and examiners can best actively manage CCAR's objectives with a clear dual strategy that includes both short-term and longer-term goals for stress-testing, modeling and system improvements. Download the paper to understand how CCAR is not a redundant set of regulatory compliance exercices; its effects on risk management include some demanding paradigm shifts from traditional approaches. The paper also reviews the macroeconomic facts around the Great Recession revealing some useful insights for bank extreme-risk scenario development, econometric modeling and stress simulations. Related Posts Where Business Models Worked, and Didn't, and Are Most Needed Now in Mortgages Now That the CFPB Has Arrived, What's First on It's Agenda Can the CFPB Bring Debt Collection Laws into the 21st Centrury

Billions of dollars are being issued in fraudulent refunds at the state and federal level. Most of the fraud can be categorized around identity theft. An example of this type of fraud may include fraudsters acquiring the Personal Identifying Information (PII) from a deceased individual, buying it from someone not filing or otherwise stealing it from legitimate sources like a doctor’s office. The PII is then used to fill out tax returns, add fraudulent income information and request bogus deductions. Additional forms of tax refund fraud may include: Direct consumer tax refund fraud using real PII of US Citizens to file fraudulent tax returns and claim bogus deductions thereby increasing refund amounts EITC (Earned Income Tax Credit)/ACC (Additional Childcare Credit) fraud which is usually perpetrated with the assistance of a tax preparer and claiming improper cash payments and/or deductions for non-existent children. Tax Preparer Fraud where tax preparers purposefully submit false information on tax returns or file false returns for clients. Under reporting of income on tax filings. Taking multiple Homestead Exemptions for tax credit. Since this Fraud more often occurs as an early filing using Fraudulent or stolen PII the individual consumer is at risk for long term Identity issues. Exacerbating the tax refund fraud problem: The majority of returns that request refunds are now filed online (83% of all federal filings in 2012 were online) -if you file online, there is no need to submit a W-2 form with that online filing. If your employment information cannot be pulled into the forms by your tax software you can fill it in manually. The accuracy of information regarding employer and wage information for which deductions are based, is only verified after the refund is issued. Refunds directly deposited - filers now have the option to have their refunds deposited into a bank account for faster receipt. Once these funds are deposited and withdrawn there is no way to trace where the funds have gone. Refunds provided on debit cards – filers can request their refund in the form of a debit card. This is an even bigger problem than bank account deposits because once issued, there is no way to trace who uses a debit card and for what purpose. So what do you need to look for when reviewing tax fraud prevention tools? Look for a provider that has experience in working with state and federal government agencies. Proven expertise in this domain is critical, and experience here means that the provider has cleared the disciplined review process that the government requires for businesses they do business with. Look for providers with relevant certifications for authentication services, such as the Kantara Identity Assurance Framework for levels of identity assurance. Look for providers that can authenticate users by verifying the device they’re using to access your applications. With over 80% of tax filings occurring online, it is critical that any identity proofing strategy also allows for the capability to verify the source or device used to access these applications. Since tax fraudsters don’t limit their use of stolen IDs to tax fraud and may also use them to perpetrate other financial crimes such as opening lines of credit – you need to be looking at all avenues of fraudulent activity If fraud is detected and stopped, consider using a provider that can offer post fraud mitigation processes for your customers/potential victims. Getting tax refunds and other government benefits into the right hands of their recipients is important to everyone involved. Since tax refund fraud detection is a moving target, it’s buyer beware if you hitch your detection efforts to a provider that has not proven their expertise in this unique space.

According to a recent Experian analysis of Q2 2013 bankcard trends, bankcard origination volumes increased 21% year-over-year equating to a $12 billion increase in new bankcard limits. The increase was largely driven by the prime and near-prime segments which made up the majority of the $12 billion increase. Download our recent Webinar: It's a new reality...and time for a new risk score.
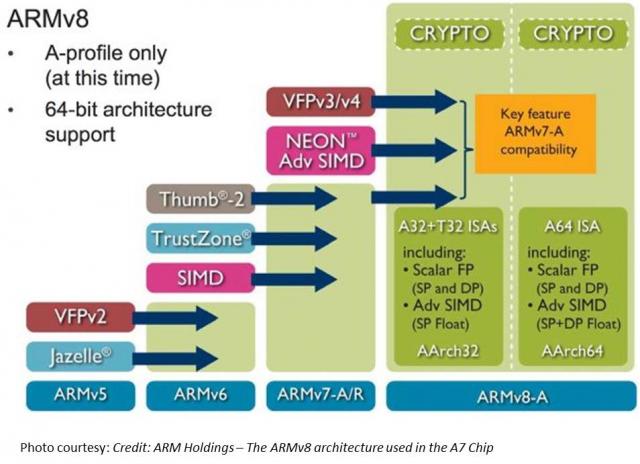
TL;DR Read within as to how Touch ID is made possible via ARM’s TrustZone/TEE, and why this matters in the context of the coming Apple’s identity framework. Also I explain why primary/co-processor combos are here to stay. I believe that eventually, Touch ID has a payments angle – but focusing on e-commerce before retail. Carriers will weep over a lost opportunity while through Touch ID, we have front row seats to Apple’s enterprise strategy, its payment strategy and beyond all – the future direction of its computing platform. I had shared my take on a possible Apple Biometric solution during the Jan of this year based on its Authentec acquisition. I came pretty close, except for the suggestion that NFC is likely to be included. (Sigh.) Its a bit early to play fast and loose with Apple predictions, but its Authentec acquisition should rear its head sometime in the near future (2013 – considering Apple’s manufacturing lead times), that a biometric solution packaged neatly with an NFC chip and secure element could address three factors that has held back customer adoption of biometrics: Ubiquity of readers, Issues around secure local storage and retrieval of biometric data, Standardization in accessing and communicating said data. An on-chip secure solution to store biometric data – in the phone’s secure element can address qualms around a central database of biometric data open to all sorts of malicious attacks. Standard methods to store and retrieve credentials stored in the SE will apply here as well. Why didn’t Apple open up Touch ID to third party dev? Apple expects a short bumpy climb ahead for Touch ID before it stabilizes, as early users begin to use it. By keeping its use limited to authenticating to the device, and to iTunes – it can tightly control the potential issues as they arise. If Touch ID launched with third party apps and were buggy, it’s likely that customers will be confused where to report issues and who to blame. That’s not to say that it won’t open up Touch ID outside of Apple. I believe it will provide fettered access based on the type of app and the type of action that follows user authentication. Banking, Payment, Productivity, Social sharing and Shopping apps should come first. Your fart apps? Probably never. Apple could also allow users to set their preferences (for app categories, based on user’s current location etc.) such that biometrics is how one authenticates for transactions with risk vs not requiring it. If you are at home and buying an app for a buck – don’t ask to authenticate. But if you were initiating a money transfer – then you would. Even better – pair biometrics with your pin for better security. Chip and Pin? So passé. Digital Signatures, iPads and the DRM 2.0: It won’t be long before an iPad shows up in the wild sporting Touch ID. And with Blackberry’s much awaited and celebrated demise in the enterprise, Apple will be waiting on the sidelines – now with capabilities that allow digital signatures to become ubiquitous and simple – on email, contracts or anything worth putting a signature on. Apple has already made its iWork productivity apps(Pages, Numbers, Keynote), iMovie and iPhoto free for new iOS devices activated w/ iOS7. Apple, with a core fan base that includes photographers, designers and other creative types, can now further enable iPads and iPhones to become content creation devices, with the ability to attribute any digital content back to its creator by a set of biometric keys. Imagine a new way to digitally create and sign content, to freely share, without worrying about attribution. Further Apple’s existing DRM frameworks are strengthened with the ability to tag digital content that you download with your own set of biometric keys. Forget disallowing sharing content – Apple now has a way to create a secondary marketplace for its customers to resell or loan digital content, and drive incremental revenue for itself and content owners. Conclaves blowing smoke: In a day and age where we forego the device for storing credentials – whether it be due to convenience or ease of implementation – Apple opted for an on-device answer for where to store user’s biometric keys. There is a reason why it opted to do so – other than the obvious brouhaha that would have resulted if it chose to store these keys on the cloud. Keys inside the device. Signed content on the cloud. Best of both worlds. Biometric keys need to be held locally, so that authentication requires no roundtrip and therefore imposes no latency. Apple would have chosen local storage (ARM’s SecurCore) as a matter of customer experience, and what would happen if the customer was out-of-pocket with no internet access. There is also the obvious question that a centralized biometric keystore will be on the crosshairs of every malicious entity. By decentralizing it, Apple made it infinitely more difficult to scale an attack or potential vulnerability. More than the A7, the trojan in Apple’s announcement was the M7 chip – referred to as the motion co-processor. I believe the M7 chip does more than just measuring motion data. M7 – A security co-processor? I am positing that Apple is using ARM’s TrustZone foundation and it may be using the A7 or the new M7 co-processor for storing these keys and handling the secure backend processing required. Horace Dediu of Asymco had called to question why Apple had opted for M7 and suggested that it may have a yet un-stated use. I believe M7 is not just a motion co-processor, it is also a security co-processor. I am guessing M7 is based on the Cortex-M series processors and offloads much of this secure backend logic from the primary A7 processor and it may be that the keys themselves are likely to be stored here on M7. The Cortex-M4 chip has capabilities that sound very similar to what Apple announced around M7 – such as very low power chip, that is built to integrate sensor output and wake up only when something interesting happens. We should know soon. This type of combo – splitting functions to be offloaded to different cores, allows each cores to focus on the function that it’s supposed to performed. I suspect Android will not be far behind in its adoption, where each core focuses on one or more specific layers of the Android software stack. Back at Google I/O 2013, it had announced 3 new APIs (the Fused location provider) that enables location tracking without the traditional heavy battery consumption. Looks to me that Android decoupled it so that we will see processor cores that focus on these functions specifically – soon. I am fairly confident that Apple has opted for ARM’s Trustzone/TEE. Implementation details of the Trustzone are proprietary and therefore not public. Apple could have made revisions to the A7 chip spec and could have co-opted its own. But using the Trustzone/TEE and SecurCore allows Apple to adopt existing standards around accessing and communicating biometric data. Apple is fully aware of the need to mature iOS as a trusted enterprise computing platform – to address the lack of low-end x86 devices that has a hardware security platform tech. And this is a significant step towards that future. What does Touch ID mean to Payments? Apple plans for Touch ID kicks off with iTunes purchase authorizations. Beyond that, as iTunes continue to grow in to a media store behemoth – Touch ID has the potential to drive fraud risk down for Apple – and to further allow it to drive down risk as it batches up payment transactions to reduce interchange exposure. It’s quite likely that à la Walmart, Apple has negotiated rate reductions – but now they can assume more risk on the front-end because they are able to vouch for the authenticity of these transactions. As they say – customer can longer claim the fifth on those late-night weekend drunken purchase binges. Along with payment aggregation, or via iTunes gift cards – Apple has now another mechanism to reduce its interchange and risk exposure. Now – imagine if Apple were to extend this capability beyond iTunes purchases – and allow app developers to process in-app purchases of physical goods or real-world experiences through iTunes in return for better blended rates? (instead of Paypal’s 4% + $0.30). Heck, Apple can opt for short-term lending if they are able to effectively answer the question of identity – as they can with Touch ID. It’s Paypal’s ‘Bill Me Later’ on steroids. Effectively, a company like Apple who has seriously toyed with the idea of a Software-SIM and a “real-time wireless provider marketplace” where carriers bid against each other to provide you voice, messaging and data access for the day – and your phone picks the most optimal carrier, how far is that notion from picking the cheapest rate across networks for funneling your payment transactions? Based on the level of authentication provided or other known attributes – such as merchant type, location, fraud risk, customer payment history – iTunes can select across a variety of payment options to pick the one that is optimal for the app developer and for itself. And finally, who had the most to lose with Apple’s Touch ID? Carriers. I wrote about this before as well, here’s what I wrote then (edited for brevity): Does it mean that Carriers have no meaningful role to play in commerce? Au contraire. They do. But its around fraud and authentication. Its around Identity. … But they seem to be stuck imitating Google in figuring out a play at the front end of the purchase funnel, to become a consumer brand(Isis). The last thing they want to do is leave it to Apple to figure out the “Identity management” question, which the latter seems best equipped to answer by way of scale, the control it exerts in the ecosystem, its vertical integration strategy that allows it to fold in biometrics meaningfully in to its lineup, and to start with its own services to offer customer value. So there had to have been much ‘weeping and moaning and gnashing of the teeth’ on the Carrier fronts with this launch. Carriers have been so focused on carving out a place in payments, that they lost track of what’s important – that once you have solved authentication, payments is nothing but accounting. I didn’t say that. Ross Anderson of Kansas City Fed did. What about NFC? I don’t have a bloody clue. Maybe iPhone6? iPhone This is a re-post from Cherian's original blog post "Smoke is rising from Apple's Conclave"

According to data from Experian's IntelliViewSM, Iowa residents carry the lowest average credit card balance per consumer in the U.S. with an average balance of $2,904, as of the second quarter of 2013. On the other end of the spectrum, the state with the highest average credit card balance is Alaska, where residents carry an average credit card balance of $4,706. New Jersey citizens are close behind with an average balance of $4,523.

By: Matt Sifferlen I recently read interesting articles on the Knowledge@Wharton and CNNMoney sites covering the land grab that's taking place among financial services startups that are trying to use a consumer's social media activity and data to make lending decisions. Each of these companies are looking at ways to take the mountains of social media data that sites such as Twitter, Facebook, and LinkedIn generate in order to create new and improved algorithms that will help lenders target potential creditworthy individuals. What are they looking at specifically? Some criteria could be: History of typing in ALL CAPS or all lower case letters Frequent usage of inappropriate comments Number of senior level connections on LinkedIn The quantity of posts containing cats or annoying self-portraits (aka "selfies") Okay, I made that last one up. The point is that these companies are scouring through the data that individuals are creating on social sites and trying to find useful ways to slice and dice it in order to evaluate and target consumers better. On the consumer banking side of the house, there are benefits for tracking down individuals for marketing and collections purposes. A simple search could yield a person's Facebook, Twitter, or LinkedIn profile. The behaviorial information can then be leveraged as a part of more targeted multi-channel and contact strategies. On the commercial banking side, utilizing social site info can help to supplement any traditional underwriting practices. Reviewing the history of a company's reviews on Yelp or Angie's List could share some insight into how a business is perceived and reveal whether there is any meaningful trend in the level of negative feedback being posted or potential growth outlook of the company. There are some challenges involved with leveraging social media data for these purposes. 1. Easily manipulated information 2. Irrelevant information that doesn't represent actual likes, thoughts or relevant behaviors 3. Regulations From a Fraud perspective, most online information can easily and frequently be manipulated which can create a constantly moving target for these providers to monitor and link to the right customer. Fake Facebook and Twitter pages, false connections and referrals on LinkedIn, and fabricated positive online reviews of a business can all be accomplished in a matter of minutes. And commercial fraudsters are likely creating false business social media accounts today for shelf company fraud schemes that they plan on hatching months or years down the road. As B2B review websites continue to make it easier to get customers signed up to use their services, the downside is there will be even more unusable information being created since there are less and less hurdles for commercial fraudsters to clear, particularly for sites that offer their services for free. For now, the larger lenders are more likely to utilize alternative data sources that are third party validated, like rent and utility payment histories, while continuing to rely on tools that can prevent against fraud schemes. It will be interesting to see what new credit and non credit data will be utilized as a common practice in the future as lenders continue their efforts to find more useful data to power their credit and marketing decisions.
By: Joel Pruis As we go through the economic seasons, we need to remember to reassess our strategy. While we use data as the way to accurately assess the environment and determine the best course of action for your future strategy, the one thing that is for certain is that the current environment will definitely change. Aspects that we did not anticipate will develop, trends may start to slow or change direction. Moneyball continues to be a movie that gives us some great examples. We see that Billy Beane and Peter Brand were constantly looking at their position and making adjustments to the team’s roster. Even before they made any significant adjustments, Beane and Brand found themselves justifying their strategy to the owner (even though the primary issue was with the head coach not playing the roster that maximized the team’s probability of winning). The first aspect that worked against the strategy was the head coach and while we could go down a tangent about cultural battles within an organization, let's focus on how Beane adjusted. Beane simply traded the players the head coach preferred to play forcing the use of players preferred by Beane and Brand. Later we see Beane and Brand making final adjustments to the roster by negotiating trades resulting in the Oakland A’s landing Ricardo Rincon. The change in the league that allowed such a trade was that Rincon’s team was not doing well and the timing allowed the A’s to execute the trade. Beane adjusted with the changes in the league. One thing to note, is that he changed the roster while the team was doing well. They were winning but Beane made adjustments to continue maximizing the team’s potential. Too often we adjust when things are going poorly and do not adjust when we seem to be hitting our targets. Overall, we need to continually assess what has changed in our environment and determine what new challenges or new opportunities these changes present. I encourage you to regularly assess what is happening in your local economy. High-level national trends are constantly on the front page of the news but we need to drill down to see what is happening in a specific market area being served. As Billy Beane did with the Oakland A’s throughout the season, I challenge you to assess your current strategies and execution against what is happening in your market territory. Related posts: How Financial Institutions can assess the overall conditions for generating the net yield on the assets How to create decision strategies for small business lending Upcoming Webinar: Learn about the current state of small business, the economy and how it applies to you

After reaching post-recession lows in June, the July S&P/Experian Consumer Credit Default Indices showed that default rates increased slightly in several categories. While the national composite,* first mortgage and auto loan default rates all increased, the bankcard default rate continued to decline and hit a new low of 3.22%.